Safety protection method facing to mobile agent network management
A mobile agent and security protection technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as damage to resources, unavailability, illegal changes in network configuration and management parameters, and achieve resource protection and a safe operating environment Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0097] The present invention will be described in more detail according to the drawings and embodiments below.
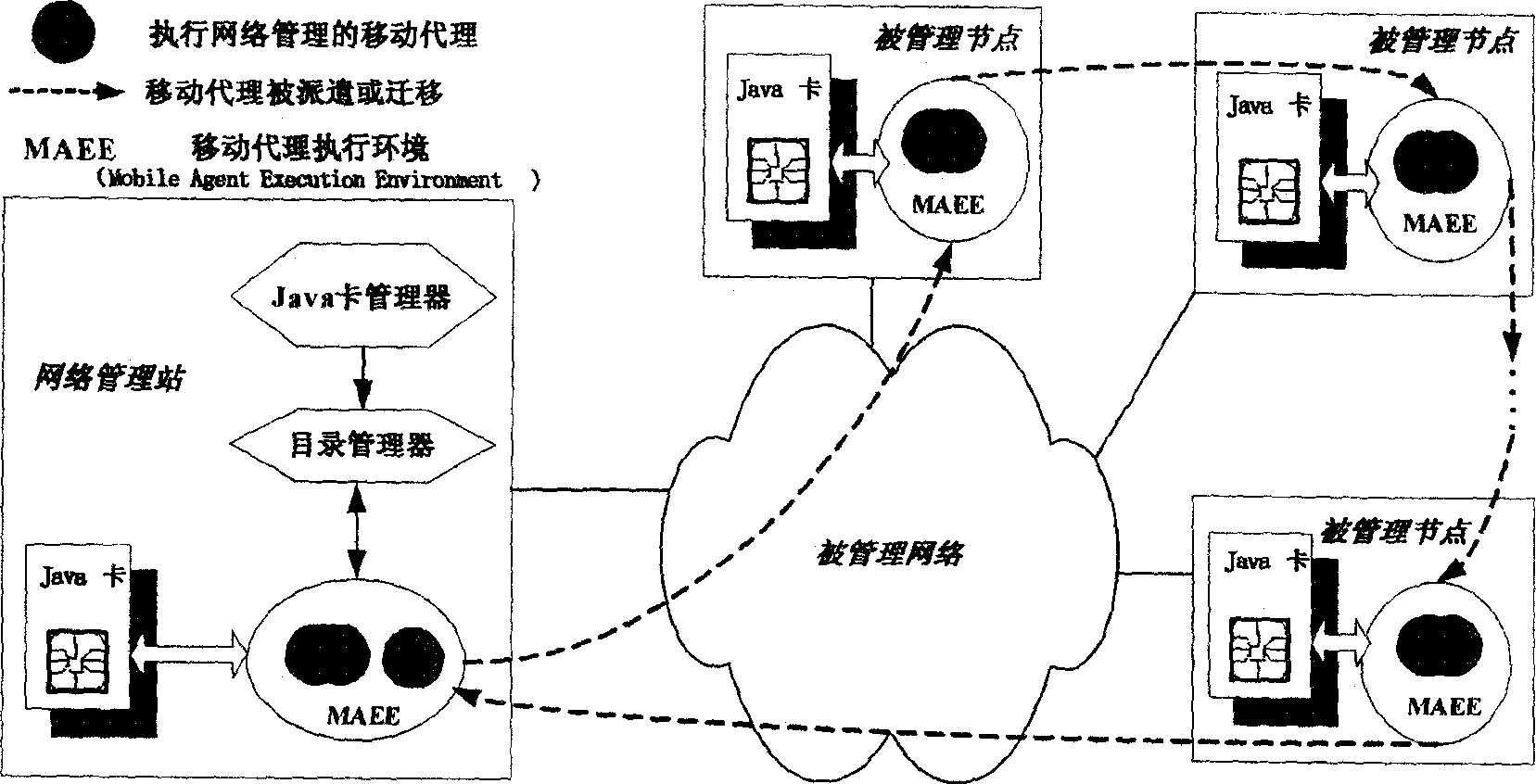
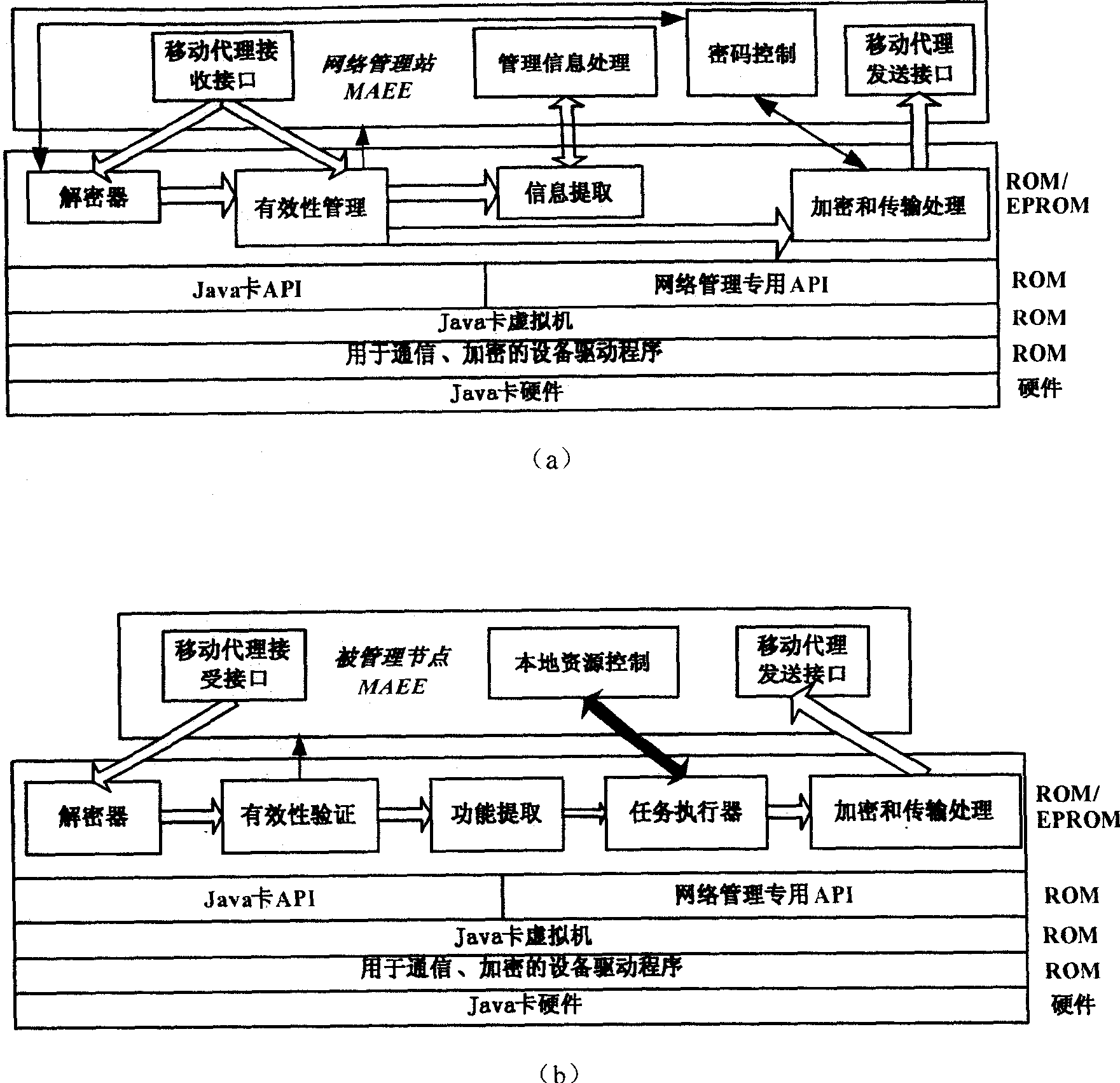
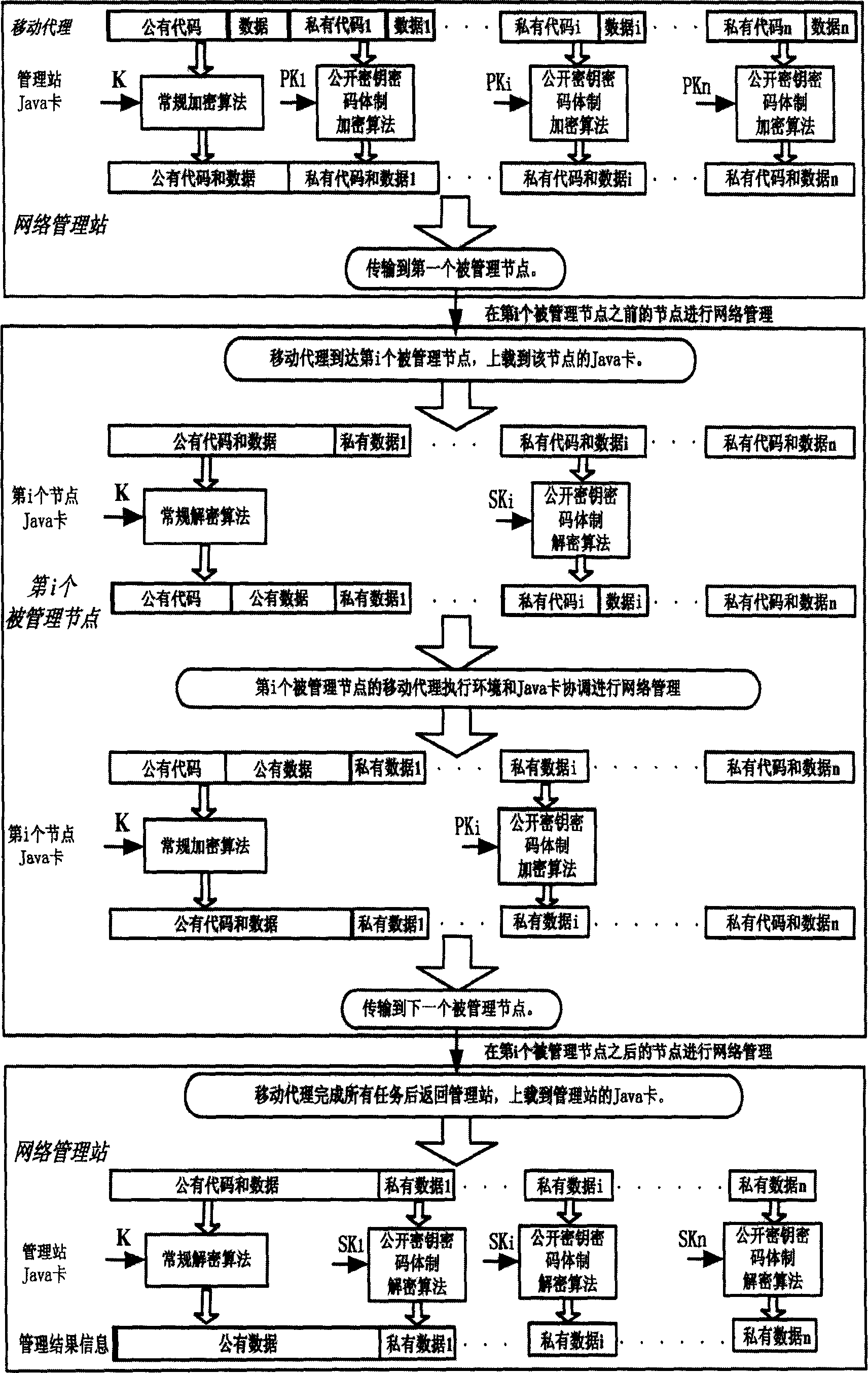
[0098] according to figure 1 and figure 2 , the present invention is a systematic mobile agent network management-oriented security protection method, from the creation of the mobile agent in the network management station, to the execution of network management tasks in the managed node, and finally returning to the network management station to submit information, the entire network management process are all protected.
[0099] For the convenience of description, we assume that the mobile agent performing network management tasks needs to visit n managed nodes, and the Java card of each managed node stores the key of the conventional encryption and decryption algorithm and the two involved in the encryption and decryption algorithm of the public key cryptosystem. A key, let the key of the conventional encryption and decryption algorithm be K, and the encryptio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com