Verification method of user identity and apparatus thereof
A user identity and verification method technology, applied in the field of user identity verification methods and devices, can solve problems such as low business processing efficiency and waste of system resources, and achieve the effects of improving verification flexibility, saving system resources, and improving verification experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
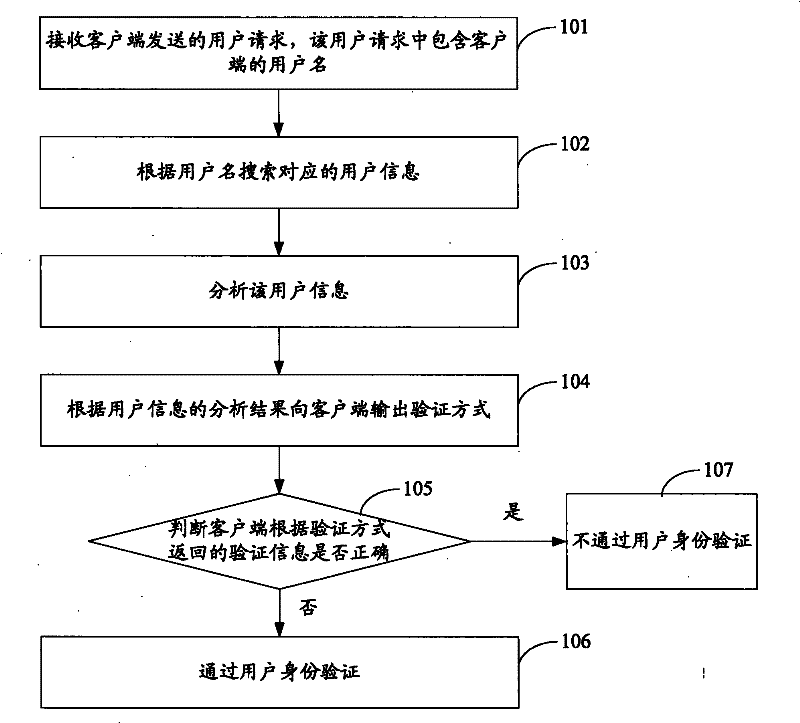
[0028] see figure 1 , which is the flow chart of the first embodiment of the method for verifying the identity of the user in this application:
[0029] Step 101: Receive a user request sent by the client, where the user request includes the user name of the client.
[0030] Before using the services provided by a certain website, the user first needs to register as a member of the website. During the registration, the website server will record the user’s user name, password and other registration information; The user sends corresponding verification information such as keys and tokens for the user to verify whether the service is legal each time the user uses the service, and the verification information is also associated with the corresponding user through the user name.
[0031] When the user logs in to the website through the client and chooses to use a certain service, a verification request is sent to the server, and the verification request includes the user's usern...
no. 2 example
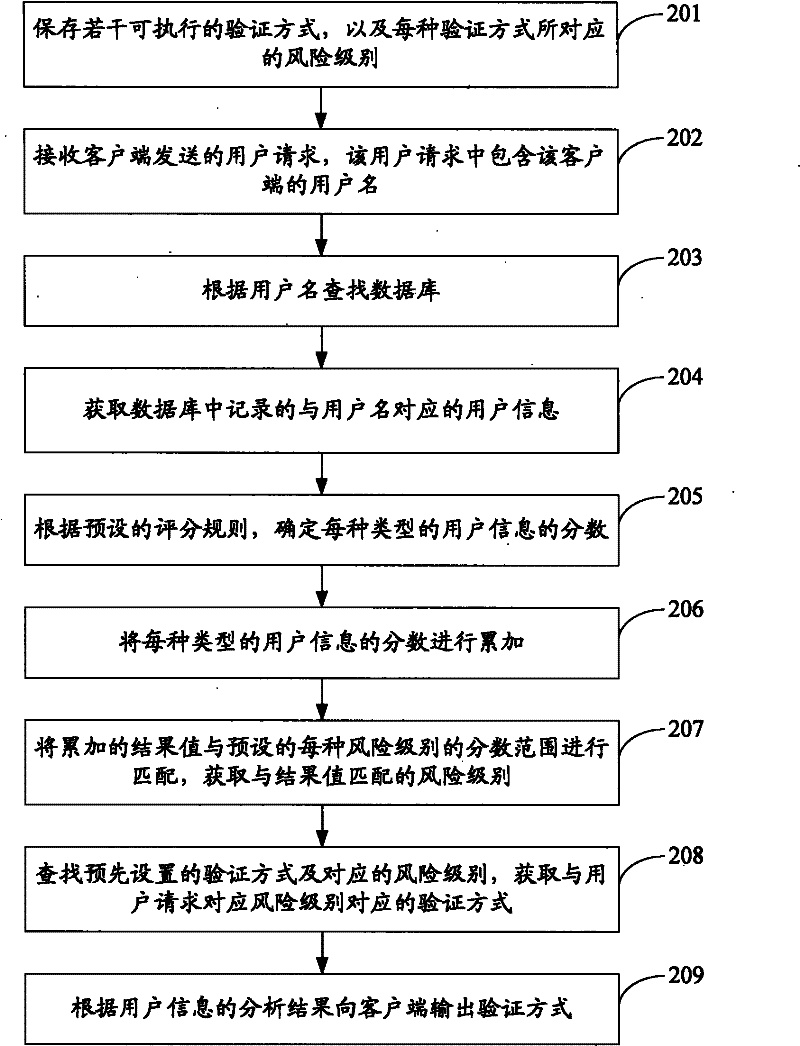
[0045] see figure 2 , which is the flow chart of the second embodiment of the method for verifying the user identity of the present application:
[0046] Step 201: Save several executable verification methods and the risk level corresponding to each verification method.
