A physical layer key agreement negotiation method and system based on channel estimation
A channel estimation and consistency technology, applied in baseband systems, channel estimation, baseband system components, etc., can solve problems such as information leakage, inability to bit error detection and correction, and inability to generate symmetric keys, achieving good fault tolerance, The effect of high security and strong implementability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
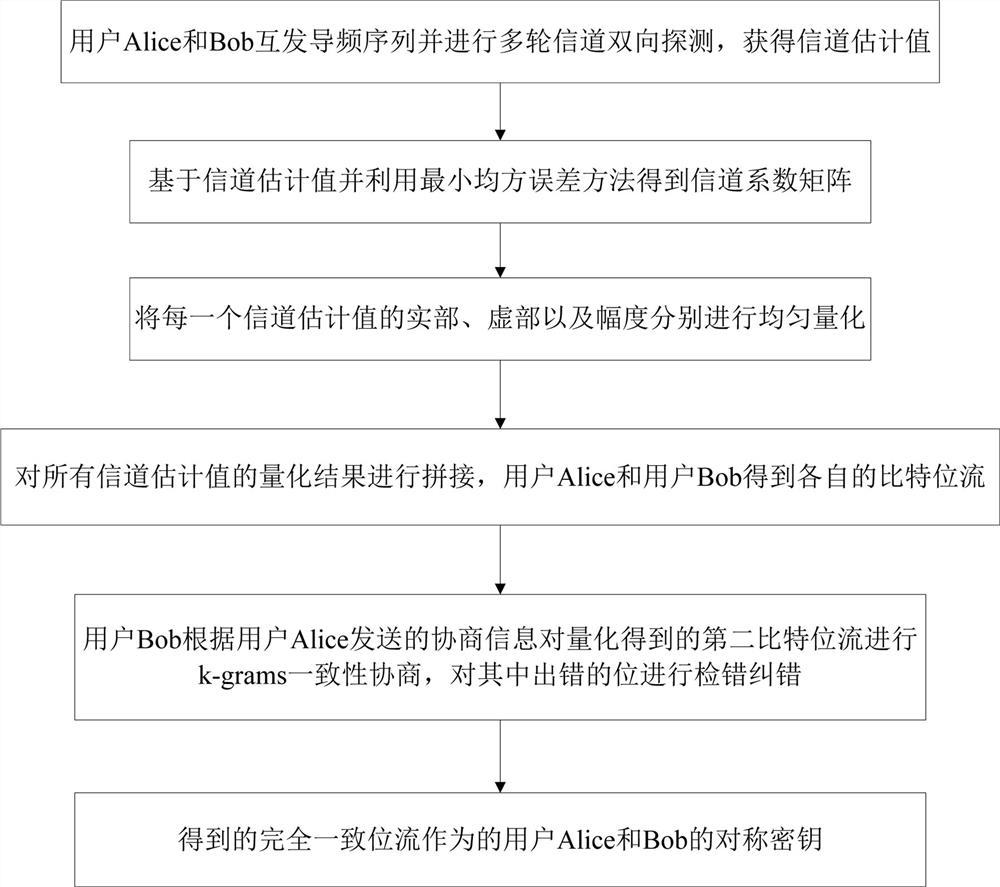
[0062] like figure 1 As shown, this embodiment provides a physical layer key consistency negotiation method based on channel estimation, the method is used in an Internet of Things communication system, and specifically includes the following steps:
[0063] S1: Channel estimation processing: The channel estimation processing in this embodiment requires both parties in legitimate communication to exchange pilot sequences to complete the channel estimation process;
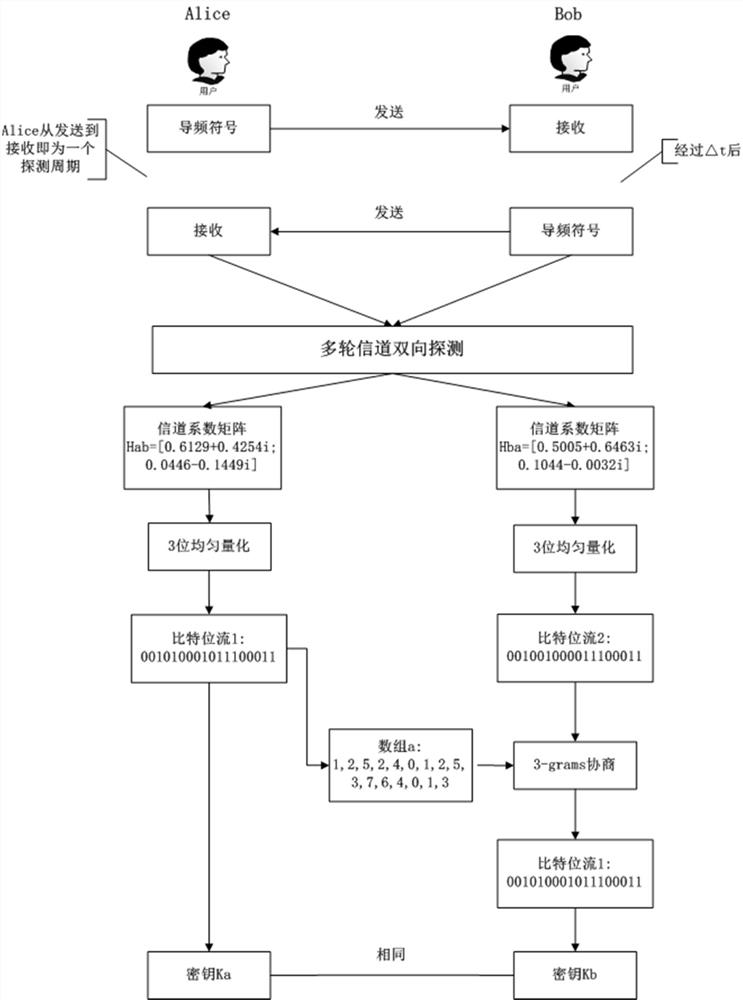
[0064] In the communication system, legitimate communication users Alice and user Bob have one transmitting antenna and multiple receiving antennas. The data communication adopts the half-duplex communication transmission mode. User Alice sends a pilot symbol to Bob, and Bob receives it after time t1. Bob experiences a transceiving transition time Δt, and then sends a pilot symbol to Alice, and then Alice receives it, and time t2 elapses. At this point, a detection cycle is completed, and t1+△t+t2 is required to...
example 1-1
[0094] Example 1-1 (using quantized bitstream):
[0095] (1) Alice obtains the key bit stream 1 through the quantization stage: '001010001011100011', at this time, Alice performs the hash calculation according to the hash function defined above with the window number 3 as the limit, and stores the calculation result in the array a and Send to Bob, the total length of the bit stream sum=18;
