On-chip power supply network verification method for side channel attack
A power supply network and side-channel attack technology, which is applied to electrical components, encryption devices with shift registers/memory, digital transmission systems, etc., can solve the problems of high cost, inability to verify chip anti-attack capabilities, low accuracy, etc. problems, to achieve the effect of low cost, improved coverage, and improved accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
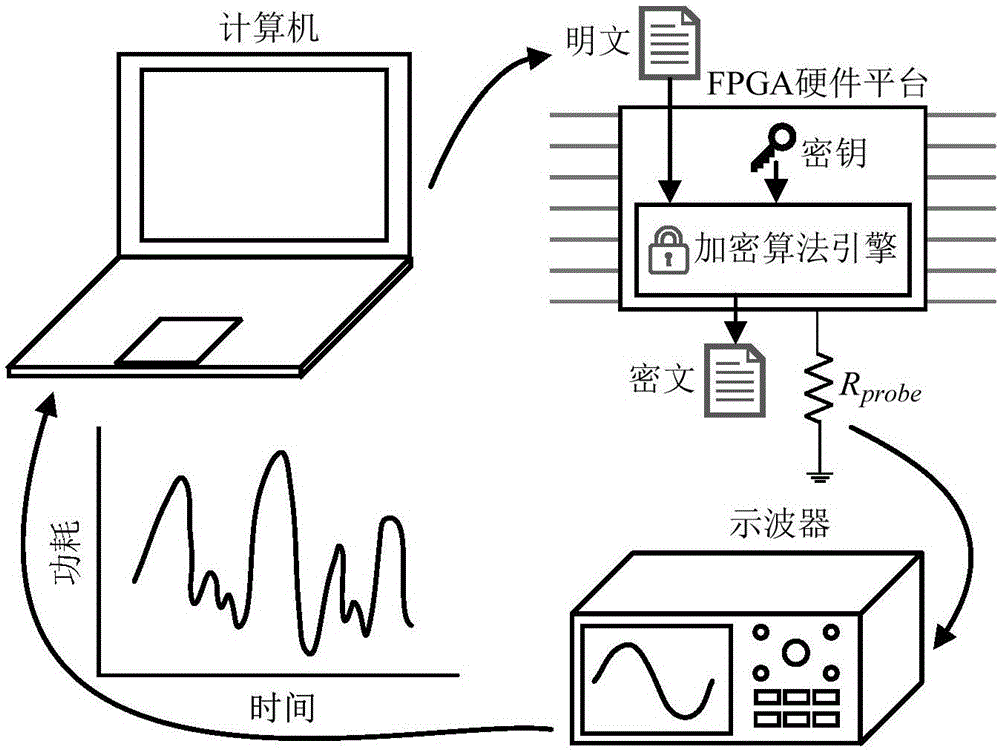
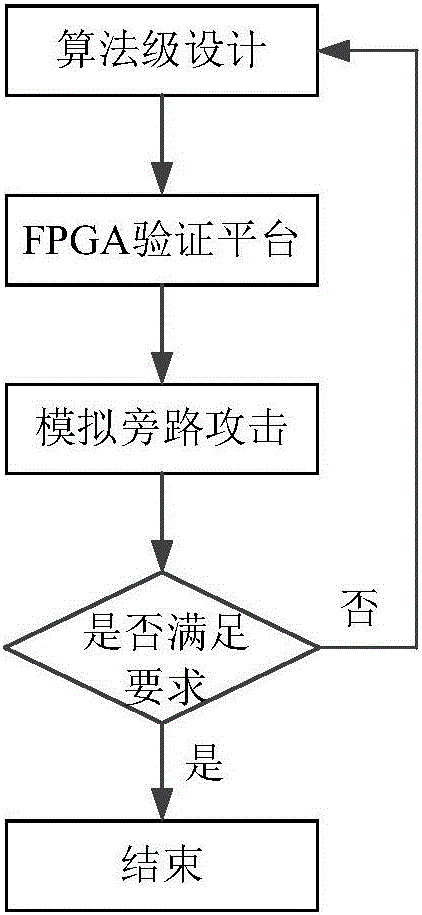
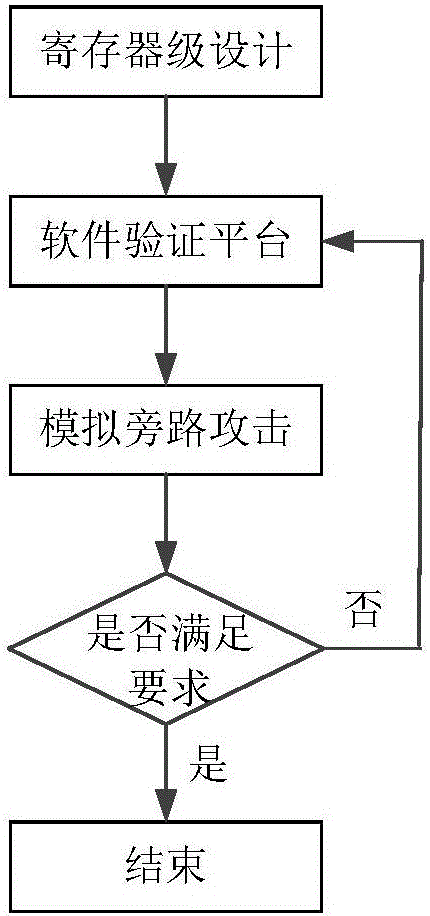
[0049] image 3 It is a flowchart of an on-chip power supply network verification method for side channel attacks in an embodiment of the present invention. Combine below image 3 Taking a test benchmark (a set of plaintext-ciphertext data pairs) as an example, each step and its principle are described in detail.
[0050] Step S110, performing logic synthesis and physical design on the register transfer level netlist file of the chip to obtain the transistor level netlist file.
[0051] Among them, the verification process from the register transfer level netlist file to the transistor level netlist file is compatible with the current mainstream electronic design automation software. In this embodiment, the existing electronic design automation software tools are used to perform logic synthesis and physical design on the register transfer level netlist file to obtain the transistor level netlist file. The specific process is as follows:
[0052] First, read in the register-t...
Embodiment 2
[0087] This embodiment is based on SMIC's 180nm process, and uses mainstream electronic design automation software to complete the design of an encryption chip using a 128-bit Advanced Encryption Standard (AES, Advanced Encryption Standard) encryption algorithm. The input of the chip is a 128-bit key and 128-bit plaintext, and the output is an encrypted 128-bit ciphertext. Next, different power supply networks are designed for the chip, and the design schemes AES-1 and AES-2 are obtained respectively, and the impact of different power supply networks on the ability to resist bypass attacks is verified and analyzed. The working process of the verification method of the present invention and the verification effect achieved are further described in detail.
[0088] Based on the Verilog language design of the encryption algorithm, and SMIC's 180nm standard cell library and process library files, the logic synthesis and physical design are completed.
[0089] Extract circuit para...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com