Security element for marking or identifying objects and living beings
a security element and living being technology, applied in the field of security elements for marking, authenticating, or identifying objects, can solve the problems of inability to determine authenticity or only with great effort, the assignment of certain security elements remains an unresolved problem, and the forgery cannot be distinguished from the original, so as to improve forgery security, accelerate the formation of crackles, and improve the effect of forgery
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
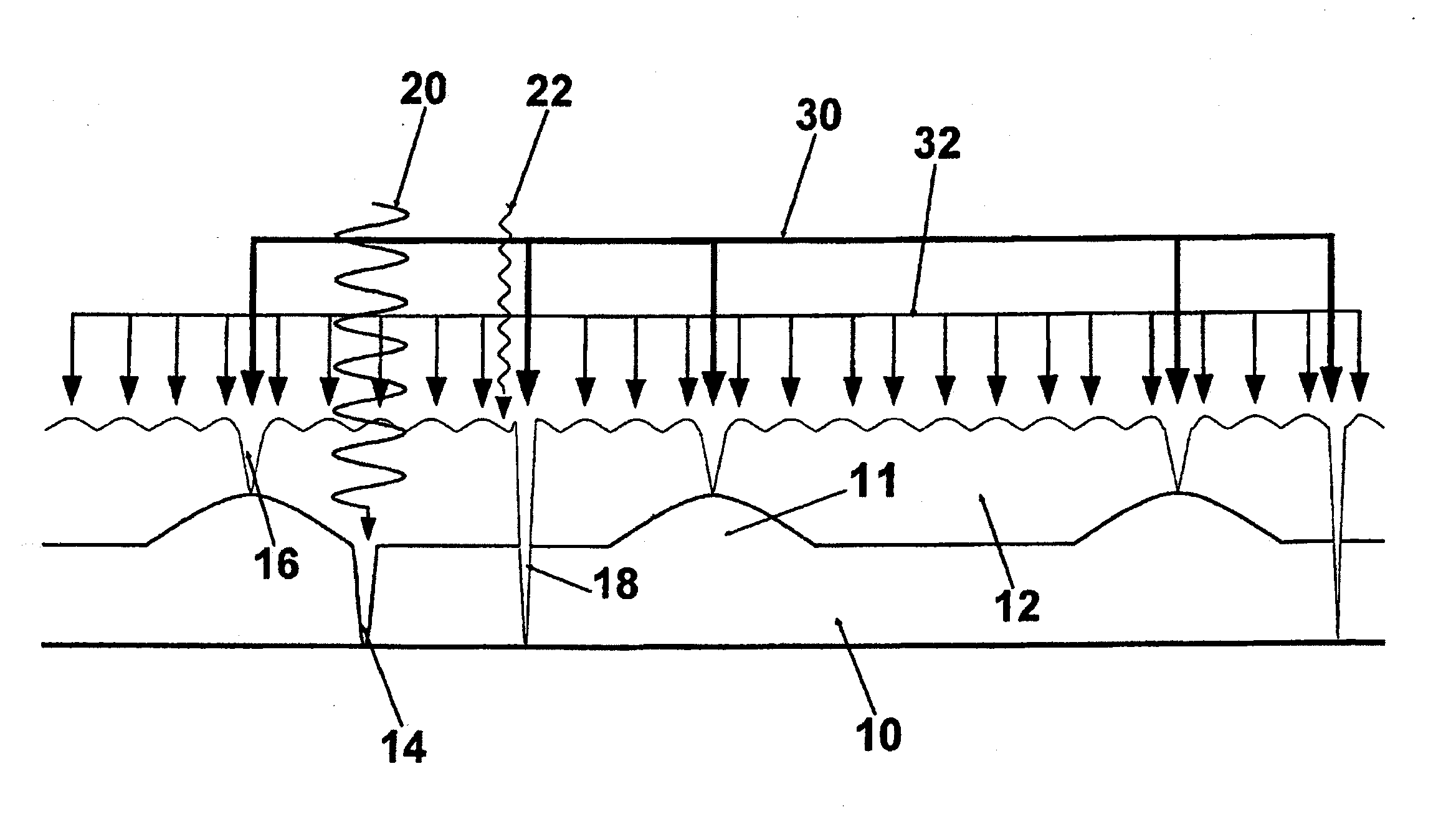
