Cloud security service function tree network intrusion detection system
A technology of network intrusion detection and security service, applied in the field of cloud security service function tree network intrusion detection system, which can solve the problems of difficult updating and difficult deployment, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
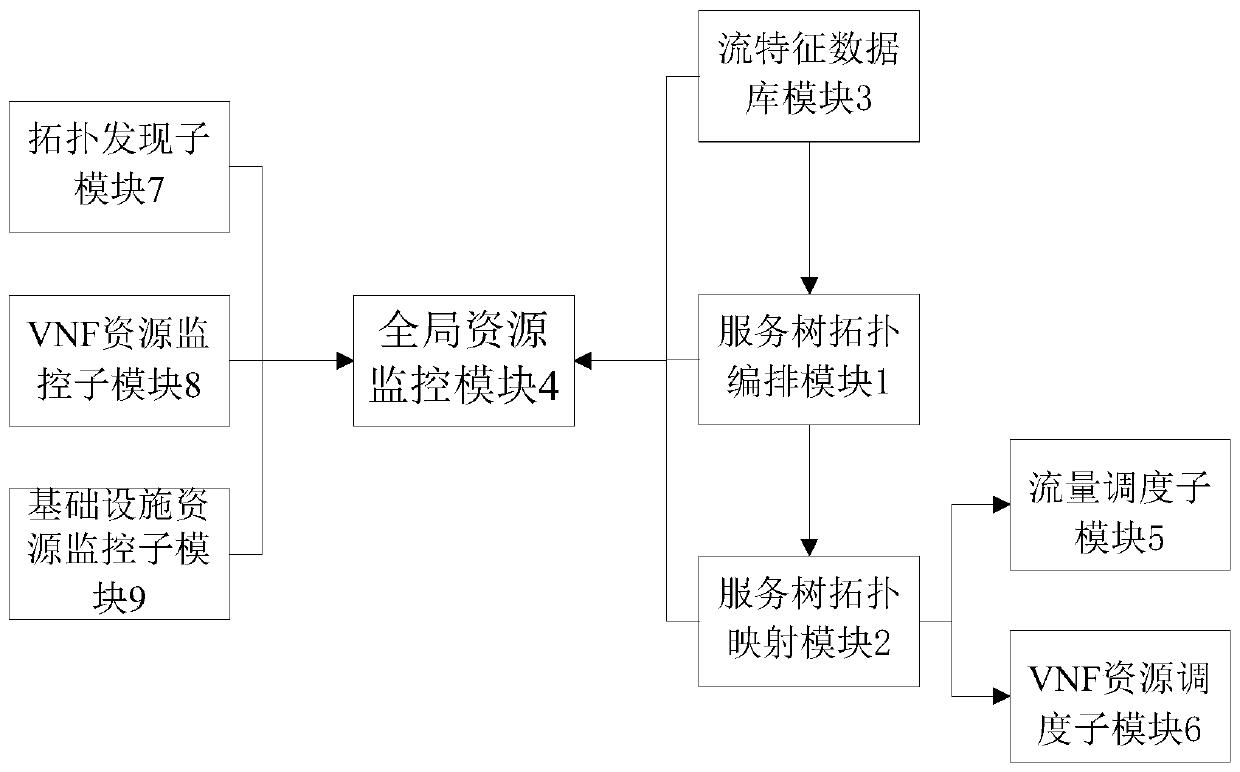
[0030] Such as figure 1 , figure 2 As shown, a cloud security service function tree network intrusion detection system includes a service tree topology arrangement module 1, a service tree topology mapping module 2, a flow feature database module 3, and a global resource monitoring module 4;
[0031] The flow feature database module 3 is used to store the network flow feature data of the network attack, and select the corresponding network attack flow feature data set in conjunction with the cloud security situation to construct a corresponding training set;
[0032] The service tree topology arrangement module 1 is used to construct a decision tree classification model in combination with the cloud security situation, use the training set constructed in the stream feature database module 3 to train and prune the decision tree model, and classify the trained decision tree The model is passed to the service tree topology mapping module 2;
[0033] The service tree topology m...
