Smart city information security guarantee system
A technology for urban information and security assurance, applied in the field of information security, can solve problems such as complex security issues, privacy information theft, lack of post-supervision of cloud services, etc., to achieve the effect of enhancing security and ensuring information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
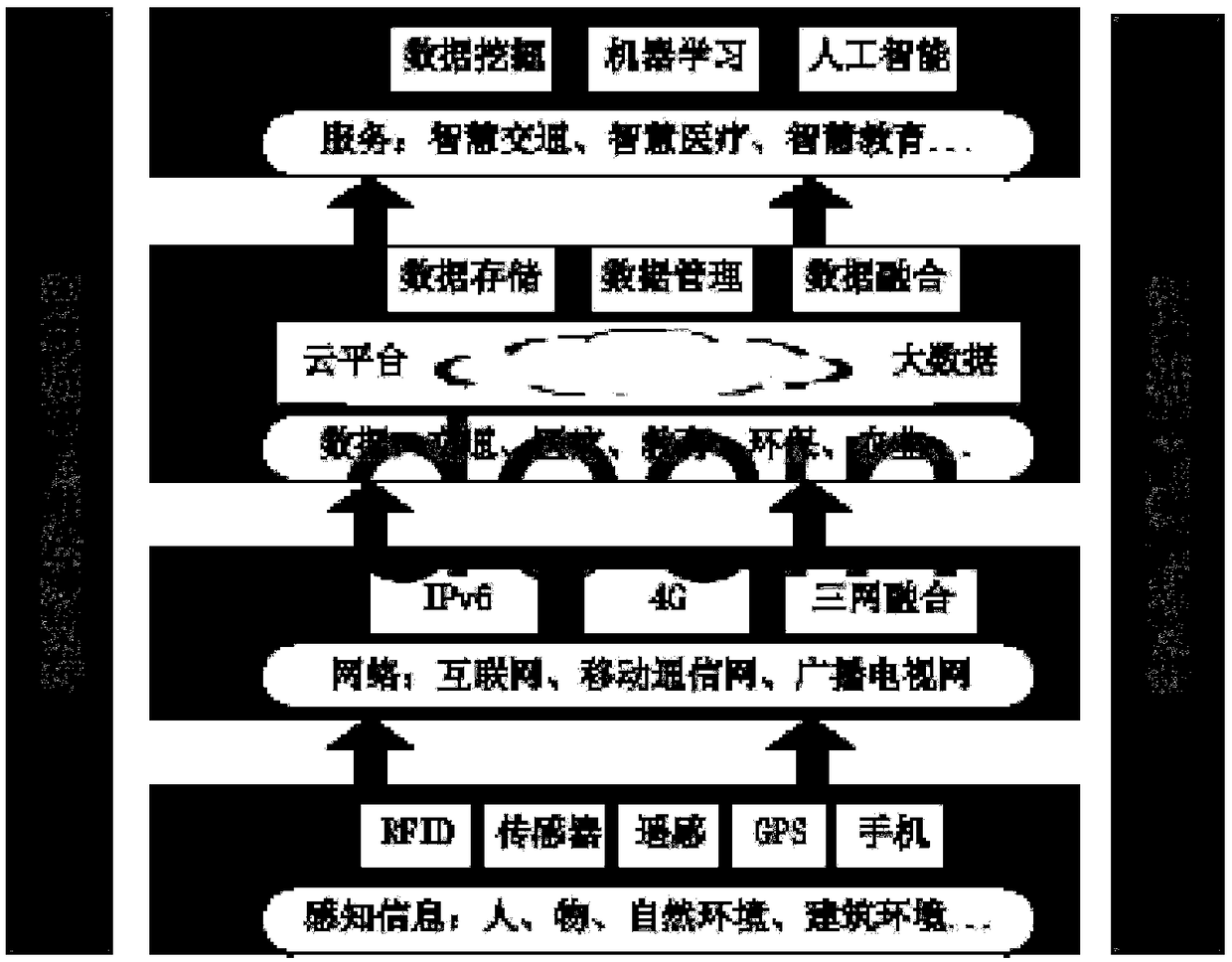
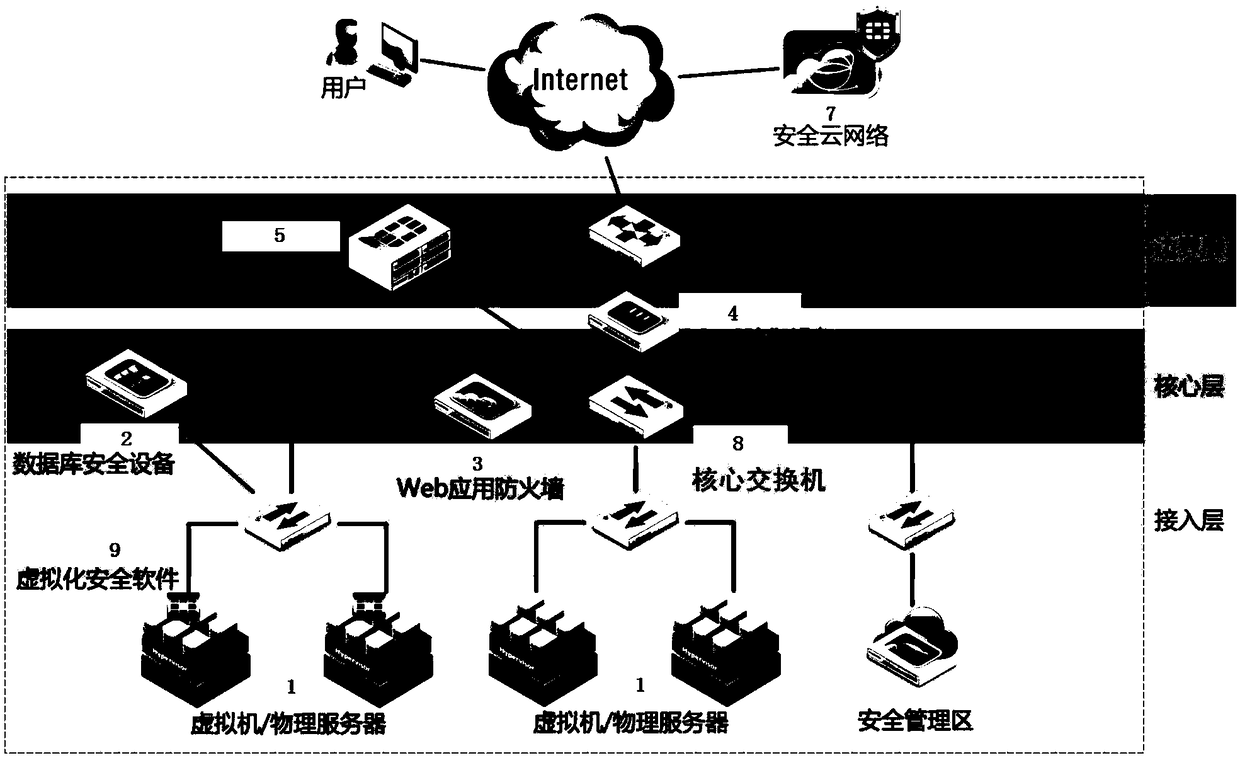
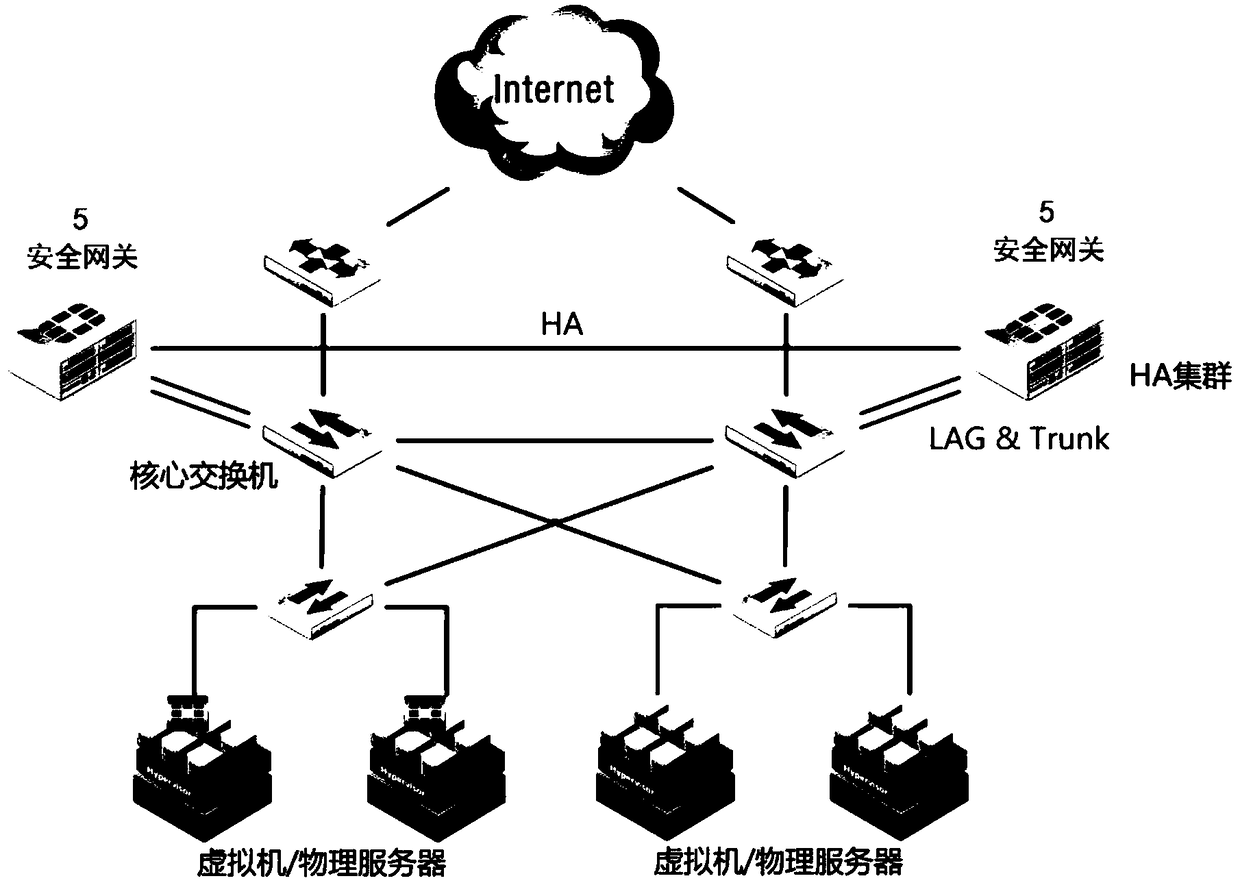
[0040] Please refer to Figure 2 to Figure 6 As shown, it shows the specific structure, method, process and working principle of the preferred embodiment of the present invention, which will be described in detail in conjunction with the accompanying drawings.
[0041] figure 2It is a schematic diagram of the smart city security system. Cloud computing data centers face a variety of security threats, including hacking, denial of service attacks, eavesdropping, viruses, Trojan horses, worms, etc., as well as hybrid attacks and APT attacks that combine the above threats. Therefore, security hardening needs to be done on the network infrastructure first. Using Security Gateway 5 Unified Threat Management (UTM) security appliance provides unparalleled functionality and detection capabilities through dynamic threat defense technology, advanced heuristic anomaly scanning engine. It integrates a variety of security functions, covering the network layer, data layer and application...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com