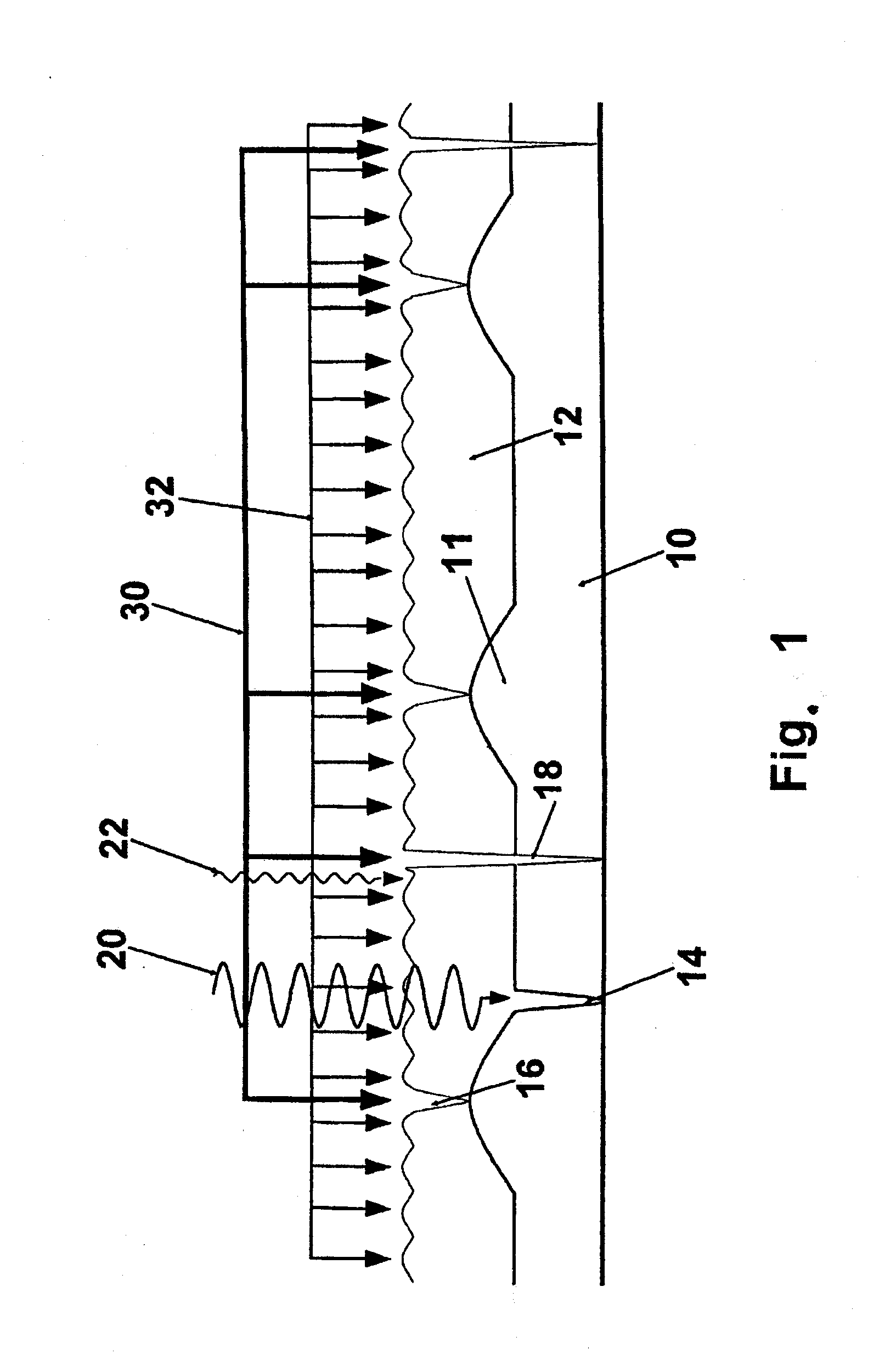
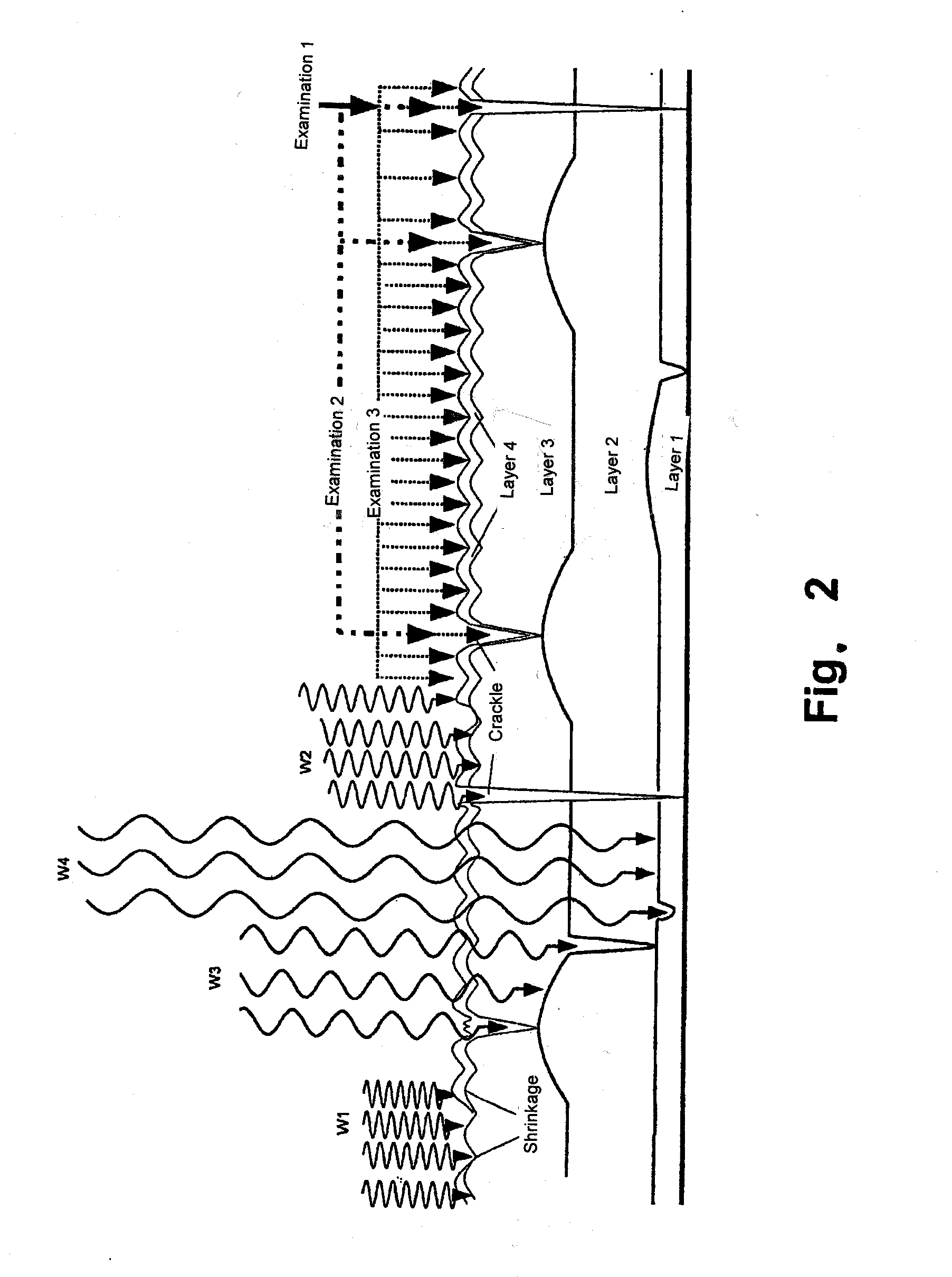
[0081]In FIG. 1, two crackle layers 10, 12 are arranged one above the other. The individual crackle layers 10, 12 form varyingly pronounced tears or cracks 14, 16, 18. Depending on the extent, the tears of the topmost layer 12 can pass through to the underlying layer 10 as a single tear (cf. tear 18). Tears 16 can arise in the topmost layer 12 because of the drying process. Such tears can arise, for example, also by the drying or shrinking 11 of the underlying layer 10. Naturally, also an overlying layer can influence an underlying layer and cause stress cracks. Depending on the employed method, tears can be introduced selectively in this way to create a crackle. If a layer shrinks, it can also form furrows, which are similarly characteristic like crackle structures. As a result, shrinkages can also be used as a security feature, apart from or in addition to the crackle structures.
[0082]The individual layers 10, 12 can be scanned by different measuring methods for data acquisition o...
PUM
| Property | Measurement | Unit |
|---|---|---|
| wavelength | aaaaa | aaaaa |
| wavelength | aaaaa | aaaaa |
| wavelengths | aaaaa | aaaaa |
Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com