Hardware Trojan side channel detection method based on electromagnetism and delay
A technology of hardware Trojan horse and detection method, which is applied in the direction of electronic circuit testing, measuring electronics, measuring devices, etc., can solve the problems of small area, strong latentness, and inability to clear, and achieve improved resolution of differences, effective detection, and simple methods easy effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] Complete technical scheme of the present invention is as follows:
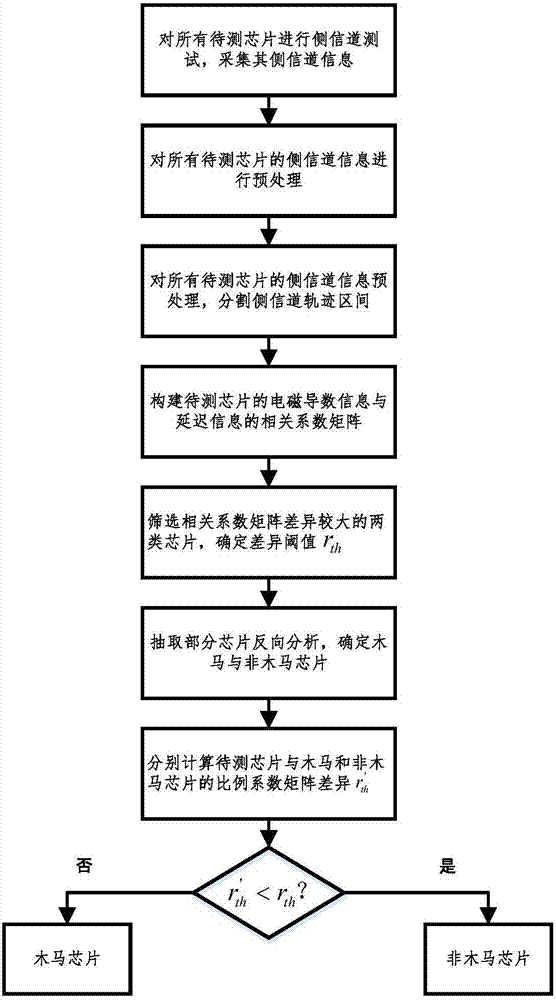
[0052] figure 1 It is a flow chart of a hardware Trojan horse side channel detection method based on electromagnetic and delay, and the method mainly includes the following steps:
[0053] (1) Perform side-channel tests on all chips to be tested, and collect side-channel information of the chips to be tested: use the side-channel acquisition platform to collect the electromagnetic information leaked by the circuit in the working state and the delay information of a certain path multiple times.
[0054] (2) Preprocessing the side channel information of all chips under test: smoothing and filtering the electromagnetic information and delay information collected multiple times by all chips under test to obtain smooth electromagnetic information and delay information. Divide the electromagnetic information and delay information of the chip to be tested into n intervals, and perform derivation processing on...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com