Blockchain cloud storage user data security solution
A technology of user data and solutions, applied in the field of blockchain applications, can solve problems such as hackers that cannot be ignored, achieve the effects of reducing the risk of data loss and complete data theft, good application prospects, and convenient management of stored data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
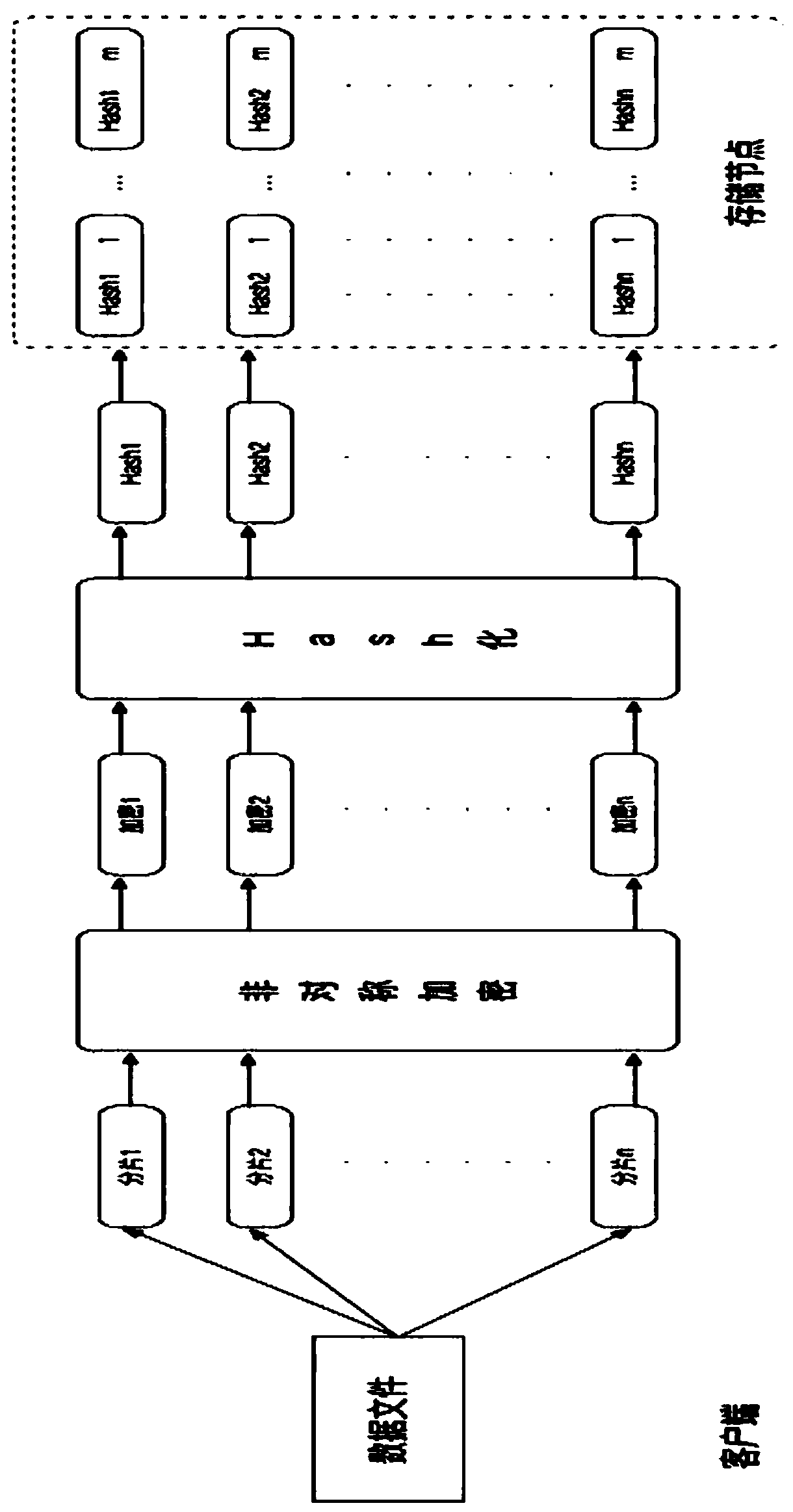
[0018] Figure 5 As shown in , a blockchain cloud storage user data security solution is divided into four steps. Step A: The client builds the blockchain client operating environment and downloads the operating framework through the application construction unit in the PC. In step A, you need to download the Visual Studio Code (editor) development tool, use Node.js (JavaScript operating environment based on Chrome V8 engine) to develop the client, download the Eclipse (extensible development platform) development kit), use the Java language to develop blockchain.
[0019] Figure 5 As shown in , Step B: The client uses the multi-signature technology based on zero-knowledge consensus to perform multi-signature through the application unit in the client. In step B, in the multi-signature, the key pair used is asymmetric encryption, and the process of generating the key does not need to be known between nodes, and only needs to use the unified verification machine of the whole...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com