Block chain distributed dynamic network key generation and encryption method
A technology of key generation and dynamic network, which is applied to the public key and key distribution of secure communication, which can solve problems such as inability to effectively decrypt ciphertext, difficulties in key distribution and management, and easy leakage of shared keys. Reduce the risk of information leakage and cracking, strengthen the ability to resist attacks, and reduce the effect of steps
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
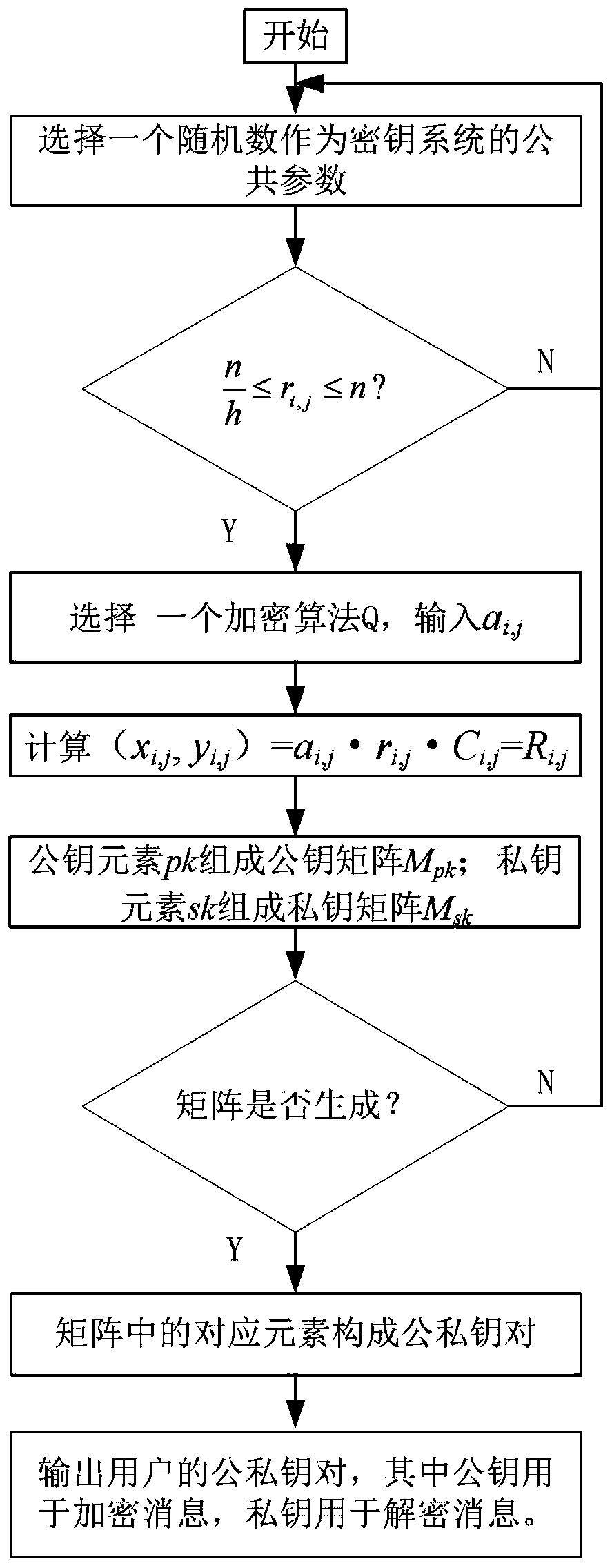
[0051] 2. figure 2 It shows the flow chart of key generation and encryption of the present invention, and the principle of key generation and encryption is shown in the figure, which includes the steps of using public parameters and random coefficients for key generation, selecting a probability algorithm for public-private key matrix and The process of generating the public-private key pair, adopting this scheme has the advantage of protecting the security of the key. Moreover, this manner is only an illustration of a preferred example, but is not limited thereto. When implementing the present invention, it is possible to design an algorithm and determine whether random coefficients are needed or not according to user requirements. For example, the steps for key generation and encryption are as follows:
[0052] 2.1 Choose a random number r i,j As a public parameter of the key system, verify that the random number satisfies Otherwise, continue to step 2.1, where n is th...
