Protocol-independent network redundant flow eliminating method
A redundant traffic, protocol-independent technology, used in data exchange networks, special data processing applications, instruments, etc., can solve problems such as not working well, improve the matching success rate, reduce storage capacity requirements, and save storage resources. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
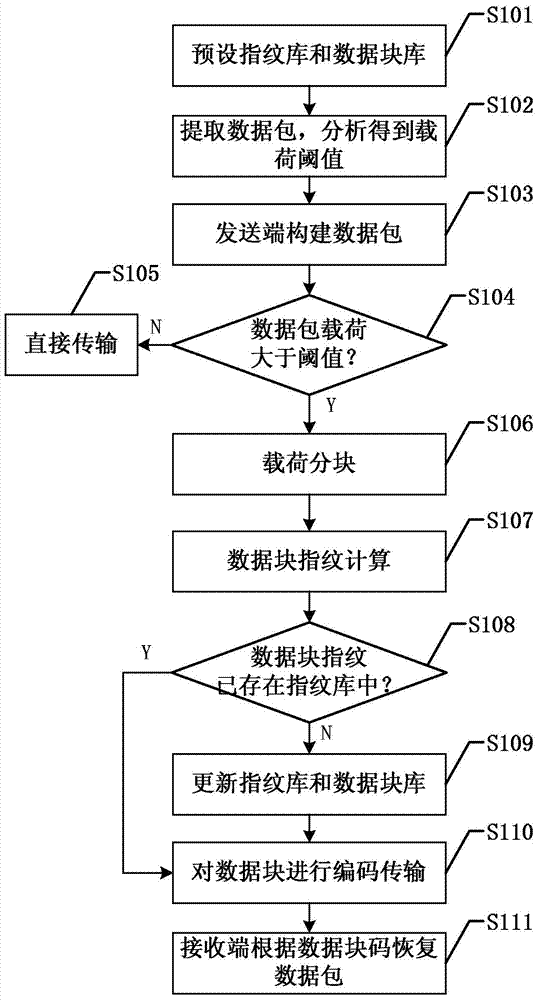
[0043] figure 1 It is a flow chart of a specific embodiment of the protocol-independent network redundant traffic elimination method of the present invention. Such as figure 1 As shown, the protocol-independent network redundant traffic elimination method of the present invention comprises the following steps:
[0044] S101: Preset fingerprint library and data block library:
[0045]In the present invention, what is stored in the fingerprint library is the fingerprint corresponding to the data block, that is, the unique identifier of the data block, and what is stored in the data block library is the data block that will be repeatedly transmitted in the network. Therefore, to adopt the communication network of the present invention, a fingerprint library and a data block library need to be pre-set in the network, and the fingerprints in the fingerprint library correspond to the data blocks in the data block library one by one. The physical storage devices of the fingerprint...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com