Hybrid media access control method based on collaborative collision decomposition
A conflict resolution and hybrid technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problems of wasting time slots and unable to eliminate idle time slots
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0065] A hybrid media access control method based on cooperative conflict resolution in a wireless network, the implementation process of which is as follows:
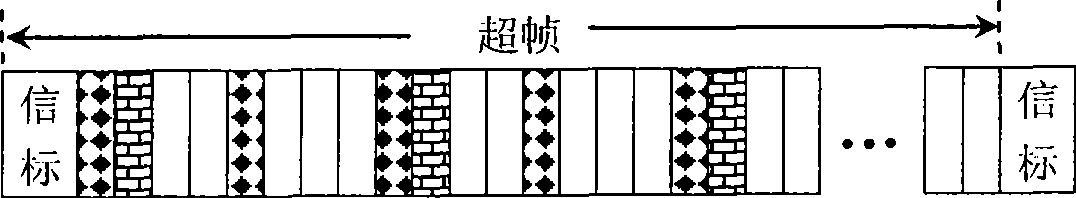
[0066] Step 1: Time-division duplexing is adopted, and the channel is time-slotted. The settings are as follows: the channel is divided into equal-length time slots in time, and the system periodically sends beacon frames. Two adjacent beacon frames construct a superframe. superframe contains time slots, N O Take an integer between 1 and 8. The beacon frame is used for broadcasting system messages, timing and synchronization. Each time slot is set with a listening sub-slot at the head, a confirmation sub-slot at the end, and a transmission sub-slot in the middle. After the listening sub-slot, confirmation sub-slot and transmission sub-slot, a protection sub-slot follows respectively,
[0067] Step 2: The non-competing service node sends the non-competing service data frame by using the time division multiple access ...
Embodiment 2
[0107] The method of the present invention is aimed at the time division duplex system, but it can also be applied to the frequency division duplex system. Example 2 takes Figure 6 As an example, the resolution process of a 6-node conflict is introduced in detail, and the resolution process of conflicts of other numbers is similar.
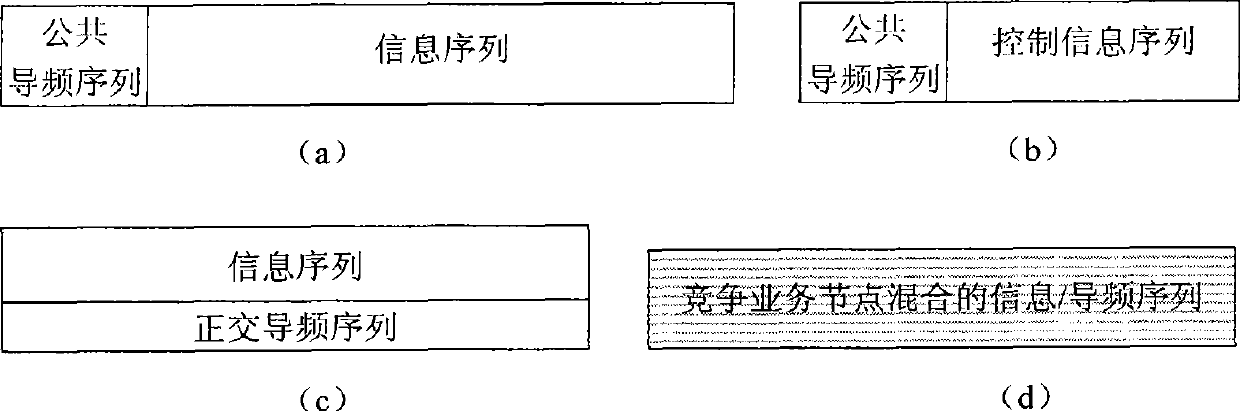
[0108] The non-competing service node in the method of the present invention adopts the time division multiple access mode, and the system first specifies an allocation time slot with a period of 5 time slots for a non-competition service node, and the allocated time slot number is broadcasted by a beacon frame. Next, consider the transmission process of competing services. First, the competing service node sends a connection request, and the access point allocates an orthogonal pilot sequence to the node, and rejects the node's connection request if the orthogonal pilot sequence has been allocated. Then, the nodes that have established the con...
Embodiment 3
[0146] The performance of the method of the invention is examined here. Assuming that the arrival of data packets of competing service nodes obeys the Poisson distribution, the total arrival rate is λ packet per time slot, which belongs to the fixed rate service, all nodes use the same modulation order, and the competing service nodes and access points have sufficient buffer space. The channel is block fading, that is, the channel state in one time slot is quasi-static, and the channel state in adjacent time slots is irrelevant.
[0147] First define the system throughput, which is defined as the average number of data packets that can be successfully received in a unit time slot. The standard slotted ALOHA throughput is R 时隙ALOHA (λ)=λe -λ .
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com