Access control system, client and access control identity authentication method
An identity verification method and access control system technology, applied in the field of access control security, can solve the problems of low recognition rate and low processing efficiency, and achieve the effect of solving the problem of low recognition rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
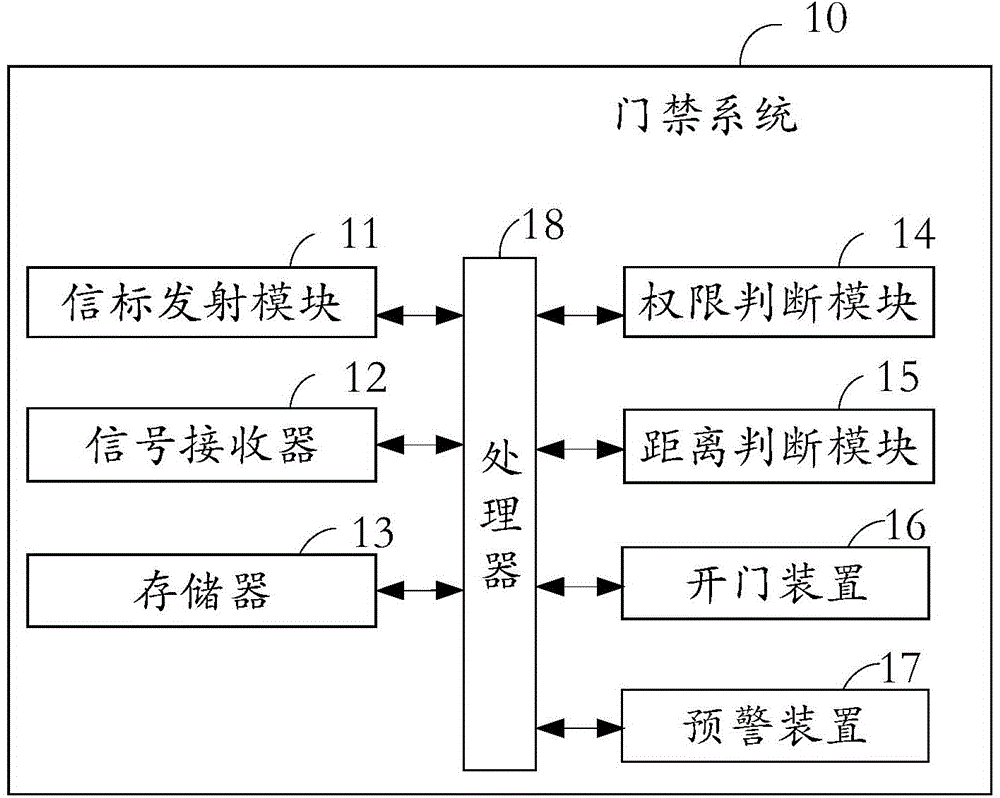
[0037] see figure 2 , which is a schematic diagram of the modules of the access control system in the embodiment of the present invention. The access control system 10 includes: a beacon transmitting module 11 , a signal receiver 12 , a memory 13 , an authority judging module 14 , a distance judging module 15 , a door opening device 16 , an early warning device 17 and a processor 18 .
[0038] The beacon transmitting module 11 is configured to transmit a beacon broadcast to wake up the client to send a short distance communication signal.
[0039] It can be understood that: the beacon broadcast includes a beacon ID, which is used to wake up the client matching the beacon ID. Usually, the broadcast range of the beacon transmitting module is about 50 meters, which may deviate according to the geographical environment, but it is enough to support the access control function in the present invention.
[0040] The signal receiver 12 is used to receive the near-field communicatio...
