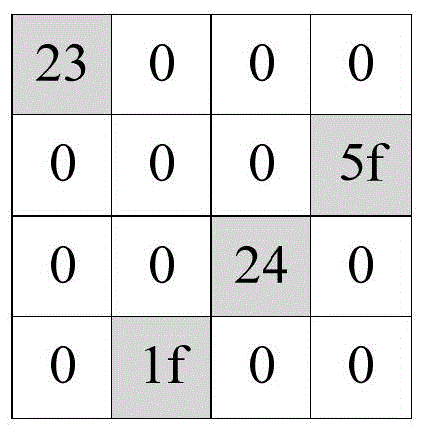Security testing method and system
A technology of security testing and testing modules, applied in the field of information security, can solve the problems of time-consuming and laborious sampling and testing of cryptographic chips, complex observation and control registers, and not batch testing, etc., to achieve strong usability and practicability, high degree of automation, The effect of small area overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
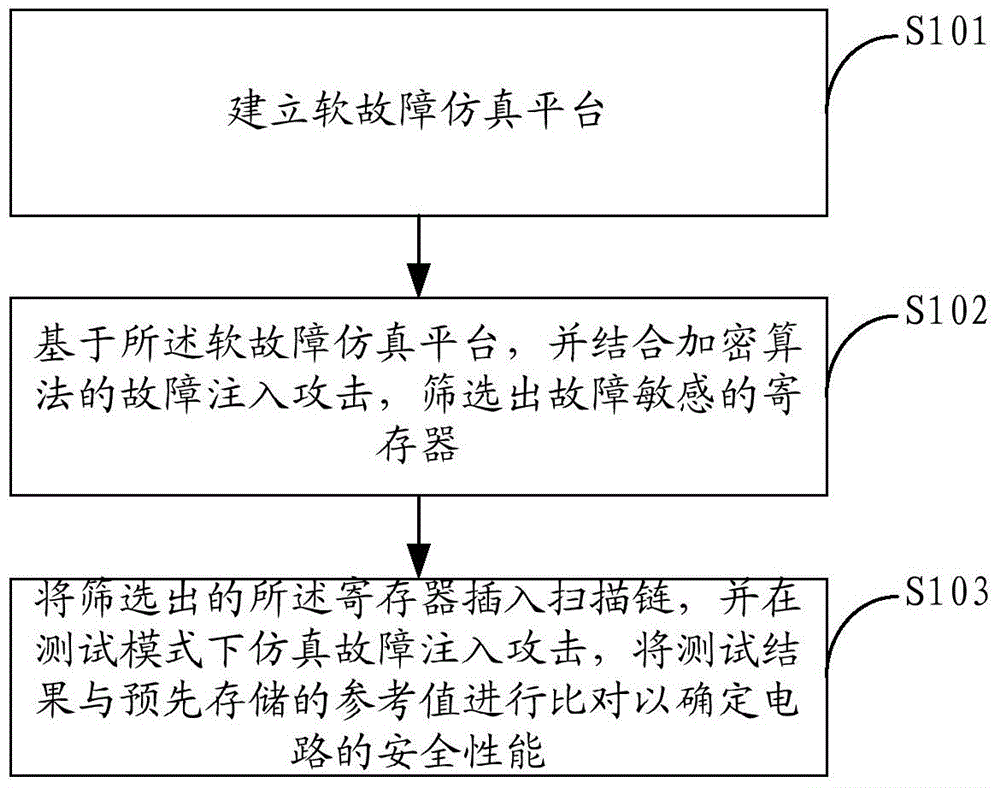
[0026] figure 1 The implementation flow of the security testing method provided by Embodiment 1 of the present invention is shown, and the process of the method is described in detail as follows:
[0027] In step S101, a soft fault simulation platform is established.
[0028] In the embodiment of the present invention, in order to filter out the sensitive registers used for inserting the scan chain, a soft fault test simulation platform is built through SynopsysVCS software and Perl script.
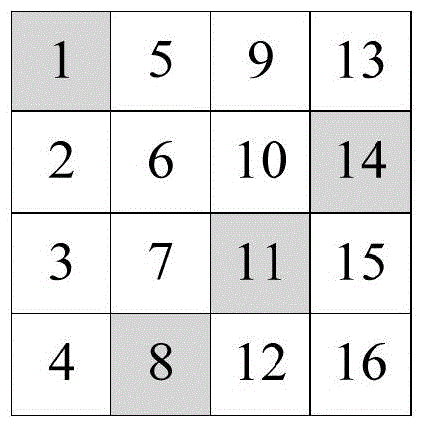
[0029] In step S102 , based on the soft fault simulation platform, combined with the fault injection attack of the encryption algorithm, the fault-sensitive registers are screened out.
[0030] Specifically, as shown in Figure 2:
[0031] Step 1. Select multiple sets of random input values for the gate-level netlist, and perform circuit encryption simulation to obtain the simulation output value;
[0032] Step 2. assigning the simulation output value to a reference value;
[0033] S...
Embodiment 2
[0067] Figure 5 The composition structure of the safety test system provided by the second embodiment of the present invention is shown, and for the convenience of description, only the parts related to the embodiment of the present invention are shown.
[0068] The security testing system can be a software unit, a hardware unit, or a combination of software and hardware built into terminal equipment (such as personal computers, laptops, tablet computers, smart phones, etc.), or integrated into terminal equipment as an independent pendant or In the application system of the terminal equipment.
[0069] The safety testing system includes:
[0070] The simulation platform establishment unit 51 is used to establish a soft fault simulation platform;
[0071] The register screening unit 52 is used to screen out fault-sensitive registers based on the soft fault simulation platform and in combination with the fault injection attack of the encryption algorithm;
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com