Hardware Trojan detection system and method based on multi-parameter side channel analysis
A technology of hardware Trojan detection and side channel analysis, which is applied in electrical digital data processing, internal/peripheral computer component protection, instruments, etc., can solve the problems of unfeasible test methods and large amount of calculation, etc., to reduce background current and improve detection Sensitivity, the effect of improving the signal-to-noise ratio
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
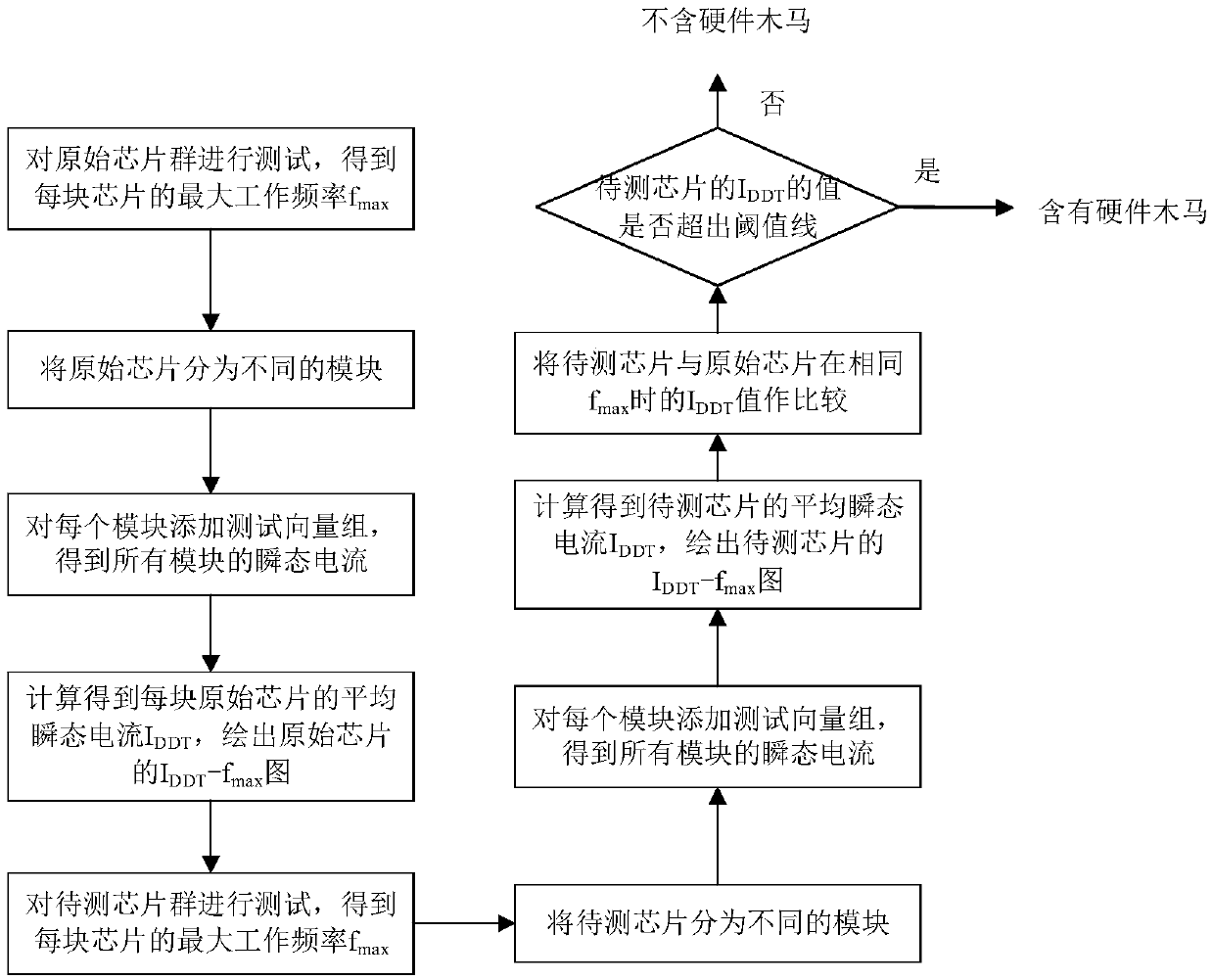
[0055] Embodiment one: the hardware trojan is placed in the controllable module 3 of the 32-bit ALU circuit, such as Figure 7 shown. The hardware Trojan can be detected when module 3 is activated, that is, during the period from 2ns to 4ns. During this period, other controllable modules (module 2 and module 4) are disconnected, thereby reducing the static power consumption by 50%, and weakening the process noise generated by the circuit. In this case, deactivating other modules will make the change of the transient current due to the insertion of the hardware Trojan more obvious. It can be shown from the above that using this method so that only one module is activated each time (except module 1) can increase the sensitivity of Trojan horse detection.
