Risk rating method and device for security vulnerabilities of information system, equipment and storage medium
An information system and vulnerability technology, which is applied in the field of information system security, can solve the problems of affecting the priority of dealing with vulnerability threats, poor applicability, time-consuming and labor-consuming, etc., to achieve objective and accurate rating results, improve applicability, and reduce subjective factors Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
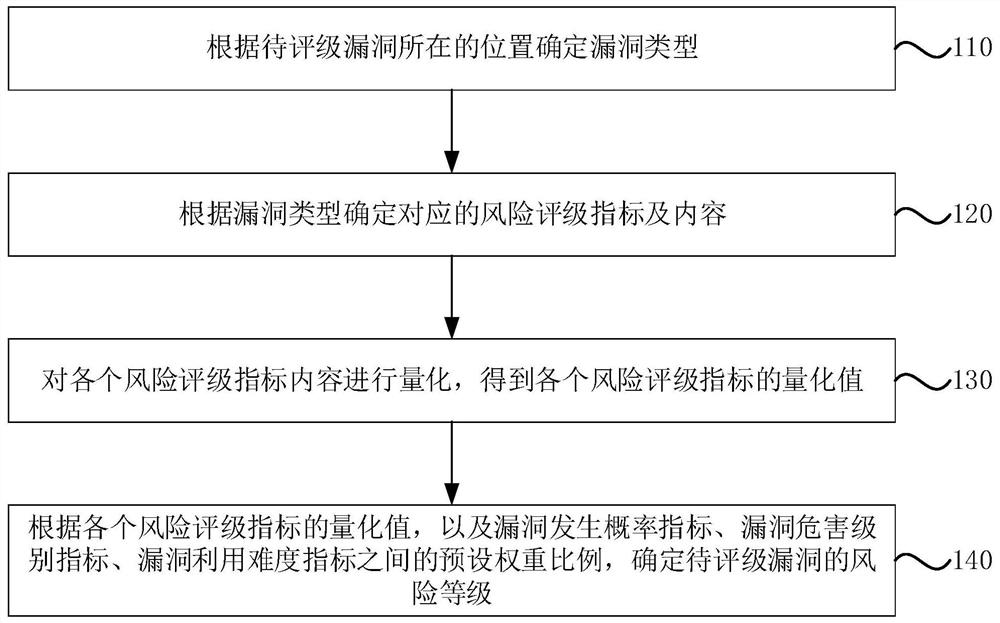
[0027] figure 1 It is a flow chart of a risk rating method for information system security vulnerabilities provided in Embodiment 1 of the present invention. This embodiment is applicable to rapidly and accurately grading the risks of system security vulnerabilities in an information system security processing platform. method, the method can be executed by a risk rating device for information system security vulnerabilities, the device can be implemented by software and / or hardware, the device can be configured in the server of the processing platform, refer to figure 1 , including the following steps:
[0028] Step 110, determine the vulnerability type according to the location of the vulnerability to be rated;
[0029] Among them, there are many types of security vulnerabilities in information systems. Different types of vulnerabilities occur in different locations, and the risk levels they bring are also different. For example, SQL injection vulnerabilities at the user-...
