Defense area type optical fiber disturbance periphery security and protection system and quick invasion disturbance judgment method
A security system and zone-type technology, applied in anti-theft alarms, instruments, alarms, etc., can solve the problems of high false alarm rate, small monitoring range of perimeter security systems, and high power consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0050] Embodiment 1: Defense Zone Type Optical Fiber Disturbance Perimeter Security System Based on Michelson Optical Fiber Interference Principle
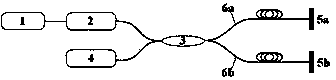
[0051] Such as figure 2 As shown, the system includes multiple defense zones, and each defense zone has an independent sensing optical path, a central control identification module, a communication and an alarm module, and a computer connected to each defense zone, wherein:
[0052] Sensing optical path part based on optical fiber interference principle: Michelson or M-Z optical fiber interference principle is used to generate interference signals and monitor external signals in real time; the specific structure of the optical path is: the optical signal emitted by laser 1 is input to 2╳2 coupler 3 through isolator 2 One input port, the two output ports of the 2╳2 coupler are respectively connected to the first sensing fiber F1-6a and the second sensing fiber F2-6b, the first sensing fiber F1 and the second sensing fiber F2 Th...
Embodiment 2
[0058] Embodiment 2, a method for quickly and efficiently judging whether there is an intrusion disturbance
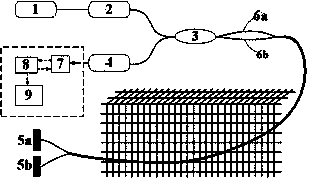
[0059] Such as figure 2 As shown, the light emitted by the light source passes through the 2╳2 couplers in each defense zone and is divided into two identical lights. When there is disturbance outside, the two beams of light will have different phase shifts. After the detector is converted into an electrical signal, it is sent to the central control identification module for data processing. The data processing parameters in the central control identification module are adjusted through the communication and alarm modules. Once it is judged that there is an intrusion signal, an alarm message is sent immediately.
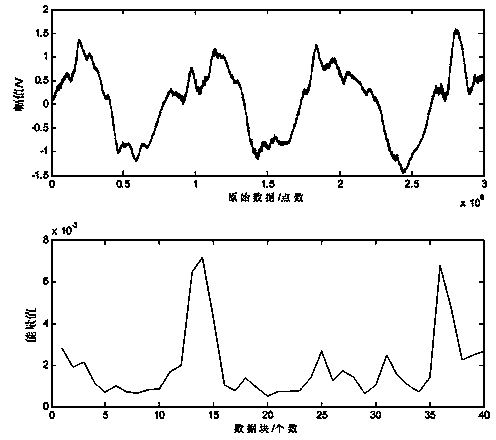
[0060] The following pairs figure 2 The system shown, combined with Figure 5 The flow of the judgment method, using an example to illustrate the judgment process:
[0061] 1. The order of the all-phase filter is set to 64, and the number of channels i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com