Code attribute graph compression method and device for source code vulnerability detection
A technology of vulnerability detection and compression method, which is applied in the field of code attribute map compression of source code vulnerability detection, which can solve the problems of low space-time efficiency, attack, ignoring semantic information, etc., and achieve the effect of improving space-time efficiency and reducing complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
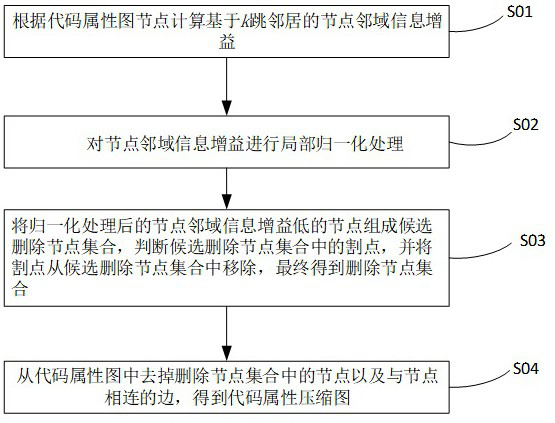
[0032] A code attribute map compression method for source code vulnerability detection, the specific steps are as follows figure 1 shown, including:
[0033] S01. According to the code attribute map node calculation based on the previous K The node neighborhood information gain of jumping neighbors;
[0034] The specific implementation process is: Let the code attribute map ,in represents a set of nodes, Represents the feature matrix of the node, Represents the adjacency matrix of nodes in the code property graph. The code attribute map node type set is , the feature vectors of different types of nodes are in different feature spaces. In order to facilitate the measurement of the distance between node features and the importance of calculation, the present invention first performs feature transformation on the features of nodes, and converts them to the same feature space for differential measurement. The conversion formula as follows:
[0035]
[0036] in, I...
Embodiment 2
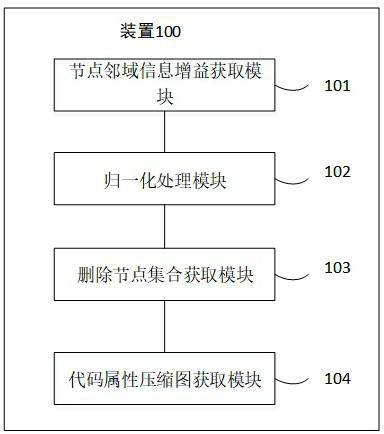
[0059] refer to figure 2 To describe according to the embodiment of the present disclosure and figure 1 The device corresponding to the shown method is a code attribute graph compression device for source code vulnerability detection. The device 100 includes: a node neighborhood information gain acquisition module 101, which is used to calculate nodes based on the previous code attribute graph. K The node neighborhood information gain of jumping neighbors; the normalization processing module 102 is used to perform local normalization processing on the node neighborhood information gain; the deletion node set acquisition module 103 is used to normalize the node neighborhood information gain after normalization Nodes with low information gain form a set of candidate deletion nodes, and determine whether the candidate deletion nodes in the candidate deletion node set meet the requirements: when the candidate deletion node and all the edges connected to it are deleted, the connec...
Embodiment 3
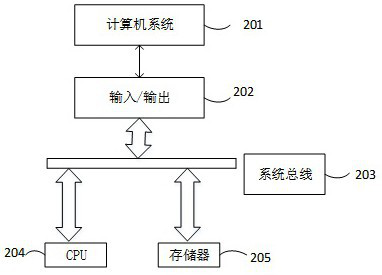
[0062] The device of the embodiment of the present invention can also use image 3 The architecture of the computing device shown is implemented. image 3 The architecture of the computing device is shown. Such as image 3 As shown, a computer system 201, a system bus 203, one or more CPUs 204, input / output 202, memory 205, and the like. The memory 205 can store various data or files used by the computer for processing and / or communication, and program instructions executed by the CPU. The program instructions include executing the code attribute map compression method for source code vulnerability detection described in Embodiment 1. image 3 The architecture shown is just an example, and it should be adjusted according to actual needs when implementing different devices image 3 One or more components in .
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com