[0047]In this embodiment of the application, instead of simply outputting a fixed verification method to the user according to the business type and user type, a corresponding risk level is set for each verification method, so that the corresponding verification method can be subsequently output according to the risk level requested by the user this time.
[0048] For example, in the embodiment of this application, three verification methods and their corresponding risk levels can be set, as shown in Table 1 below:
[0049] Table 1
[0050] Ways of identifying
risk level
high
safe question
middle
PIN
Low
[0051] Step 202: Receive a us...
no. 3 example
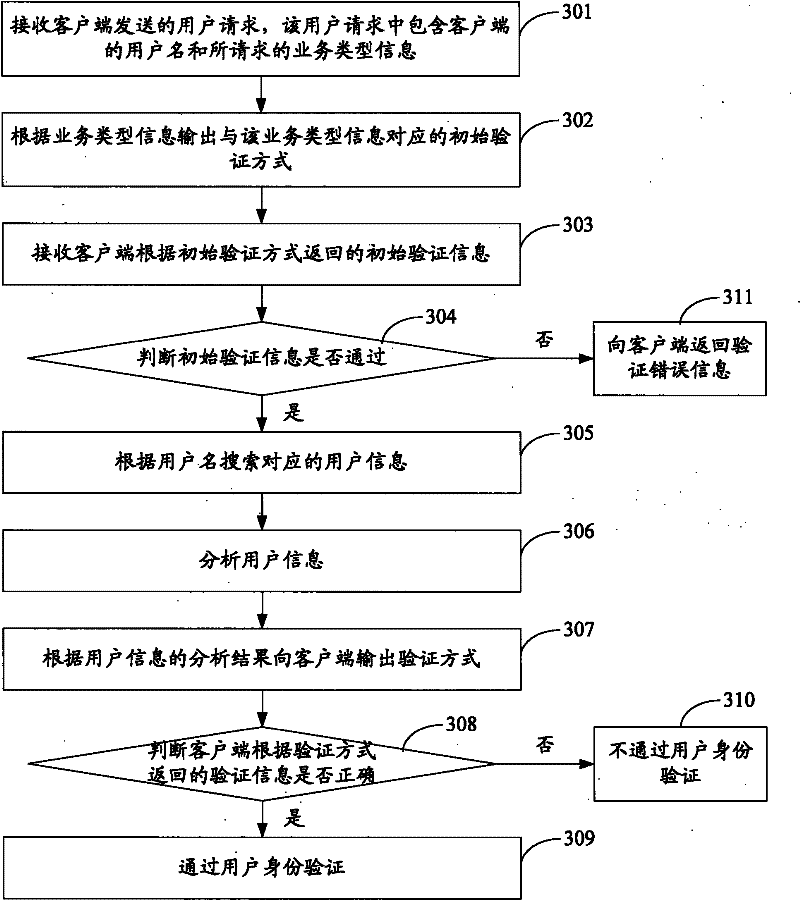
[0077] see image 3 , which is the flow chart of the third embodiment of the verification method output method of this application:
[0078] Step 301: Receive the user request sent by the client, the user request includes the user name of the client and the requested service type information.
[0079] Step 302: output an initial verification method corresponding to the service type information according to the service type information.
[0080] The difference from the previous embodiments is that in this embodiment, instead of directly obtaining the corresponding authentication method based on user information, secondary authentication is performed in combination with the business type, that is, it is compatible with the existing authentication methods based on the business type or user type.
[0081] In this embodiment, the server can pre-set a corresponding verification method for each type of service, and after receiving the verification request, first output the verificat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com