DPA (Differential Power Analysis) security evaluation and countercheck method and device
A security and analysis method technology, which is applied in the field of DPA security evaluation and countermeasures and its devices, can solve problems such as difficulty in ensuring chip security, and achieve the effect of realizing intelligence and improving analysis capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
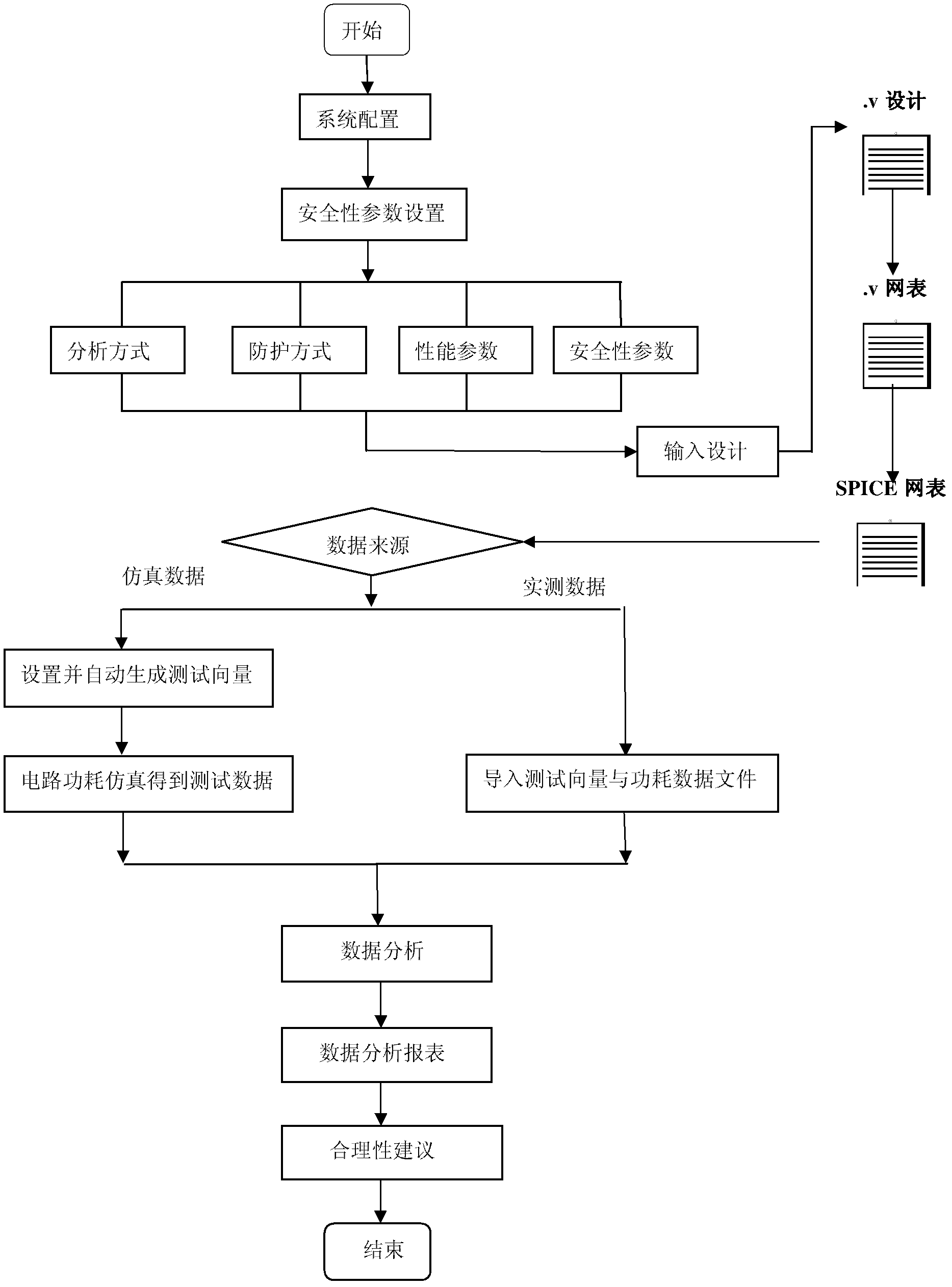
[0057] A DPA security evaluation and confrontation method, comprising the following steps:
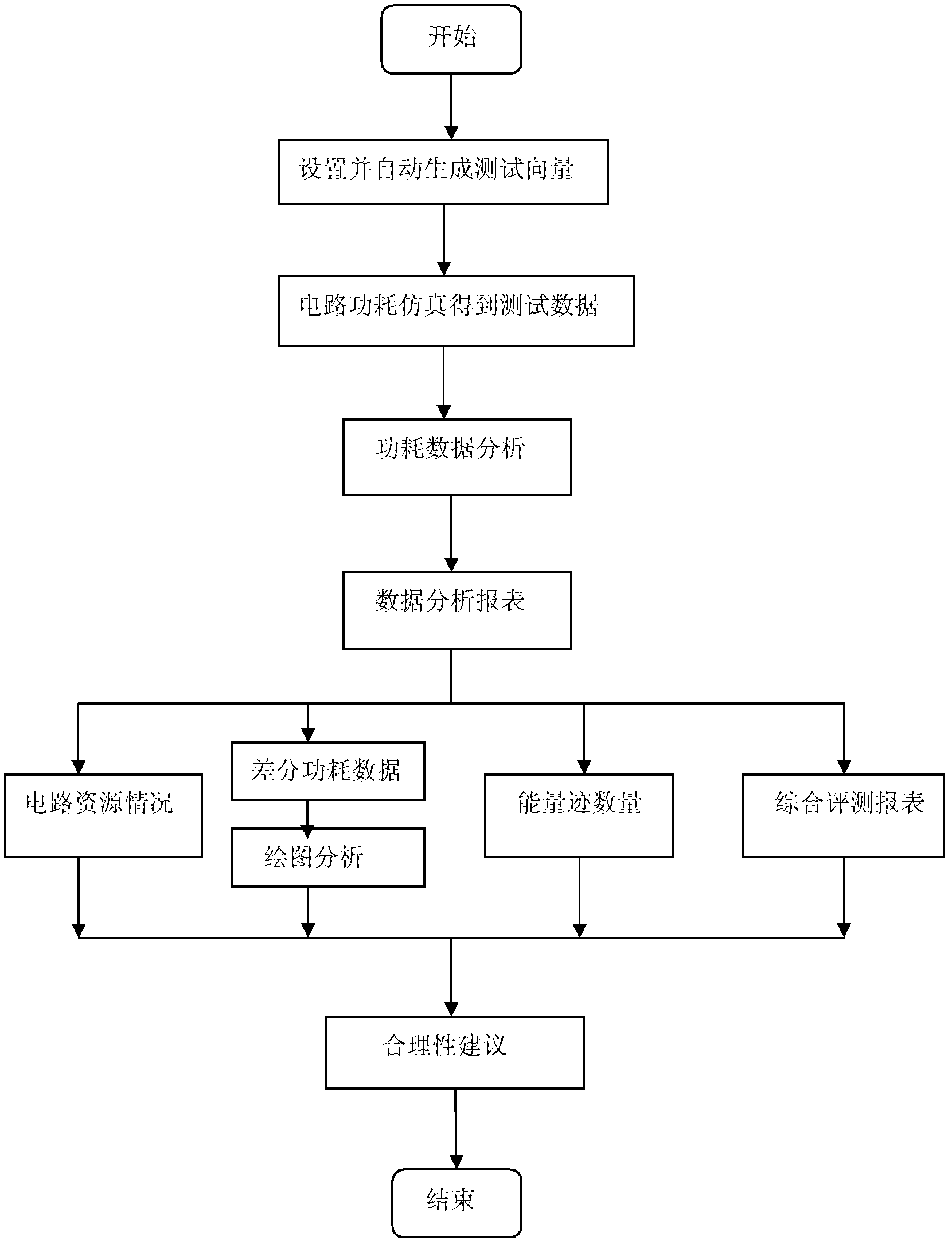
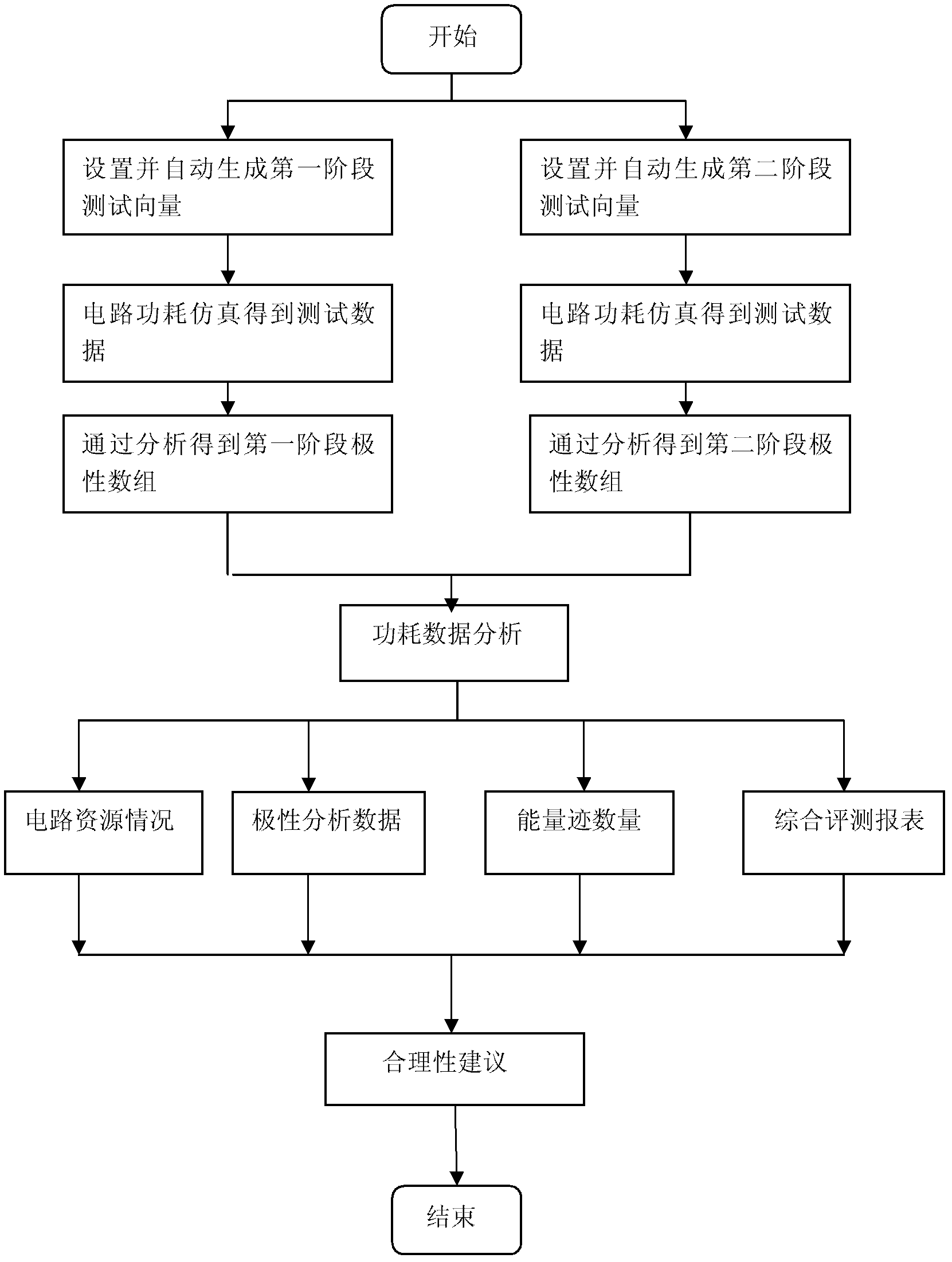
[0058] Step 1, system configuration by the system configuration module: including fitting tool settings, component library settings and tool path settings used in the analysis process; tool settings include: HSPICE, Design Compiler, HSIM component library settings include: HSPICE, Design Compiler , component library corresponding to HSIM; tool path settings include: installation path corresponding to HSPICE, Design Compiler, and HSIM; confrontation methods include: WDDL confrontation method, KANO confrontation method, user-defined method; performance parameters in the analysis report include: circuit resources Situation, signal-to-noise ratio; security parameter settings include: correlation coefficient, conditional entropy and mutual information, and number of energy traces.
[0059] Step 2, parameter setting is performed by the parameter setting module: including analysis mode, conf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com