High-efficiency quantum digital signature method and system
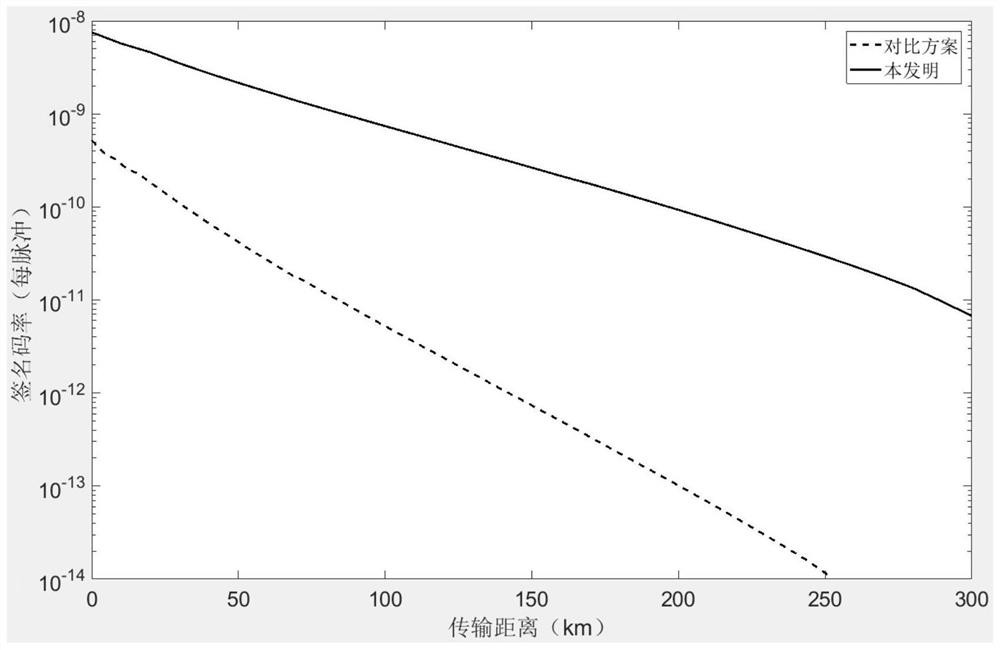
A quantum digital signature and high-efficiency technology, applied in the field of high-efficiency quantum digital signature methods and systems, can solve the problems of resource waste and low efficiency, and achieve the effect of reducing loss and reducing communication resource waste
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
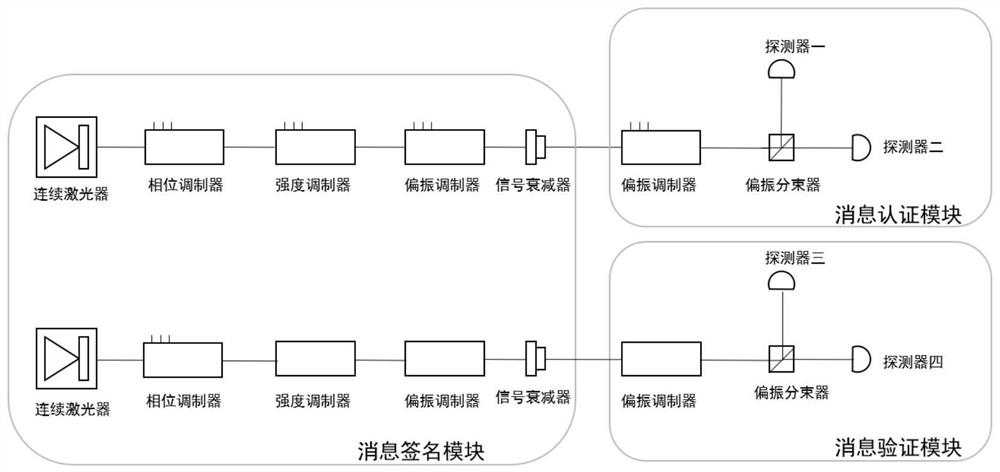
[0045] figure 1 An exemplary quantum digital signature system for implementing the method described in Embodiment 1 is given, including a message signature module, a message authentication module, and a message verification module connected through an insecure quantum channel.