[0096] (2) Suppose Bob obtains the key bit stream through the quantization stage as: '001001000011100011', the calculation method will not be repeated, and the obtained array b is 1, 2, 4, 1, 2, 4, 0, 0, 1, 3, 7, 6, 4, 0, 1, 3;
[0097] (3) At this time, Bob gets the array a and starts a one-to-one comparison, and finds that the first digit of the subscript is the same, then the bit stream header does not need to be adjusted, and continues to compare and finds that the subscript c=3 digit is different, then the Directly perform 0 / 1 correction on the c+2th bit. At this time, the bit strea...
Embodiment 2
[0116]This embodiment provides a physical layer key consistency negotiation system based on channel estimation, including: a channel estimation value acquisition module, a channel coefficient matrix acquisition module, a uniform quantizer, a splicing module, and a consistency negotiation module;
[0117] Users Alice and Bob on both sides of the communication exchange pilot sequences and perform multiple rounds of two-way channel detection, and the channel estimation value obtaining module is used to obtain the channel estimation value;
[0118] Users Alice and Bob both have multiple receiving antennas to form multiple-input multiple-output channels, and the channel coefficient matrix acquisition module is used to obtain the channel coefficient matrix based on the channel estimation value and using the minimum mean square error method;
[0119] In this embodiment, the uniform quantizer is used to uniformly quantize the channel estimation value, and the real part, imaginary part ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com