Embodiment 2
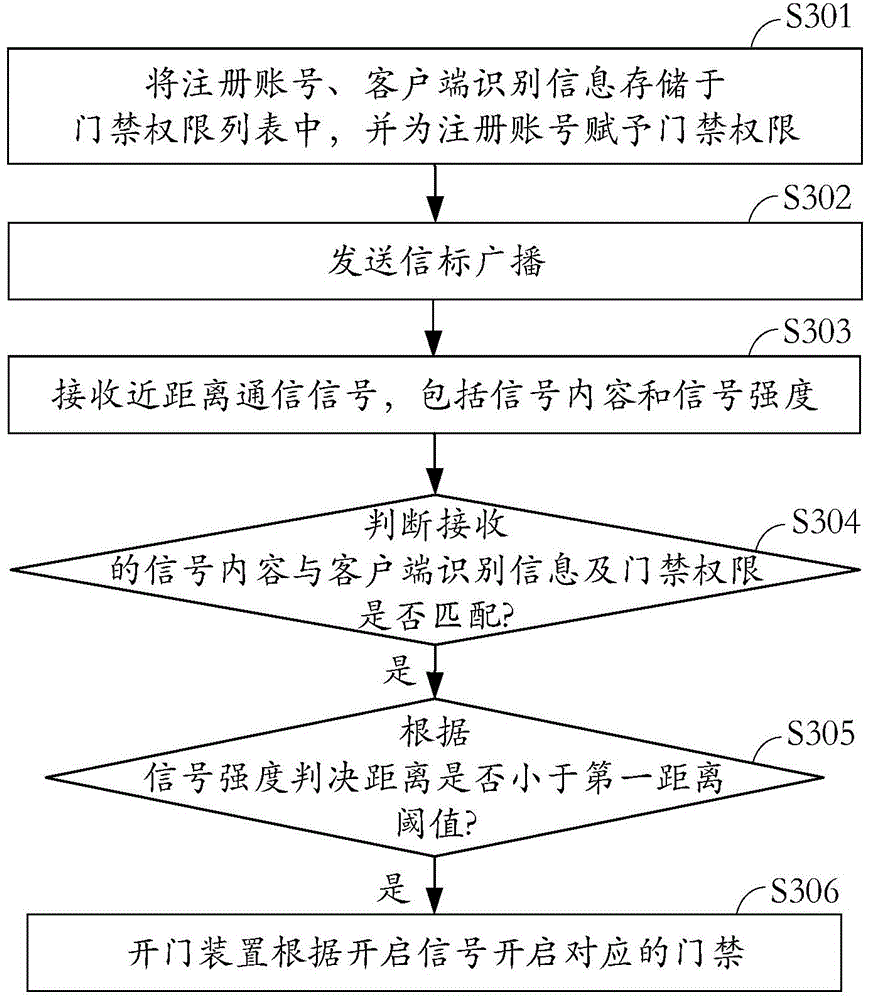
[0071] see image 3 , which is a schematic flowchart of an identity verification method for access control in an embodiment of the present invention. In short, divided by function includes two parts: registration, access control.
[0072] Registration section, including:
[0073] In step S301, the registered account number and client identification information are stored in the access control authority list, and the access control authority is assigned to the registered account number.
[0074] It can be understood that: the registered account is used to confirm whether it has the authority to modify the client identification information in the access control authority list, usually one of employee ID + employee name, employee name + password, or employee ID + password One or other combination of information that contains employee information that is not readily available through heuristics.
[0075] In the access control permission list, the permission to add rows and modi...
Embodiment 3
[0093] see Figure 4 , which is a schematic diagram of the workflow of the access control system in the embodiment of the present invention. In short, it includes four parts by function: registration, access control, attendance, and early warning.
[0094] Registration section, including:
[0095] In step S401, the registered account number and client identification information are stored in the access control authority list, and the access control authority is assigned to the registered account number.
[0096] It can be understood that: the registered account is used to confirm whether it has the authority to modify the client identification information in the access control authority list, usually one of employee ID + employee name, employee name + password, or employee ID + password One or other combination of information that contains employee information that is not readily available through heuristics.
[0097] In the access control permission list, the permission to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com