Embodiment 2
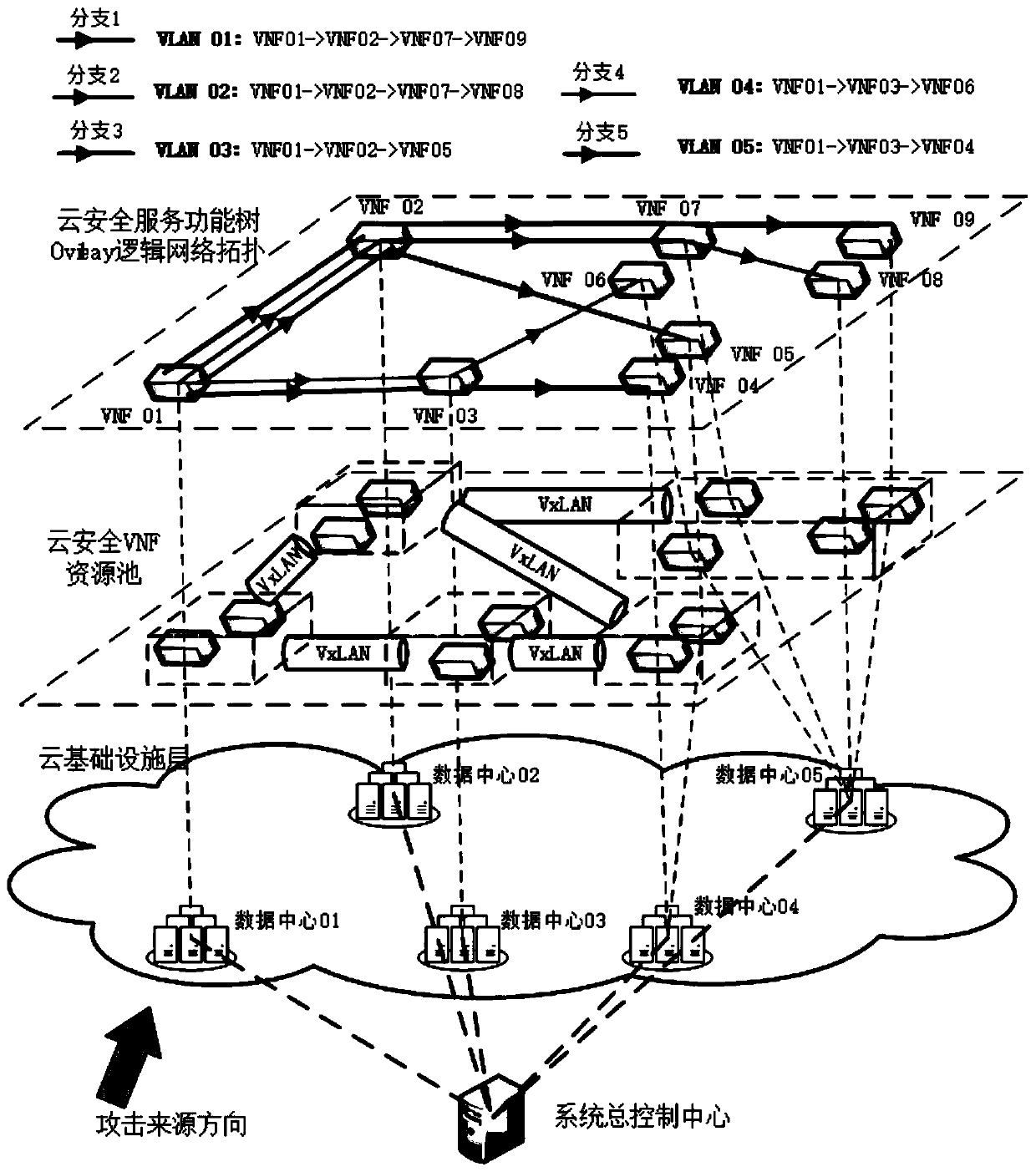
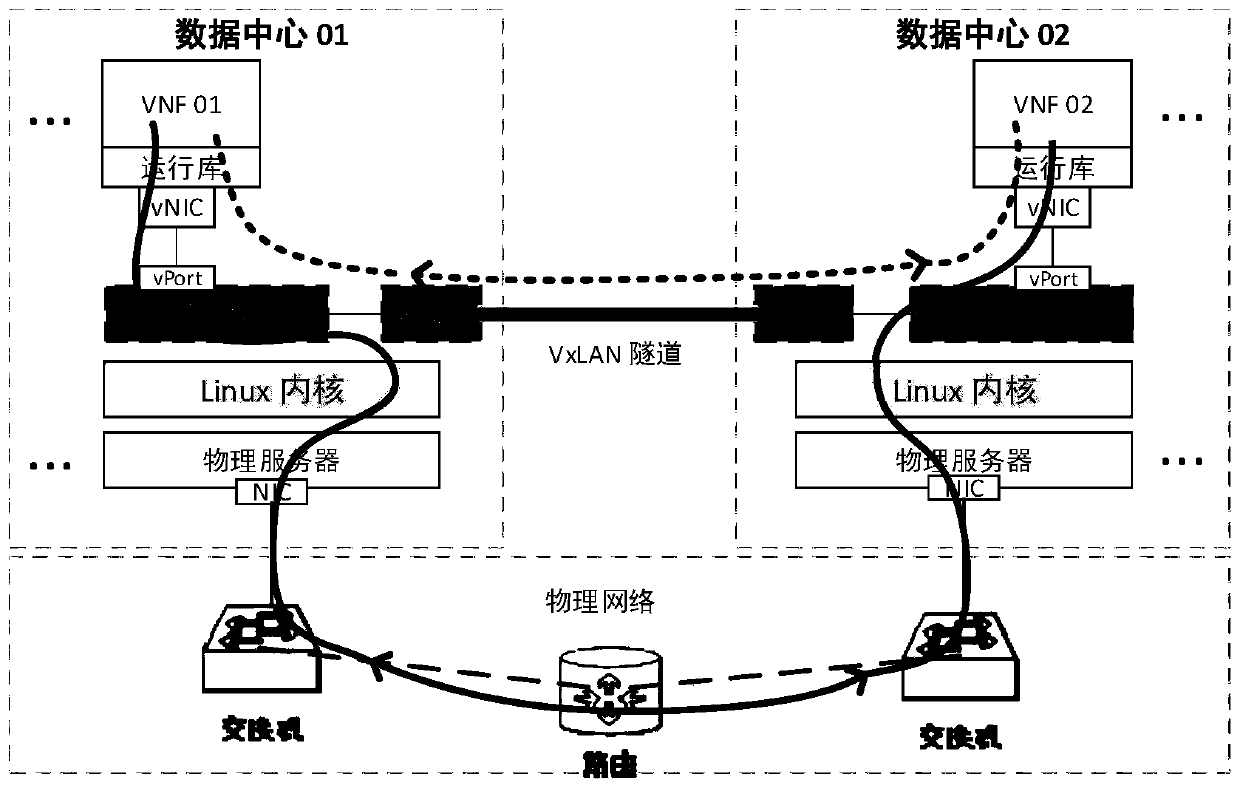
[0045] Such as image 3 as well as Figure 4 As shown, in this embodiment, the tree topology of the service function tree is combined with the characteristics of the network attack traffic identification and classification of the decision tree, and the characteristic rules of the decision tree nodes are matched and distributed to each VNF node of the service function tree. accomplish. Under the guidance of the decision tree classification idea, each path from the root node of the service tree to each leaf node is a VNF node path through which network traffic with certain characteristics flows. image 3 In the process of VNF communication across data centers, a virtualized container network is implemented. Two OVS virtual network bridges are built on the host machine through network virtualization technology, among which the br-int virtual network bridge mainly assumes the role of data packet exchange in the local network segment in the container data exchange network; the br...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com