A multi-chain architecture information sharing system based on blockchain technology
A technology of information sharing and blockchain, which is applied in the field of multi-chain architecture information sharing system, can solve the problems of poor security and sharing cost, and achieve the effect of protecting security, strong consistency, and protecting against theft or tampering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
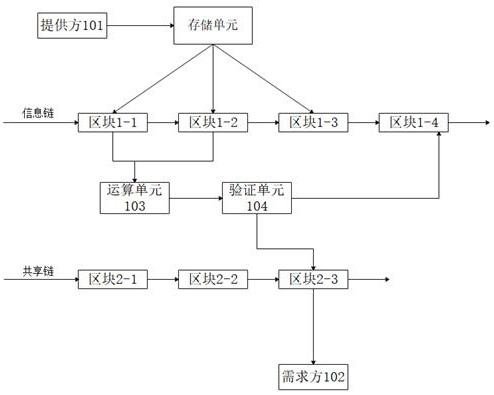
[0038]A multi-chain architecture information sharing system based on blockchain technology, the sharing system includes: a storage unit for storing the shared information of the provider; a computing unit for performing extraction and processing operations on the shared information, and output The result information after the operation; the verification unit is used to verify the validity of the source information, the result information and the encrypted information; the matching unit is used to record the shared information and match the shared information with the information requirements; in the shared system Maintain at least one information chain and more than one sharing chain; the provider is connected to the information chain; the receiver is connected to the sharing chain; the information chain and the sharing chain are established and maintained in the form of an alliance chain; All nodes are allowed to connect to the information chain and the shared chain after they...
Embodiment 2
[0065] In order to ensure that after the provider provides information sharing, information additions, deletions, and modifications can be traced, this embodiment should be understood as at least including all the features of any one of the foregoing embodiments, and further improved on the basis of it:
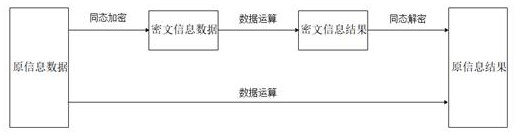
[0066] Each node on the chain, including the provider, has a pair of unique key pairs based on asymmetric encryption, including one public key Pkey and one private key Skey; the private key Skey is automatically encrypted by the node Safekeeping; the public key Pkey is broadcast to the whole chain and can be obtained by all nodes on the chain;
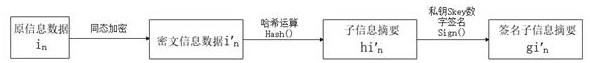
[0067] as attached image 3 , further, when the storage node obtains the encrypted sub-information set Afterwards, a hash function Hash() operation is performed on each piece of encrypted sub-information, so as to obtain a plurality of fixed-length sub-information summaries about the encrypted sub-information , and its sub-informa...
Embodiment 3
[0080] This embodiment should be understood as at least including all the features of any one of the foregoing embodiments, and further improvements on the basis of it:
[0081] Since the data sharing system of the present invention adopts block chain as technical support, it can further match and maintain a plurality of said providers and a plurality of said demand parties for information transactions;
[0082] In this embodiment, in addition to providing the information to be shared, the provider may also target the information I or multiple sub-information i n Set the quotation of information; the quotation includes the use of legal currency for transactions, or specifying equivalent transactions in the form of information exchange; in specific circumstances, the value or value-equivalent information that can be provided by the provider and the demander can be seen;
[0083] After matching the information requirements, the matching node includes matching information quotati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com