An Image Tampering Detection Method Based on Double-Image Reversible Fragile Watermarking
A fragile watermark and tamper detection technology, applied in the field of image information, can solve problems such as unsatisfactory authentication results, inability to restore the original image without errors, and inaccurate detection of modified areas
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
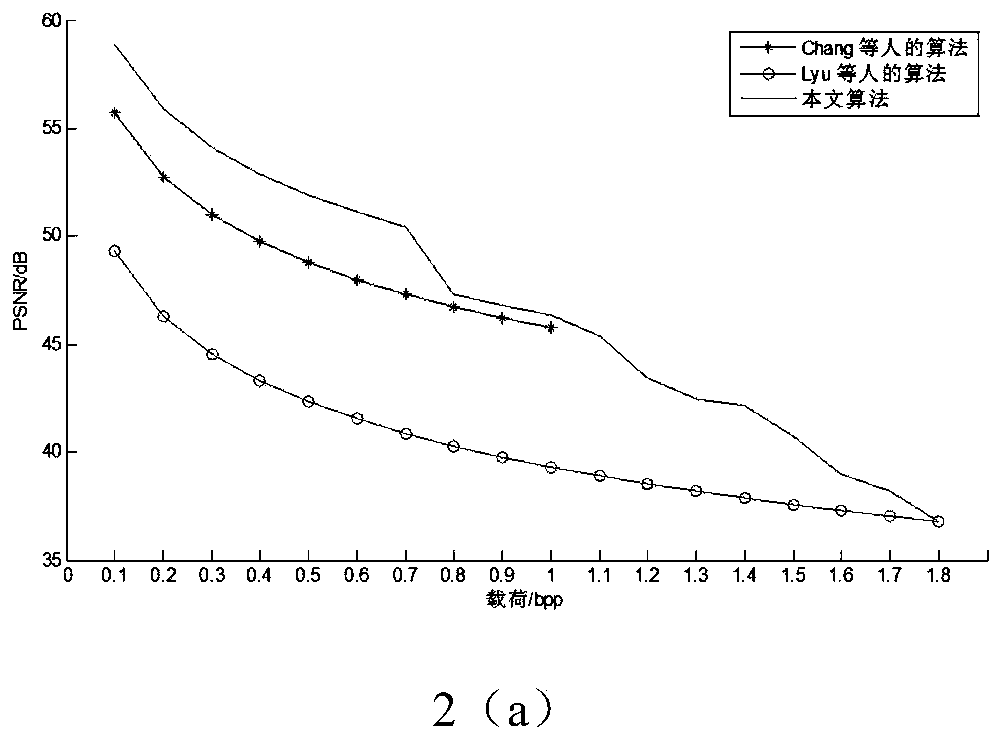
[0114] Embodiment 1: Carry out image hiding capacity, quality and safety test.
[0115] This embodiment uses MATLAB software, the watermark information is the binary pseudo-random number generated by the key, and nine 512×512 grayscale images: Lena, Peppers, Sailboat, Tiffany, Plane, Boat, Baboon, Splash, and Man are used as host images ,Such as figure 1 shown.
[0116] The quality of information hiding is usually evaluated from two aspects: the quality of information hiding and the capacity of information hiding. PSNR (peak signal to noise ratio) is a common indicator for evaluating the quality of information hiding. The calculation formula is as follows:
[0117]
[0118]
[0119] MSE is I 1 ' and I1 mean square error of . I 1 ' and I 1 The higher the similarity, the smaller the mean square error and the higher the PSNR value. Generally, when the PSNR value is greater than 30dB, it is difficult for people to directly observe the difference between the two images...
Embodiment 2
[0125] Example 2: Image Integrity Authentication Test.
[0126] Figure 4 In embodiment 2, after using the present invention, the distribution of the authentication information area in the image can be embedded. Here, the present invention groups two pixels into one group. Figure 4 The middle black and white are alternately distributed, the black part is a blind area, and the white part can be embedded in the authentication information area. Figure 4 The first pair of pixels in (a) embed authentication information, Figure 4 The first pair of pixels in (b) embeds distortion information, and the second pair of pixels in the two images is the opposite, that is, the area embedded with authentication information and the area embedded with distortion information are equally divided by the two images. Compared with other reversible authentication methods, the embeddable area of the authentication method in the present invention is not limited by image texture.
[0127] In or...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com