Skip list based cross-site scripting attack defense method
A cross-site scripting attack and table skipping technology, which is applied in special data processing applications, instruments, electrical digital data processing, etc., can solve the problem of consuming a lot of system resources, making it difficult to accurately defend against cross-site scripting, and reducing user experience comfort, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
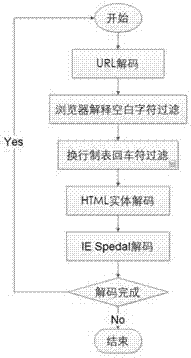
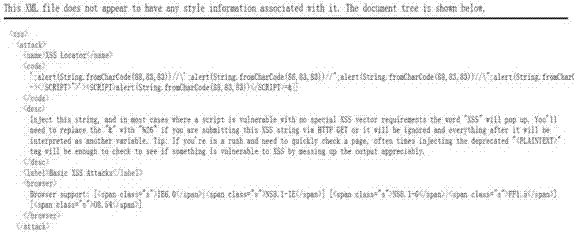
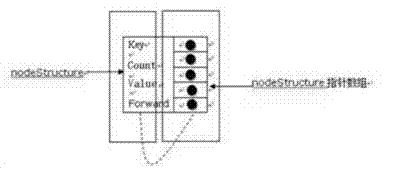
[0033] Cross-site scripting attack (XSS): A cross-site scripting attack refers to a malicious attacker using a vulnerability in an application or code in a web server as a normal visitor to convert a piece of malicious script code (usually a piece of JavaScript code). Some data) are uploaded to the Web server, or a URL link of a Web site that also contains malicious script code is sent to the target user; when an individual user who trusts this Web server visits a page containing malicious script code in this Web site, or opens When the URL link is received, the user's browser will automatically load and execute the script code that the malicious attacker hopes to be executed, thereby achieving the purpose of the attack. From the process of this attack, we can see that cross-site scripting attacks are actually an indirect attack technique. In most cases, malicious attackers use the Web server to indirectly attack another individual user, but in rare cases it is also You can u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com