Data authorization method and system
A technology of data authorization and data request, applied in the direction of digital transmission system, transmission system, user identity/authority verification, etc., can solve the problem of lack of flexibility and efficiency, difficulty in adapting to a dynamic and changeable network environment, and difficulty in supporting flexibility and efficiency To improve flexibility and efficiency, support security sharing and value protection, and realize generalization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
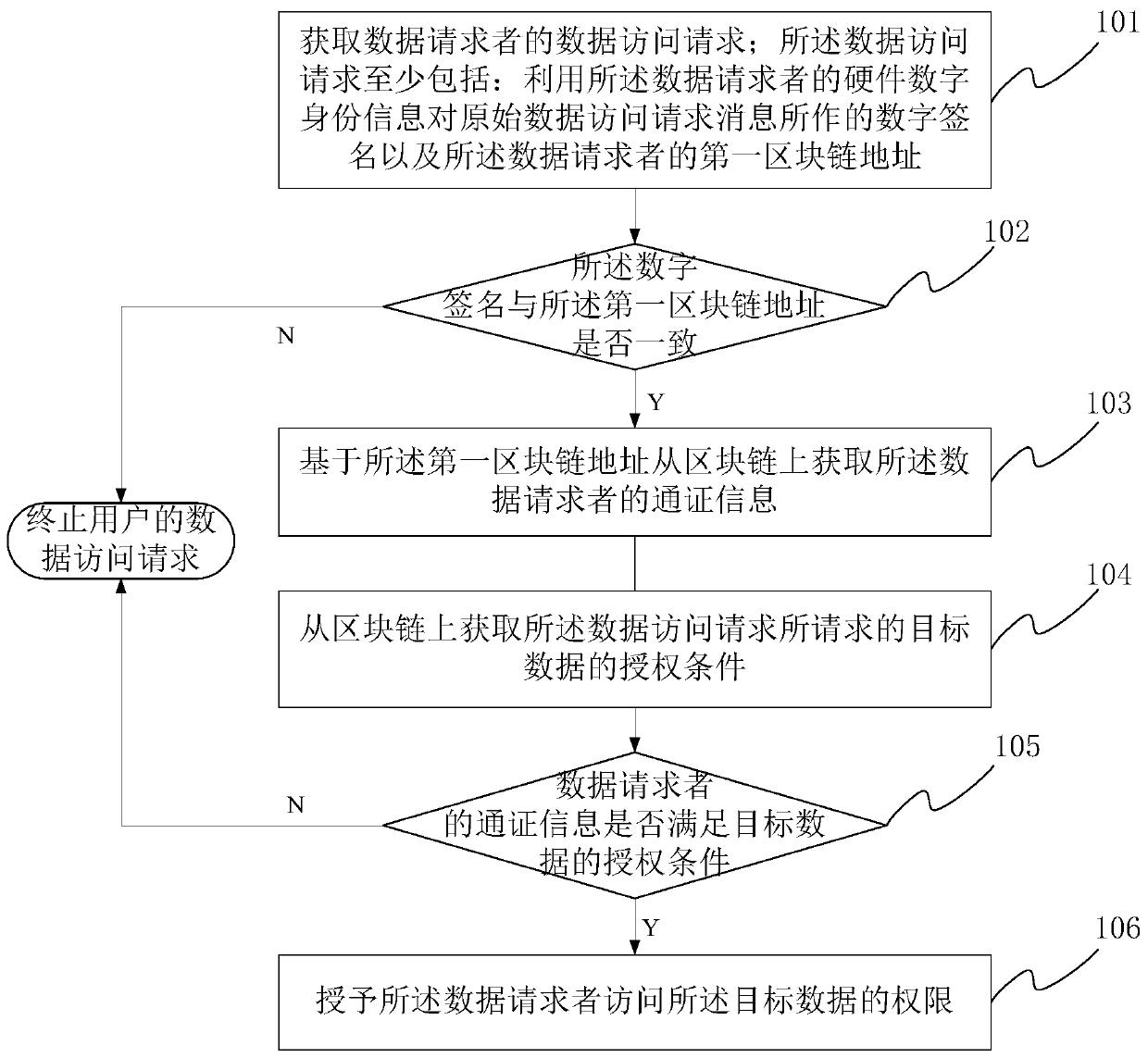
[0054] refer to figure 1 , is a schematic flowchart of the data authorization method provided in Embodiment 1 of this application. In Embodiment 1, as figure 1 As shown, the data authorization method includes the following processing steps:
[0055] Step 101, obtain the data access request of the data requester; the data access request at least includes: the digital signature obtained by signing the original data access request message with the hardware digital identity information of the data requester and the data requester's The first blockchain address.
