Authentication information processing method, terminal and network equipment
An information processing method and technology of network equipment, applied in the field of terminal and network equipment, authentication information processing method, can solve the problems of consuming large computing resources, being unavailable to attackers, and unable to initiate correlation attacks by attackers.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
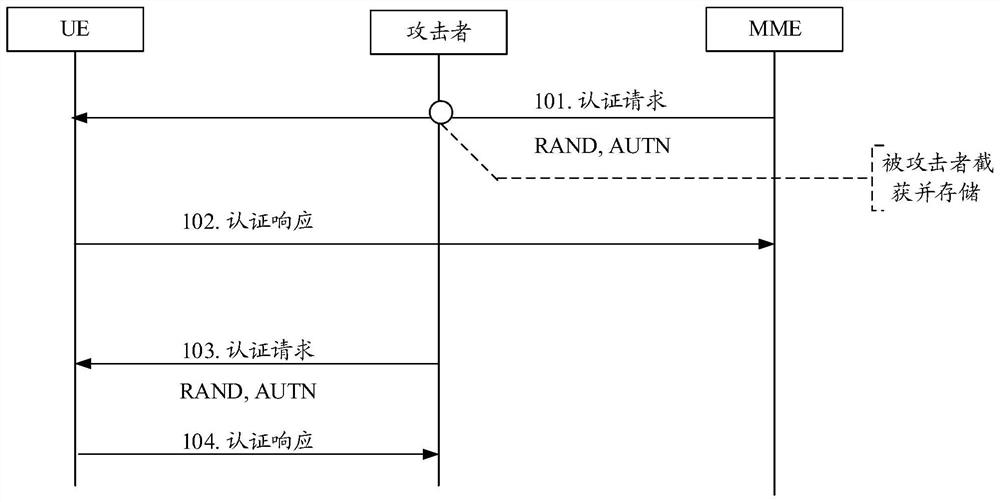
[0082] Before describing in detail the authentication information processing method of the embodiment of the present invention, first, a brief introduction to the association attack is made.
[0083] figure 1 Schematic diagram of the process of correlation attacks in related technologies; figure 1 Take 4G network (such as LTE network) as an example for description. Such as figure 1 Shown, including:
[0084] Step 101: The mobility management entity (MME, Mobility Management Entity) sends an authentication request message to the UE, and the authentication request message includes a random password (RAND) and an authentication token (AUTN). In this step, the attacker may intercept the authentication request message, obtain and store the random password (RAND) and authentication token (AUTN) in the authentication request message.
[0085] Step 102: The UE performs network authentication. After the network authentication is completed, the UE sends an authentication response message to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com