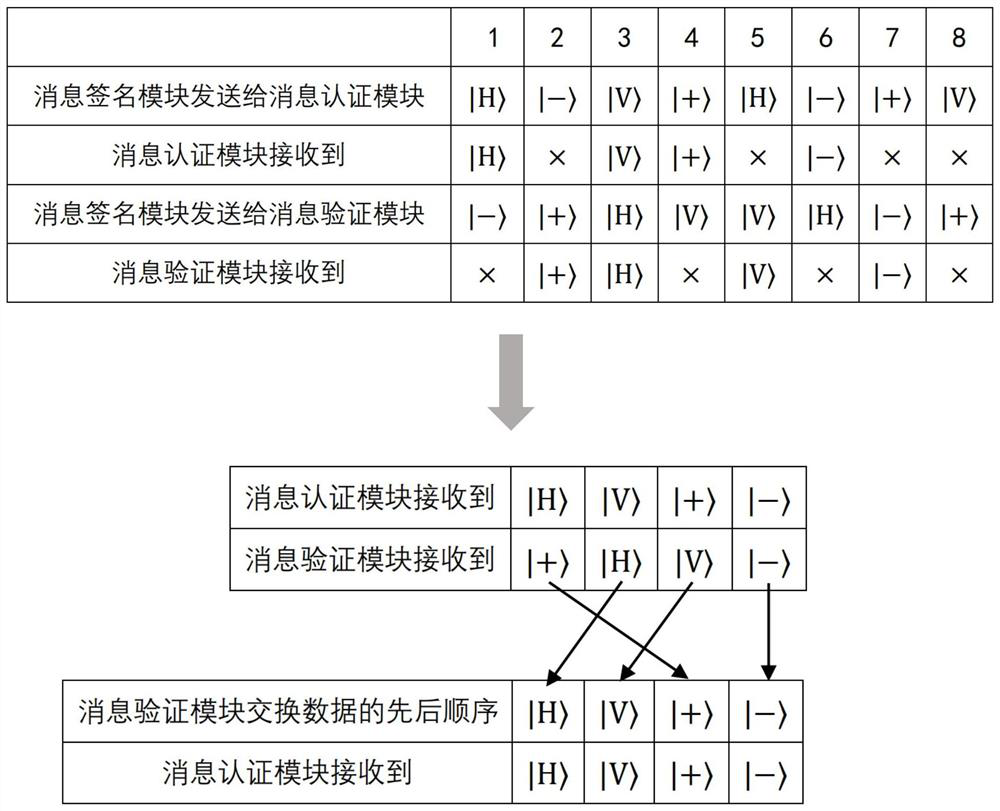
[0046] Such as figure 1 As shown, this embodiment considers the situation that the channels of message signature module-message authentication module and message signature module-message verification module are symmetrical, and the devices of message authentication module and message verification module are the same. The message signature module uses a continuous laser to generate phase-randomized weakly coherent state pulses, and uses phase modulators, intensity modulators, polarization modulators, and signal attenuators to perform phase randomization, decoy state modulation, and polarization encoding, respectively. The intensity modulator can modulate the pulse into the light intensity of {μ, v, ω}....
Embodiment 2
[0091] This embodiment considers the channel asymmetry between message signature module-message authentication module and message signature module-message verification module. At this time, the remaining steps of the signature scheme are the same as those in Embodiment 1, except that: in the case of asymmetric distances, an asymmetric light intensity is selected with an asymmetric probability to prepare a quantum state. For example: the distance between the message signature module and the message authentication module is L B , and the distance between the message signature module and the message verification module is L C ; The message signature module starts with The probability of selecting light intensity {μ B , v B , ω B} send N B pulses to the message authentication module to The probability of selecting light intensity {μ C , v C , ω C} send N C pulses to the message verification module. In the above process, the probability of the light intensity selecte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com