IP white list building method based on intranet traffic
A whitelist and intranet technology, applied in electrical components, transmission systems, etc., can solve the problems of poor whitelist pertinence and high generation cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
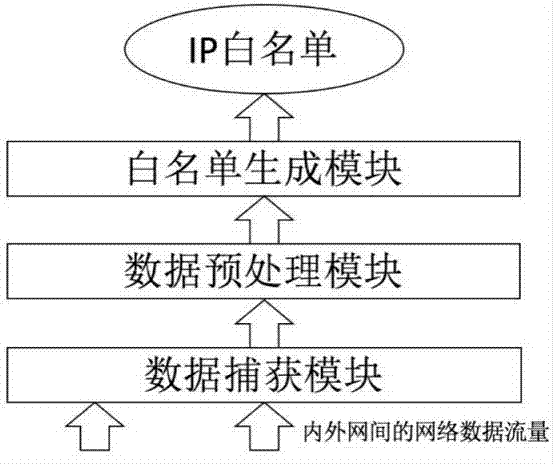
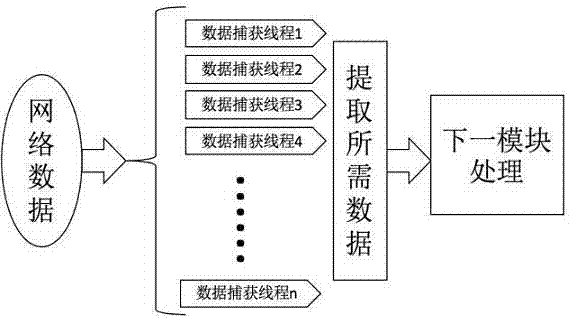
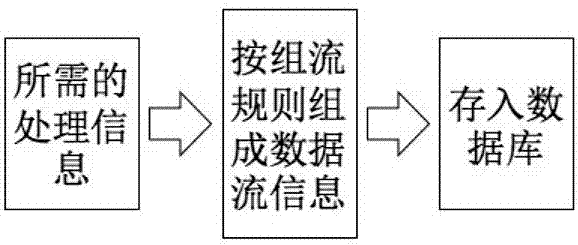
[0015] The whitelist construction method in the present invention aims to realize more targeted IP whitelist construction through simple network communication flow records with higher efficiency and low cost. The present invention will be further described below in conjunction with the accompanying drawings. The method provided by the present invention can effectively solve the shortcoming that the intranet traffic monitoring system occupies too much system resources when processing traffic, and summarizes the characteristics of normal network traffic generation and the behavior characteristics of intranet users accessing the network, and summarizes a set of construction The rules of the IP whitelist can not only reduce the processing pressure of the intranet security monitoring system, but also prevent suspicious traffic from being filtered out.
[0016] figure 1 is an architectural diagram describing the technology of the present invention.
[0017] Such as figure 1 Shown...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com