Criminal suspect mining association method and system based on social network analysis
A social network and suspect technology, applied in the field of public security crime network analysis, can solve problems such as no good solutions, and achieve good scalability, tight integration, and fast system operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
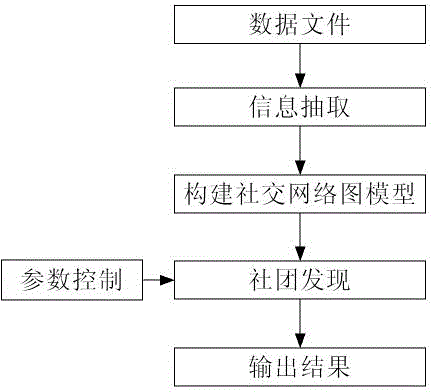
[0025] The technical solutions provided by the present invention will be described below in conjunction with the accompanying drawings and specific examples, using telephone communication records as input data.
[0026] The system involved in the present invention mainly includes four modules: a data analysis and extraction module, a social network building module, a community discovery module, and a result output module. When the system is working, each module performs the following work:
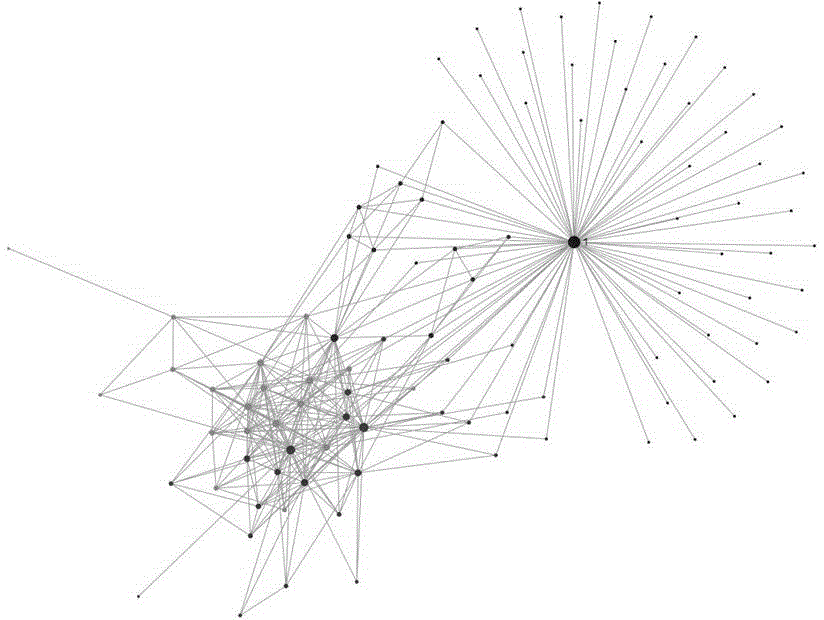
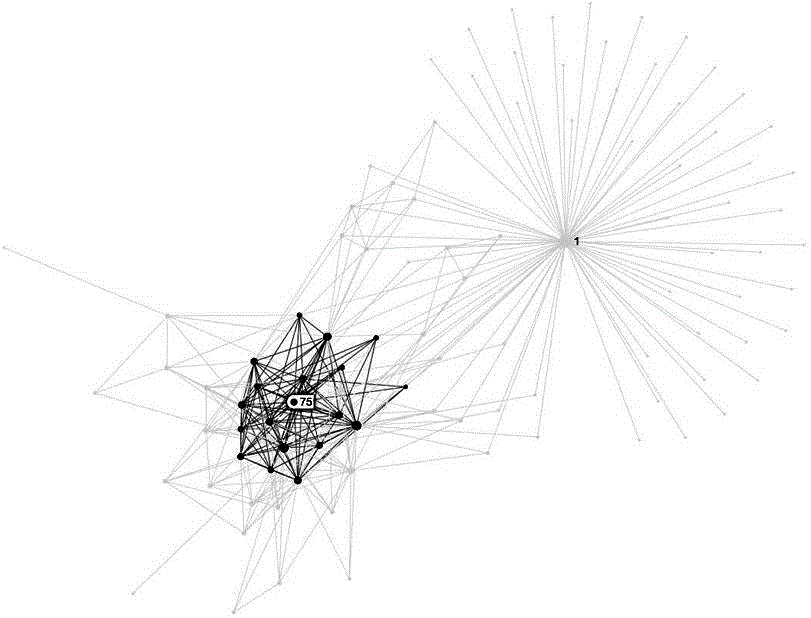
[0027] The data analysis and extraction module is mainly responsible for the extraction of key information. For telephone communication records, it is necessary to analyze the caller, receiver, call duration, total number of calls, call frequency and other data. After calculation and conversion, the output is structured Data, for any two people in the phone communication record, all call records between them will be converted into a piece of structured data, a piece of structured data conta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com