Embodiment 2
[0056] Embodiment 2: The hardware Trojan horse is placed in the active module 1 of the 32-bit ALU circuit. Since module 1 is always active, its transient current can only be detected when all controllable modules are deactivated, in this embodiment before or after 6 ns of the external signal to the SC. The hardware Trojan horse system of detection module 1 is established as Figure 8 As shown, TD is "high" and SC is "low" to inactivate all other controllable modules. If there is a hardware Trojan in this block, it will be easily detected, because the static power consumption of the circuit (the other 3 modules are deactivated) is reduced by 75%, and the process noise generated by the circuit is significantly reduced, making the noise caused by the hardware Trojan Transient current changes are very noticeable.
Embodiment 3
[0057] Embodiment 3: Even if there is a hardware Trojan among different modules, the present invention can effectively detect the Trojan. Such as Figure 9 As shown, here, it is assumed that both module 2 and module 3 have hardware Trojans, which can be detected by activating these modules individually. First, module 2 is activated by giving pulse excitation at SC1, after which the transient current of module 2 can be detected. Then, module 3 is activated by SC2 after a buffer delay, after which the transient current of module 3 can be detected. The transient current change of the circuit under the superimposition of two hardware Trojan horses is very obvious.
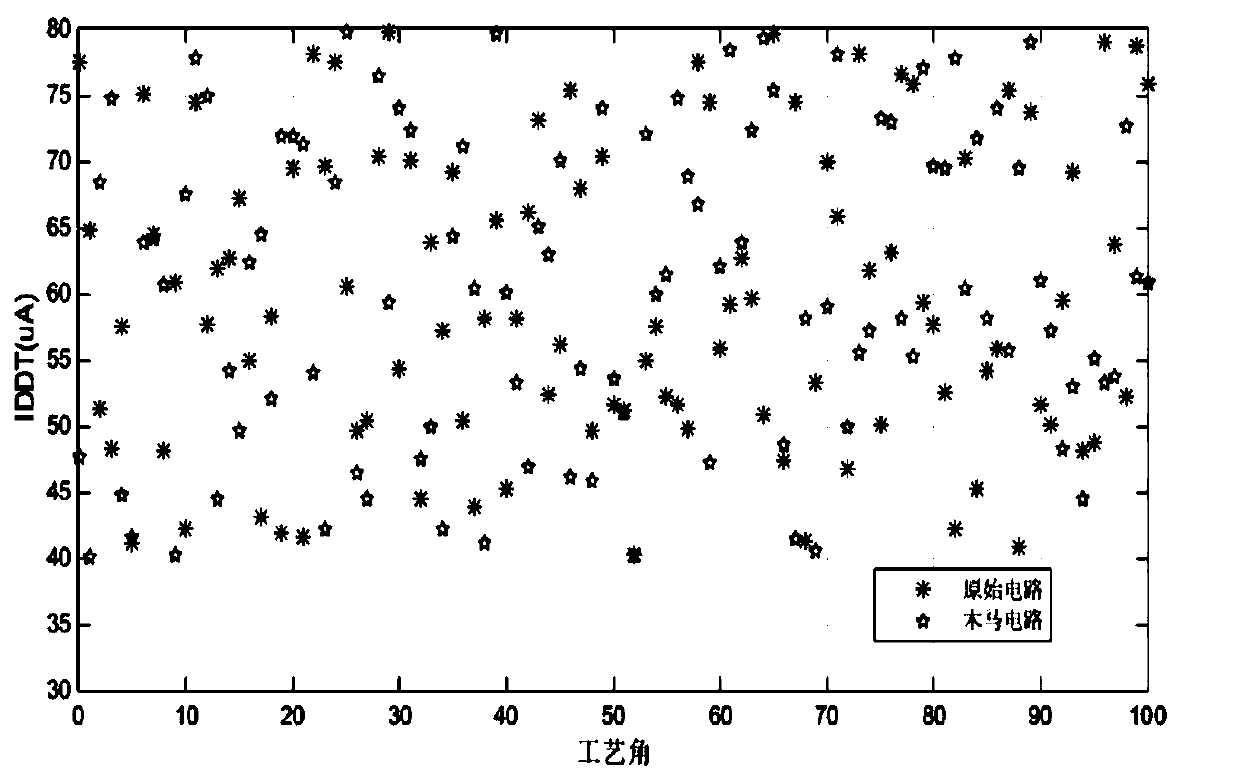
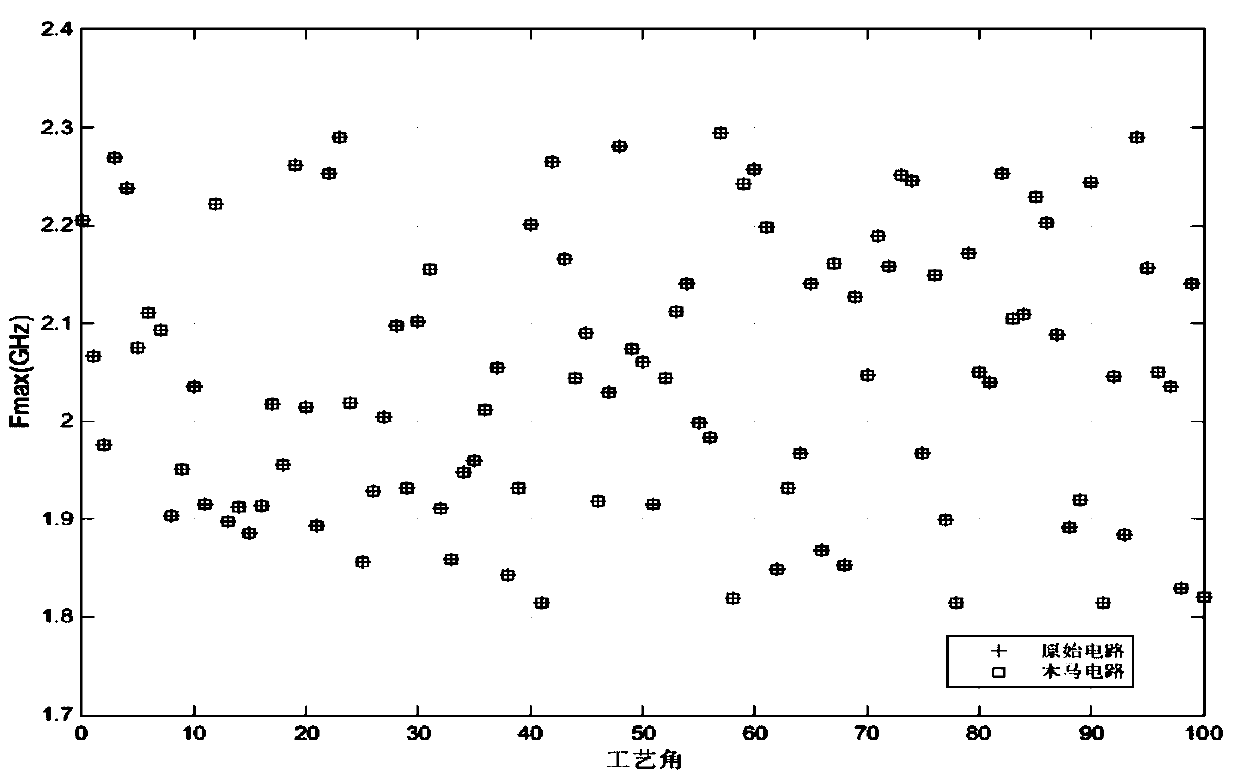
[0058] The above examples all illustrate that the present invention can amplify the influence of the hardware Trojan horse on the transient current of the circuit. Thus the average transient current I of the IC chip is obtained DDT , with the average transient current I DDT value and maximum operating frequency f ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com