User behavior anomaly detection system and method based on principal component analysis
A principal component analysis, anomaly detection technology, applied in the computer field, can solve the problems of long running time, long system response time, complex process design, etc., to achieve the effect of increasing detection efficiency, effective detection results, and easy implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] An embodiment of the present invention will be described in detail below in conjunction with the accompanying drawings.
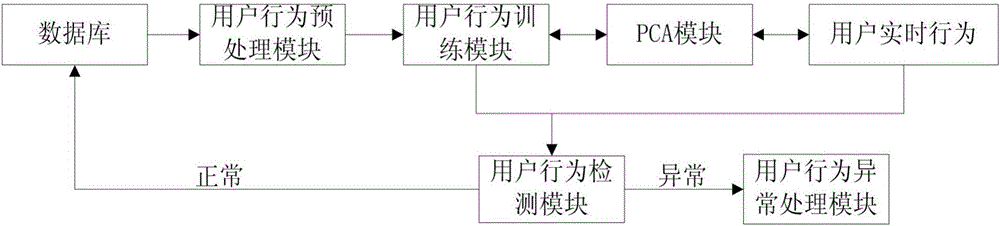
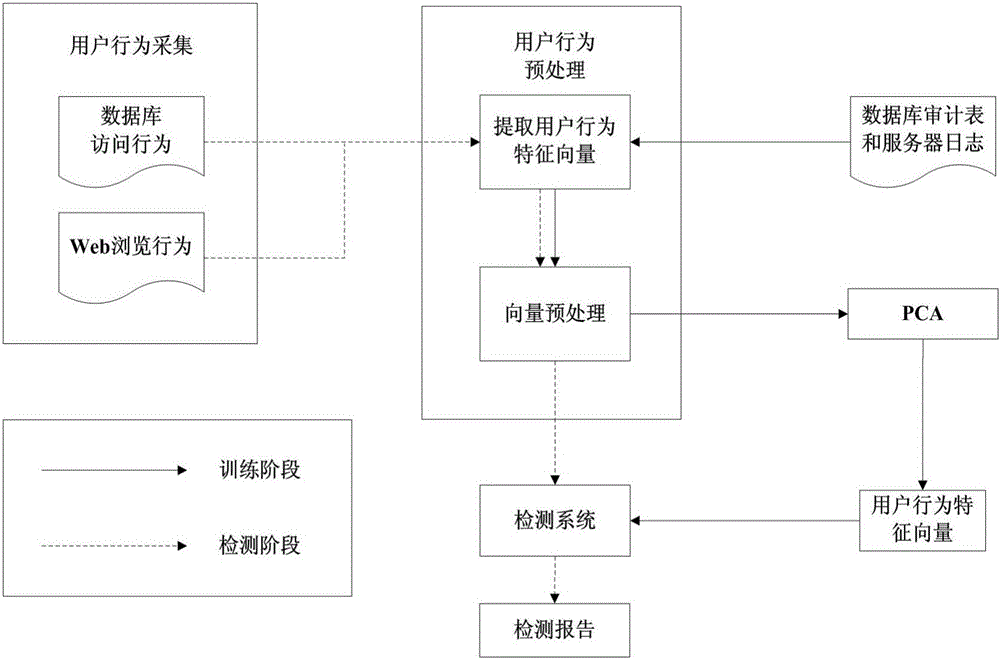
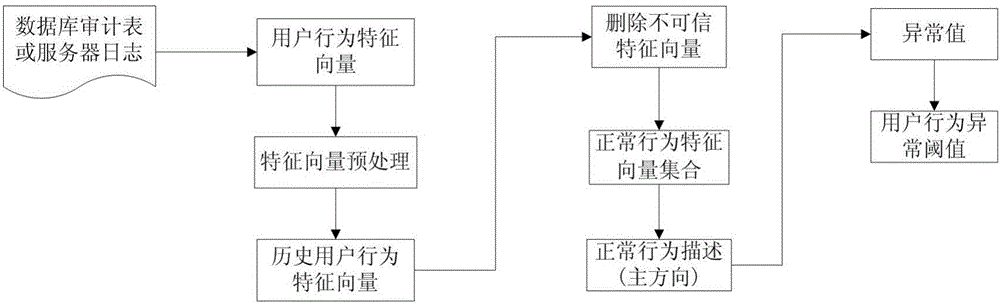
[0057] A user behavior anomaly detection system based on principal component analysis: the user behavior includes two types: user database access behavior and user Web server access behavior; user behavior elements in each type of user behavior include: when user behavior is database When accessing behavior, the user behavior element includes the name of the data table accessed by the user, the user access time, the primary key in the user access table, the original data accessed by the user, and the data changed by the user; when the user behavior is a web server access behavior, the user behavior element includes the user The object of the access request to the web server and the time interval between adjacent access requests.
[0058] Such as figure 1 As shown, the system includes the following modules:
[0059] The user behavior preprocessing m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com