Embodiment 2
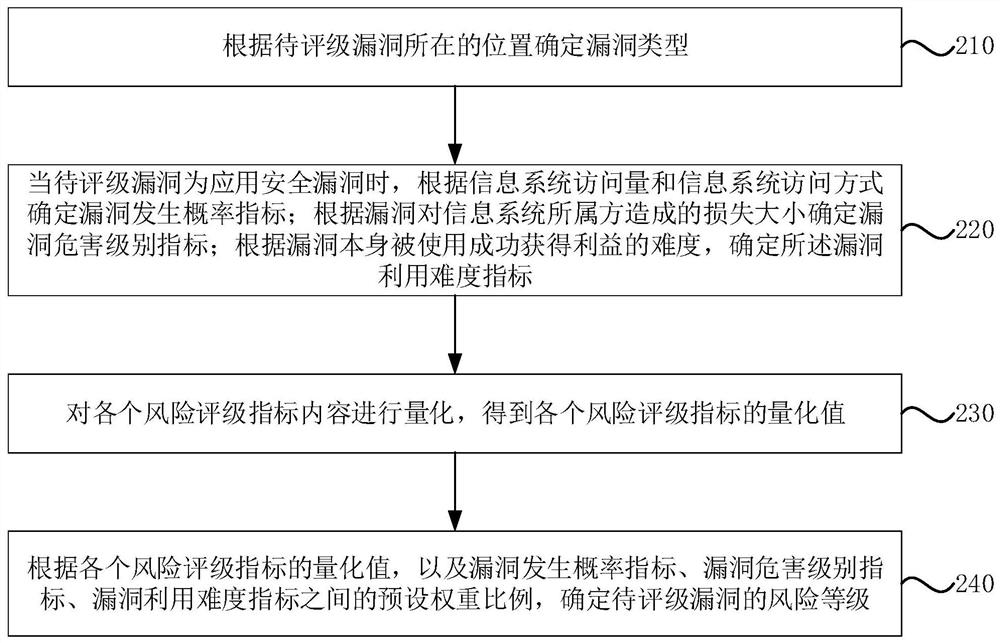
[0052] figure 2 It is a flowchart of a risk rating method for information system security vulnerabilities provided in Embodiment 2 of the present invention. On the basis of the first embodiment above, optionally, refer to figure 2 , determine the corresponding risk rating indicators and content according to the type of vulnerability, including the following steps:
[0053] Step 210, determine the vulnerability type according to the location of the vulnerability to be rated;
[0054] Step 220, when the vulnerability to be rated is an application security vulnerability, determine the vulnerability occurrence probability index according to the information system access volume and information system access method; determine the vulnerability hazard level index according to the loss caused by the vulnerability to the owner of the information system; Using the difficulty of successfully obtaining the benefit, determine the exploit difficulty metric.
[0055]Among them, when the...
Embodiment 3
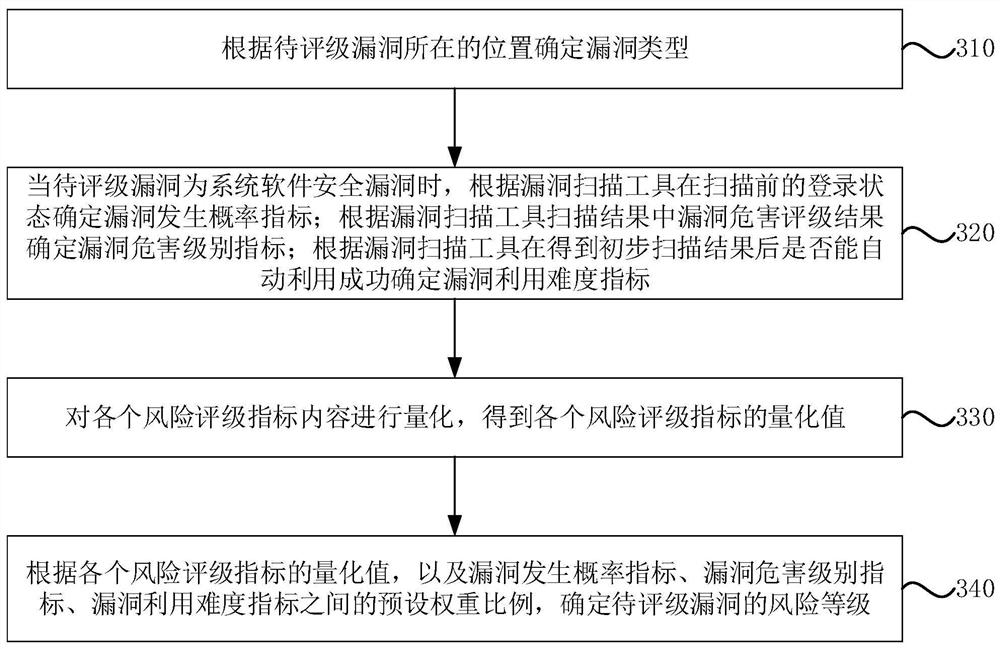
[0067] image 3 It is a flow chart of a risk rating method for information system security vulnerabilities provided in Embodiment 3 of the present invention. On the basis of the above embodiments, optionally, refer to image 3 , determine the corresponding risk rating indicators and content according to the type of vulnerability, and also include the following steps:
[0068] Step 310, determine the vulnerability type according to the location of the vulnerability to be rated;
[0069] Step 320, when the vulnerability to be rated is a system software security vulnerability, determine the vulnerability occurrence probability index according to the login status of the vulnerability scanning tool before scanning; determine the vulnerability hazard level index according to the vulnerability hazard rating result in the vulnerability scanning tool scanning result; Whether the tool can automatically exploit successfully after obtaining the preliminary scanning results determines th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com