specific Embodiment 2
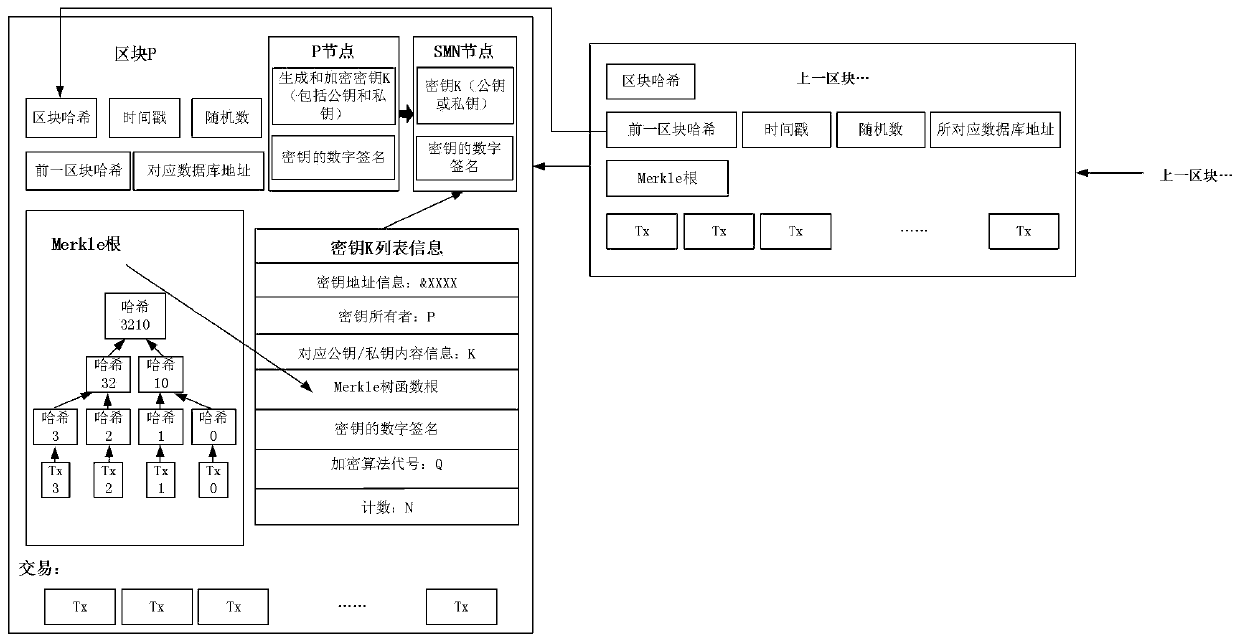
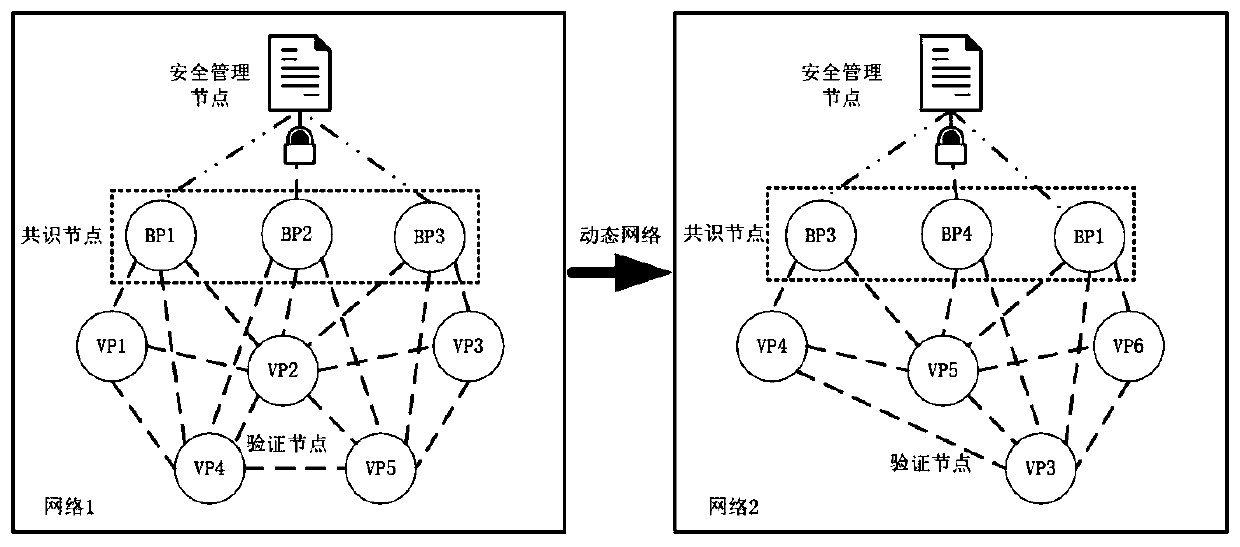
[0063] 3. image 3 It shows the principle diagram of the key update of the present invention, for example, in the block chain network 1:
[0064] 3.1 After receiving key encryption information each time, SMN accumulates key generation and encryption times in the list;
[0065] 3.2 After reaching the specified number of times, select an encryption algorithm from the alternative N encryption algorithms to regenerate and encrypt the key, and at the same time update the data information carried by the key accordingly;
[0066] 3.3 After each transaction is completed, the key is regenerated and encrypted. After passing the verification, the list is updated by SMN, and the cumulative key is generated and encrypted at the same time. Then, SMN requests the consensus node BP to write into the ledger, and BP completes the packaging and blocks to ensure the key Can not be tampered with. Among them, in the process of checking the key information, if the result is true, the data is tempo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com