Malicious webpage identification and detection method based on static field, computer and storage medium
A technology for malicious web pages and detection methods, applied in the field of malicious web page identification and detection, can solve the problems of fingerprints occupying too much space resources, inability to apply real-time detection, and one-sided plain text information, etc. short time effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
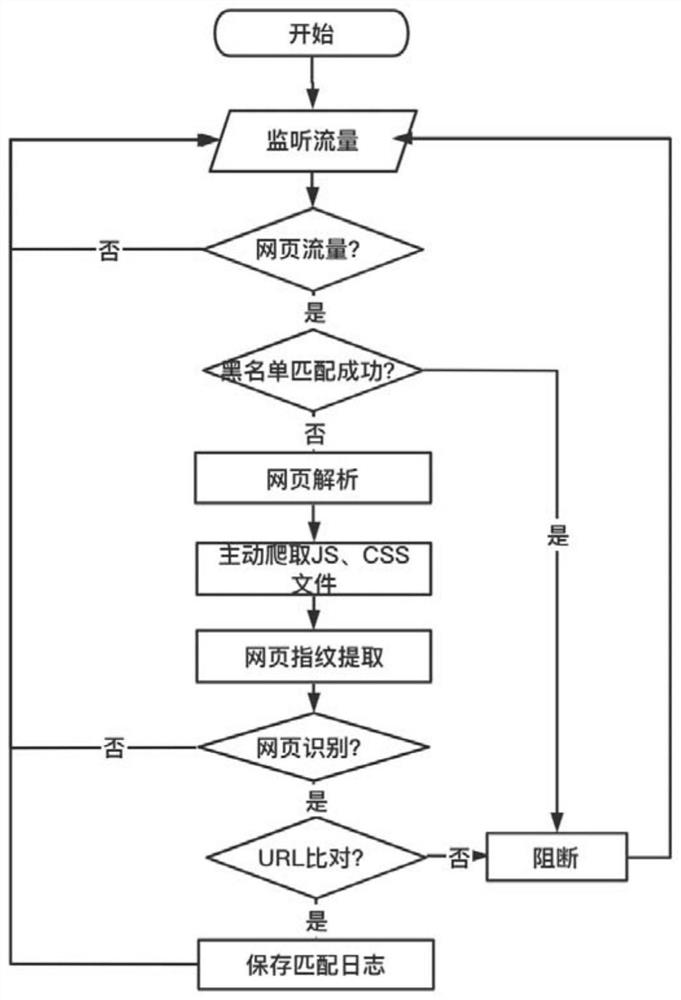
[0053] Embodiment 1, with reference to Figure 1-3 To illustrate this embodiment, the present invention provides a method for identifying and detecting malicious webpages based on static domains, including the following steps:
[0054] Step 1, monitor the webpage traffic in real time, and extract the URL address of the HTTP header;
[0055] Step 2. Match the URL address described in step 1 with the URL address stored in the blacklist library; if the match is successful, block the traffic, and if the match fails, perform step 3;
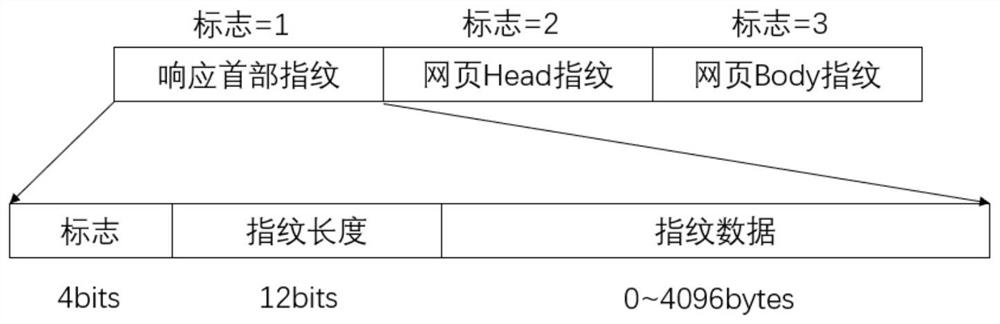
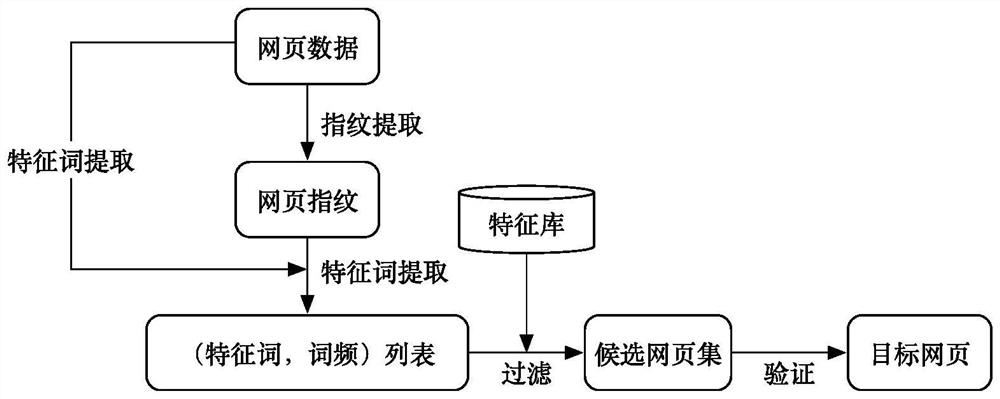
[0056] Step 3, parsing the webpage traffic of matching failure; the parsing method of the present invention can improve the efficiency in the webpage parsing process, can carry out a series of response processing and avoiding for the grammatical and format errors existing on the webpage, and can also be resolved by setting the maximum parsing depth Limit the running time of the program and de-dry the deep nodes. Specifically include the following st...
Embodiment 2
[0100] Embodiment 2. A computer. The computer device of the present invention may be a device including a processor and a memory, such as a single-chip microcomputer including a central processing unit. Moreover, when the processor is used to execute the computer program stored in the memory, the steps of the above-mentioned recommendation method based on CREO software that can modify the recommendation data driven by the relationship are realized.
[0101] The so-called processor can be a central processing unit (Central Processing Unit, CPU), and can also be other general-purpose processors, digital signal processors (Digital Signal Processor, DSP), application specific integrated circuits (Application Specific Integrated Circuit, ASIC), off-the-shelf Programmable gate array (Field-Programmable Gate Array, FPGA) or other programmable logic devices, discrete gate or transistor logic devices, discrete hardware components, etc. A general-purpose processor may be a microprocesso...
Embodiment 3
[0103] Embodiment 3, computer-readable storage medium
[0104] The computer-readable storage medium of the present invention can be any form of storage medium read by the processor of the computer device, including but not limited to non-volatile memory, volatile memory, ferroelectric memory, etc., computer-readable storage A computer program is stored on the medium, and when the processor of the computer device reads and executes the computer program stored in the memory, the steps of the above-mentioned modeling method based on CREO software that can modify the relationship-driven modeling data can be realized.
[0105] The computer program includes computer program code, which may be in source code form, object code form, executable file or some intermediate form, and the like. The computer-readable medium may include: any entity or device capable of carrying the computer program code, a recording medium, a U disk, a removable hard disk, a magnetic disk, an optical disk, a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com