Data authentication method and system using same
A data authentication and authentication device technology, applied in the field of information security, can solve problems such as loss or embezzlement of certificates, potential safety hazards, transaction tampering, etc., and achieve the effects of ensuring non-tampering, improving security, and ensuring confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] In order to further illustrate the technical means adopted by the present invention and its effects, the following describes in detail in conjunction with preferred embodiments of the present invention and accompanying drawings.
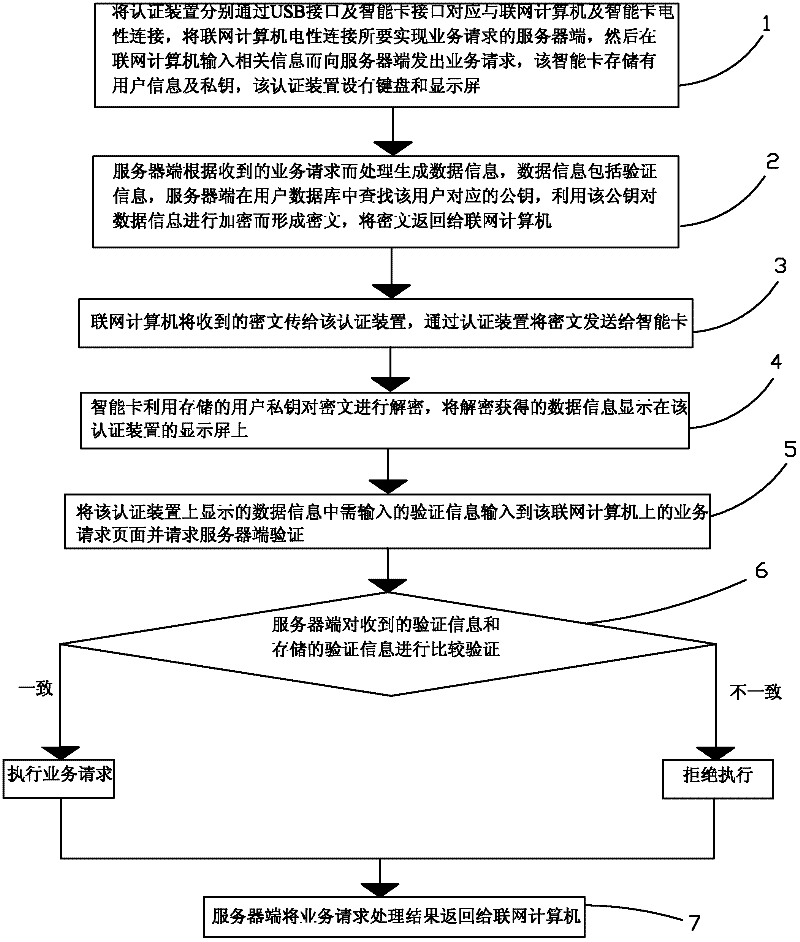
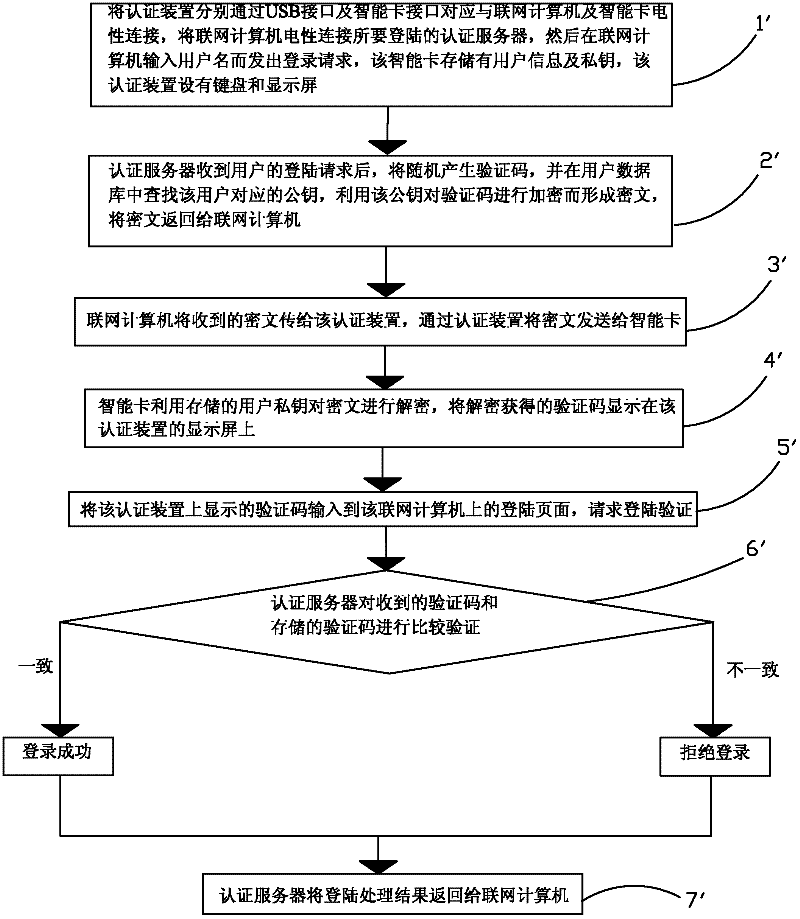
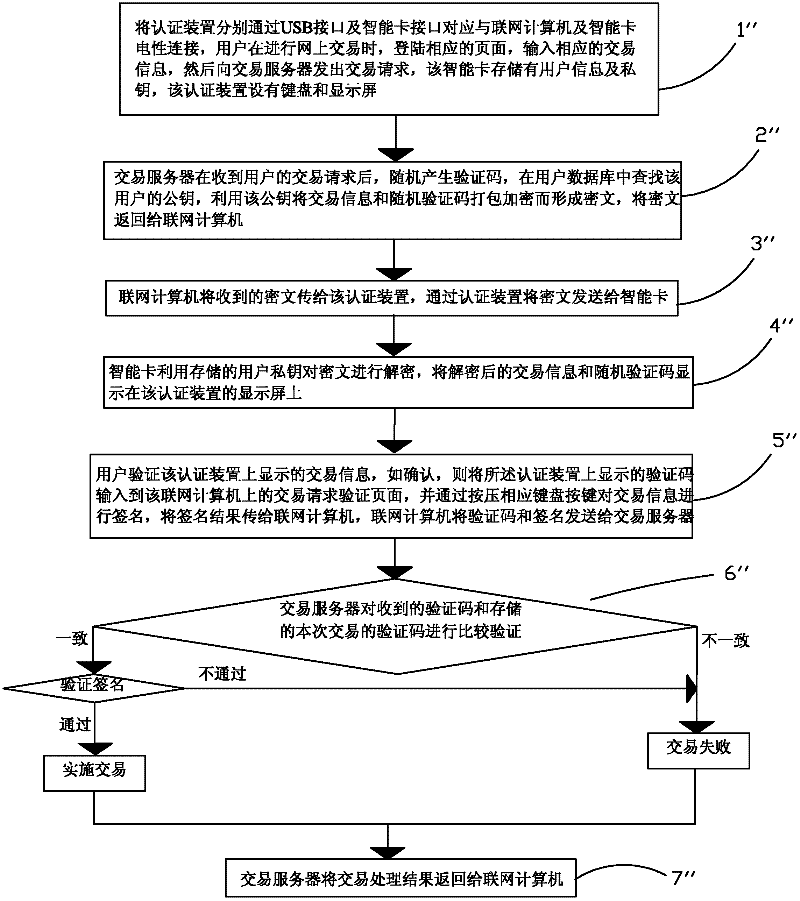
[0043] Such as figure 1 As shown, the present invention provides a data authentication method, which includes the following steps:
[0044] Step 1. Electrically connect the authentication device to the networked computer and the smart card through the USB interface and the smart card interface respectively, and electrically connect the networked computer to the server to realize the service request, and then input relevant information on the networked computer to send the service to the server request, the smart card stores user information and a private key, and the authentication device is provided with a keyboard and a display screen.
[0045] Step 2. The server side processes and generates data information according to the received busine...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com