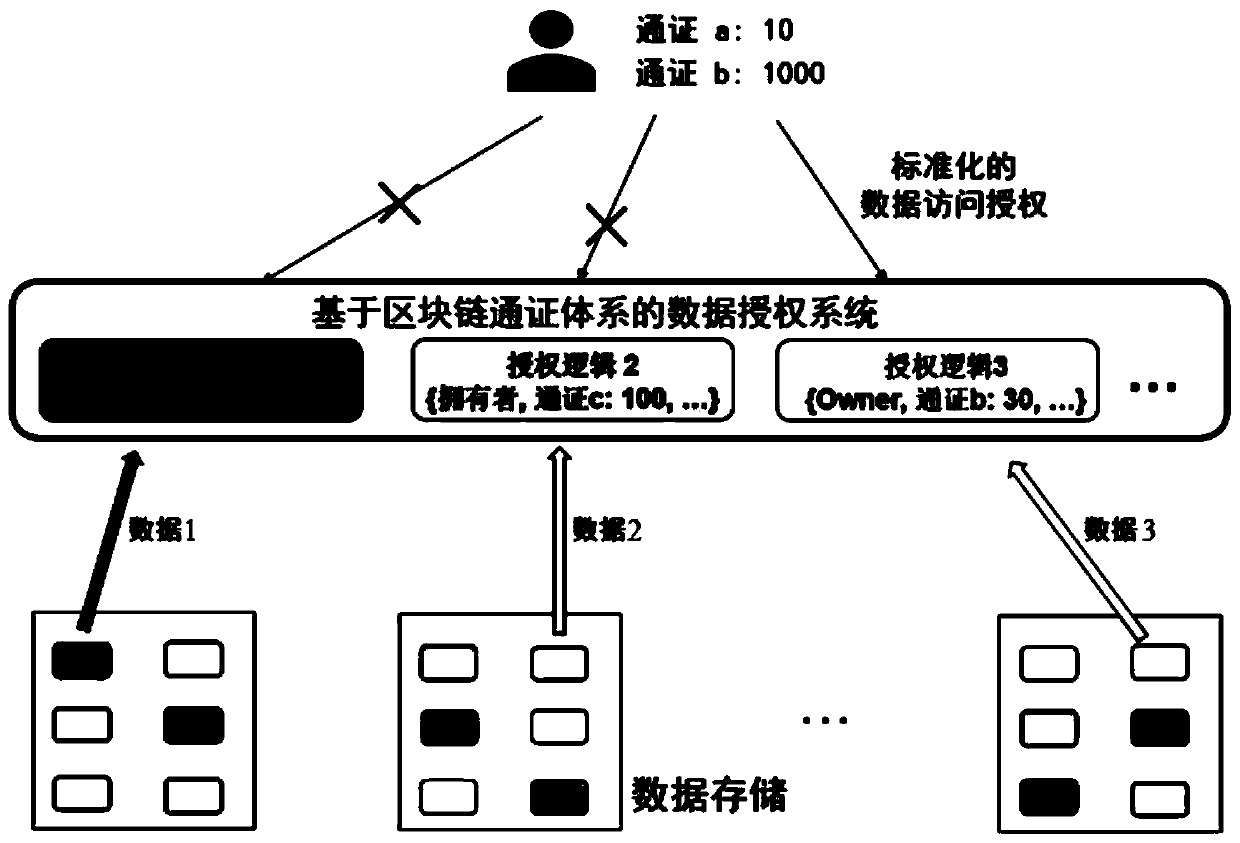
[0056] In practical applications, the data authorization processing logic of the method of this application can be implemented in the form of a software system. Specifically, refer to figure 2 As shown, a data authorization system based on the blockchain token system can be realized based on the method of this application.
[0057] Users who participate in the use of this system, such as data requesters who need to re...
