Block chain-based big data security authentication method and system
A security authentication and big data technology, applied in the field of big data, can solve the problems of paralysis of the whole network authentication system, node data leakage, heavy operation and maintenance workload, etc., to improve the network robustness, simplify the management process, and save the operation and maintenance cost. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] Glossary:
[0042] Hadoop: It is a software framework capable of distributed processing of large amounts of data, the core design is HDFS and MapReduce. HDFS provides storage for massive data, and MapReduce provides calculation for massive data.
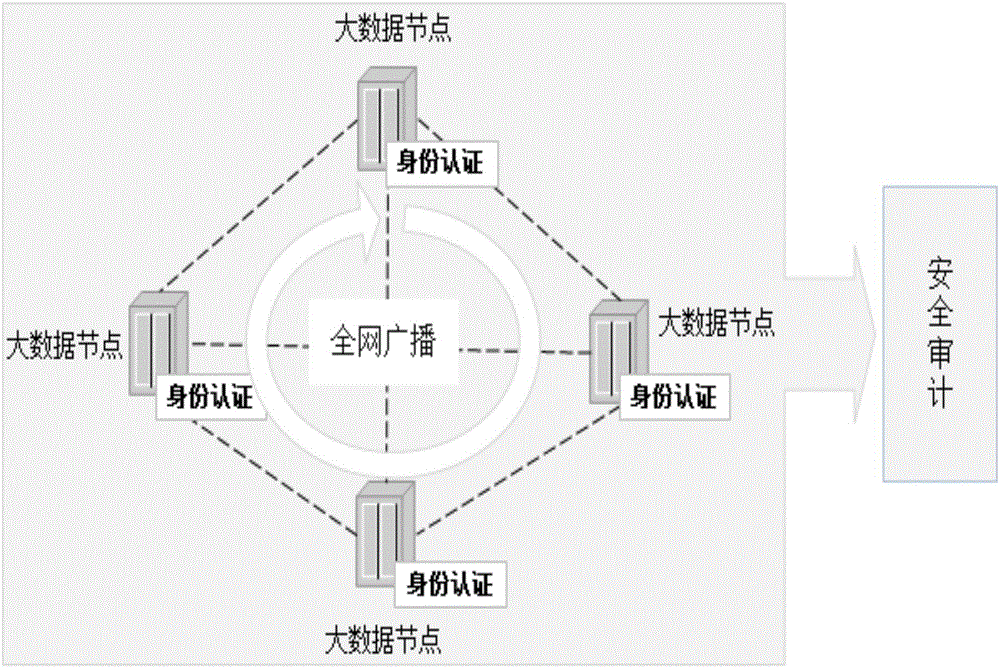
[0043] Decentralization: The influence between nodes will form a non-linear causal relationship through the network. Decentralization refers to an open, flat, and equal system phenomenon or structure.
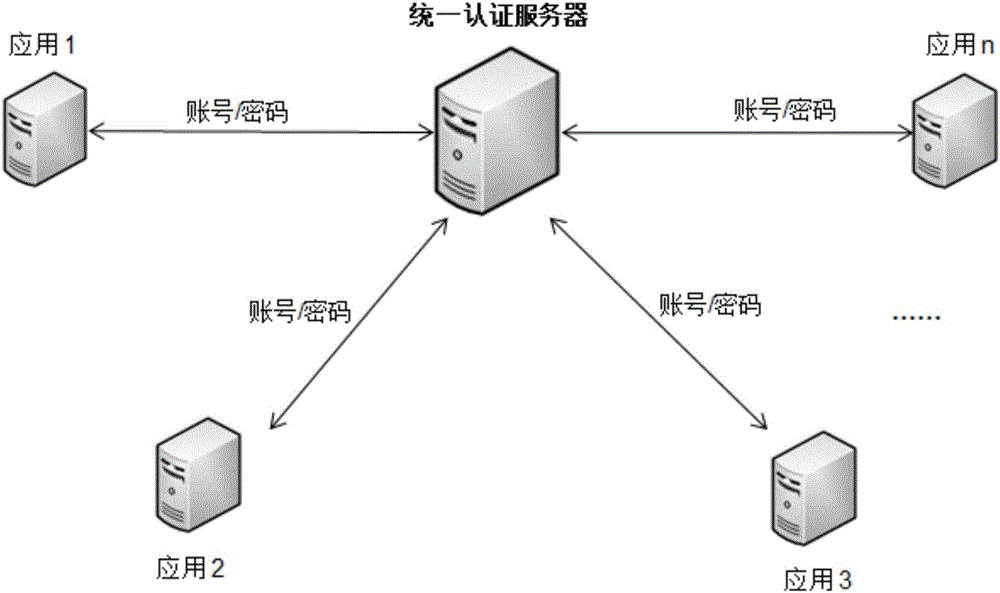
[0044] Blockchain, a technical solution for collectively maintaining a reliable database through decentralization and trustlessness. It is mostly used in user authentication, custody of assets and smart contracts, etc., and value exchange can be completed without third-party access.
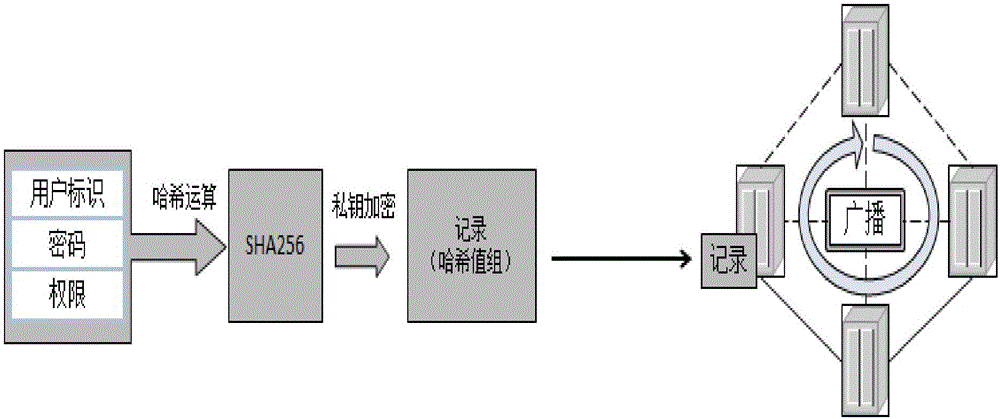
[0045] The process of applying blockchain technology is essentially the process of organizing block content and demonstrating the rationality of consensus agreements.
[0046] A smart contract is a computer program based on the blockchain that...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com