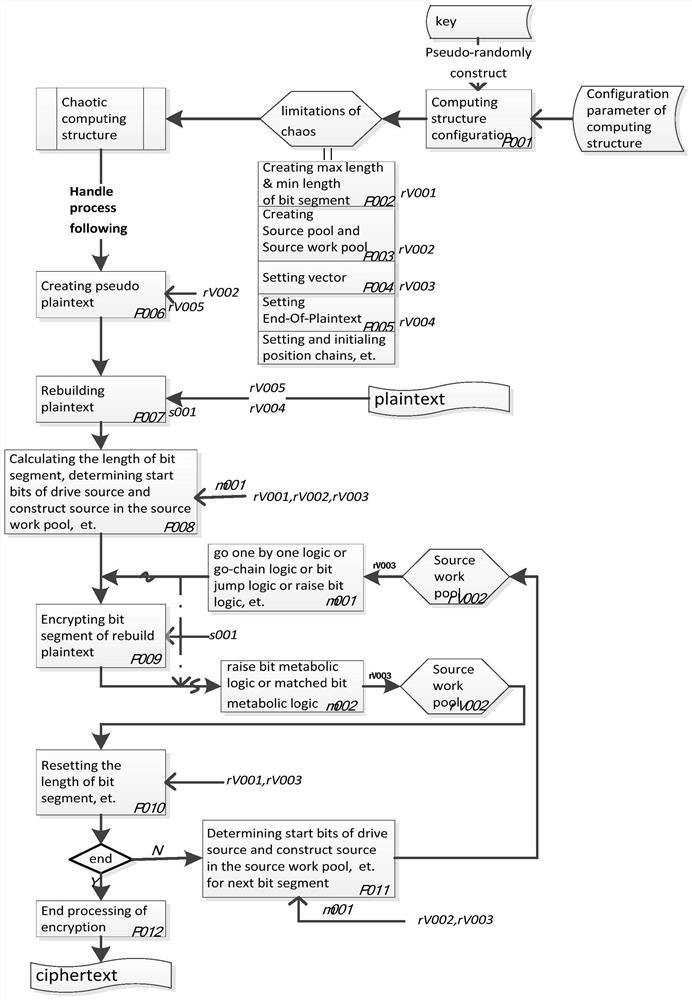
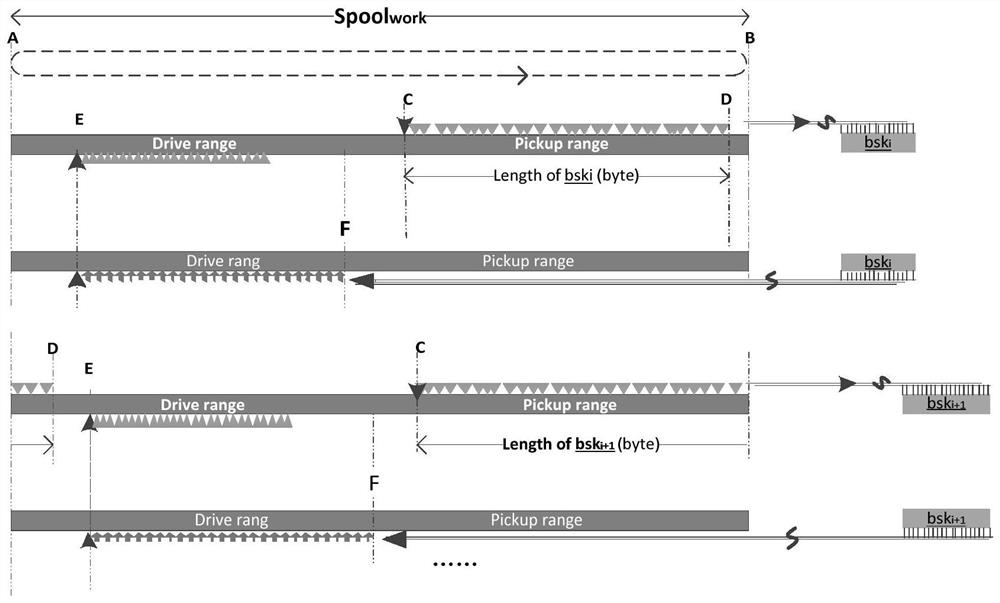
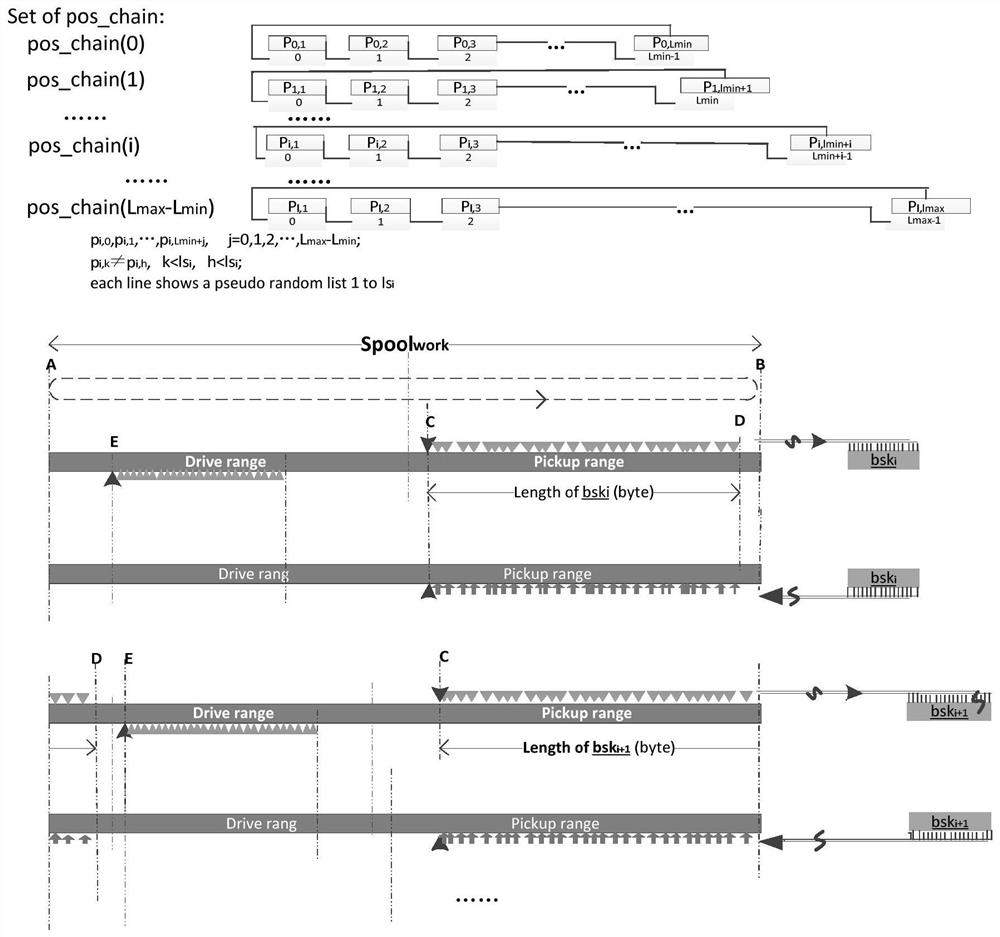
Sequence encryption method of complex reconstruction key
A sequence encryption and key technology, applied in the field of information security cryptography
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0249] Example 1 Non-overlapping & single metabolic model of progressive bit logic / delayed bit metabolic logic configuration
[0250] Calculation parameters and calculation formulas of embodiment 1 (the calculation formulas are all based on the real number type)
[0251] Chaos computing structure configuration
[0252] 1 As a secret agreement between the encryption / decryption parties, define the structure configuration quantity ctl of embodiment 1 init =640, and make the key length equal to it.
[0253] 2 Define the selection pool and working pool of embodiment 1, and define and generate pseudo-plaintext
[0254] 2.1 Define the selection pool SPool
[0255] Select the pool SPool to satisfy: length(SPool)=2*ctl init (1)
[0256] 2.2 Define the working pool SPool work And load the worker pool SPool work
[0257] Define the initial worker pool SPool work Satisfied: length(SPool work ) = ctl init
[0258] Set the working pool SPool work The initial content of is the ...
Embodiment 2
[0365] Embodiment 2 Progressive chain bit-taking logic / sequentially-promoting metabolic logic and bit-jumping bit-taking logic / extracted bit metabolic logic matching double superposition & double metabolism staggered superposition model embedded in pseudo-random bit twining
[0366] Since only one regeneration key bit sequence group is used in each regeneration key bit sequence group in this embodiment (s=1, see error segment superposition logic structure 4.5), this embodiment identifies the regeneration key bit segment sequence group (bsk1 i,q 、bsk2 i,q 1 and 2 in , refer to 4.5 of the wrong segment superposition logic structure) and the sequence submark of the regeneration key bit segment in the group (bsk1 i,q 、bsk2 i,q The q in , refer to the staggered segment superposition logic structure 4.5) is merged into '1' or '2', and a single buffer area is used instead of the stack.
[0367] Calculation parameter and calculation formula of embodiment 2
[0368] Chaos computing...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com