Hardware filling method for Hash algorithm SHA256 message preprocessing
A hash algorithm and filling method technology, applied in the direction of electrical digital data processing, electrical components, energy-saving calculations, etc., can solve the problems of inability to prevent malicious data damage, no resistance to data tampering, etc., and achieve low power consumption and reduced power consumption , to handle the effect of easy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
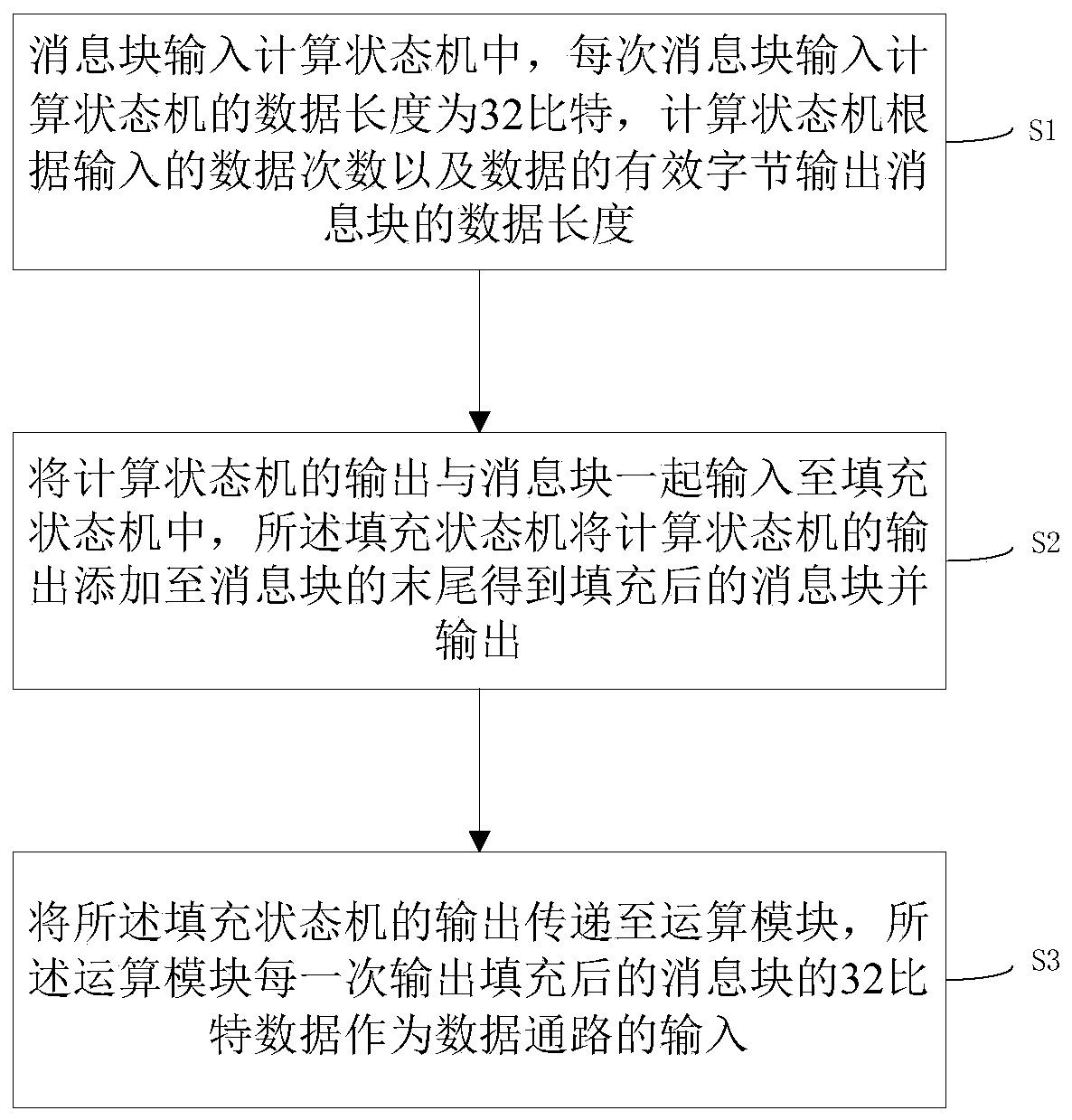
[0035] This embodiment provides a hardware filling method for preprocessing the SHA256 hash algorithm message, such as figure 1 , Including the following steps:
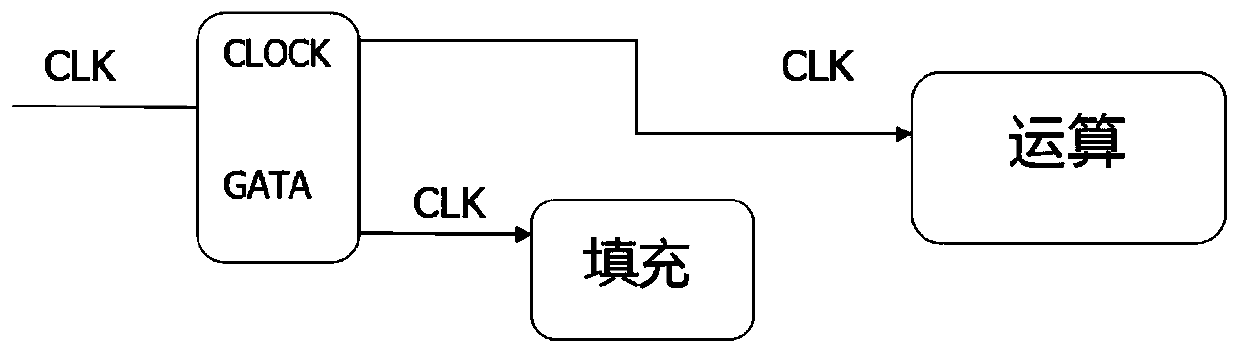
[0036] S1: In the message block input calculation state machine, the data length of each message block input calculation state machine is 32 bits, and the calculation state machine outputs the data length of the message block according to the number of data input and the effective bytes of the data;
[0037] S2: Input the output of the computing state machine together with the message block into the filling state machine, and the filling state machine adds the output of the computing state machine to the end of the message block to obtain the filled message block and output it;
[0038] S3: Pass the output of the filling state machine to the arithmetic module, and the arithmetic module outputs the 32-bit data of the filled message block as the input of the data path each time.
[0039] The output of the counting state machine...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com