Embodiment 2
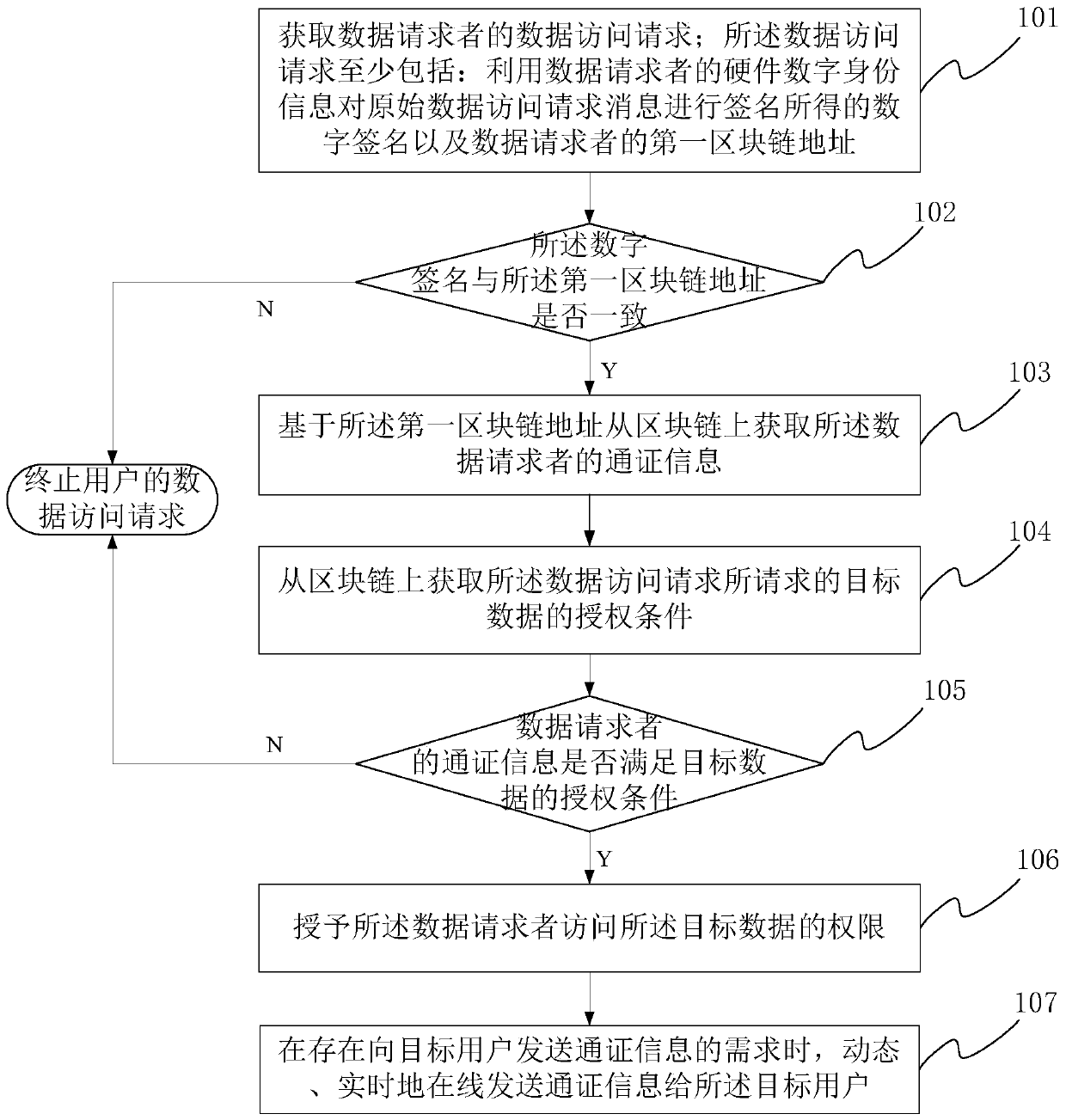
[0082] refer to image 3 , is a schematic flowchart of the data authorization method provided in Embodiment 2 of the present application. In this embodiment, the data authorization method may further include the following steps:
[0083] Step 107. When there is a need to send the token information to the target user, send the token information to the target user online in a dynamic and real-time manner.
[0084] Among them, the system administrator can dynamically and real-time send token information (including the type and quantity of tokens) online to a target user according to actual needs, so as to temporarily grant a target user access to certain data. And specifically, the system administrator can also set the valid time limit information of the pass information sent online according to actual needs, for example, set the valid time limit of the sent pass information to 5 minutes, etc., so that, subsequently, the target user can be in this The sent pass is used for corre...
Embodiment 3
[0087] refer to Figure 4 , is a schematic flowchart of the data authorization method provided in Embodiment 3 of the present application. In this embodiment, the data authorization method may further include the following steps:
[0088] Step 108: Record the interaction information involved in the process of the interaction between the user and the blockchain, and store the interaction information on the blockchain.
[0089]Specifically, it may include but is not limited to recording in the blockchain the interaction information involved in various interactive operations such as the data owner registering with the blockchain, the data requester requesting access to data from the blockchain, and the sending of tokens. .
[0090] In this embodiment, by recording the interaction information involved in the process of interaction between the user and the blockchain in the blockchain, it can facilitate the traceability and auditing of subsequent data authorization behaviors.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com