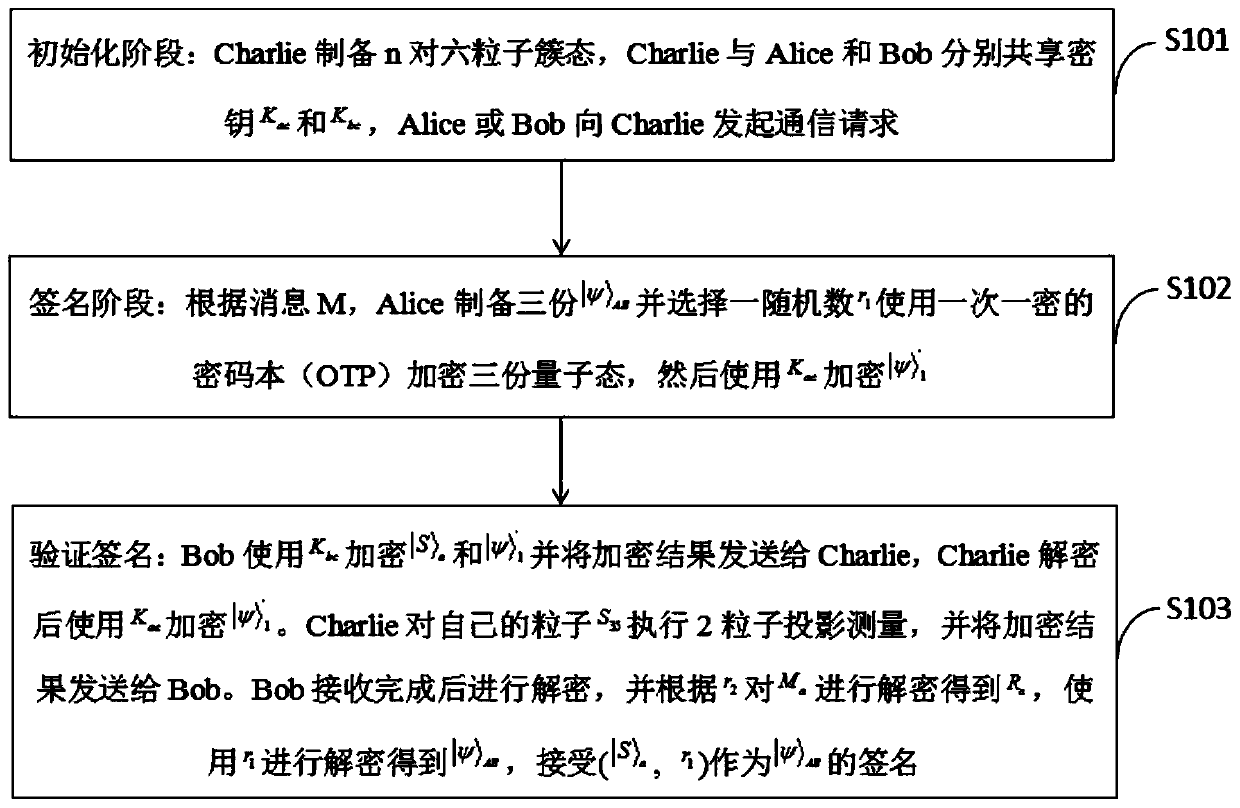
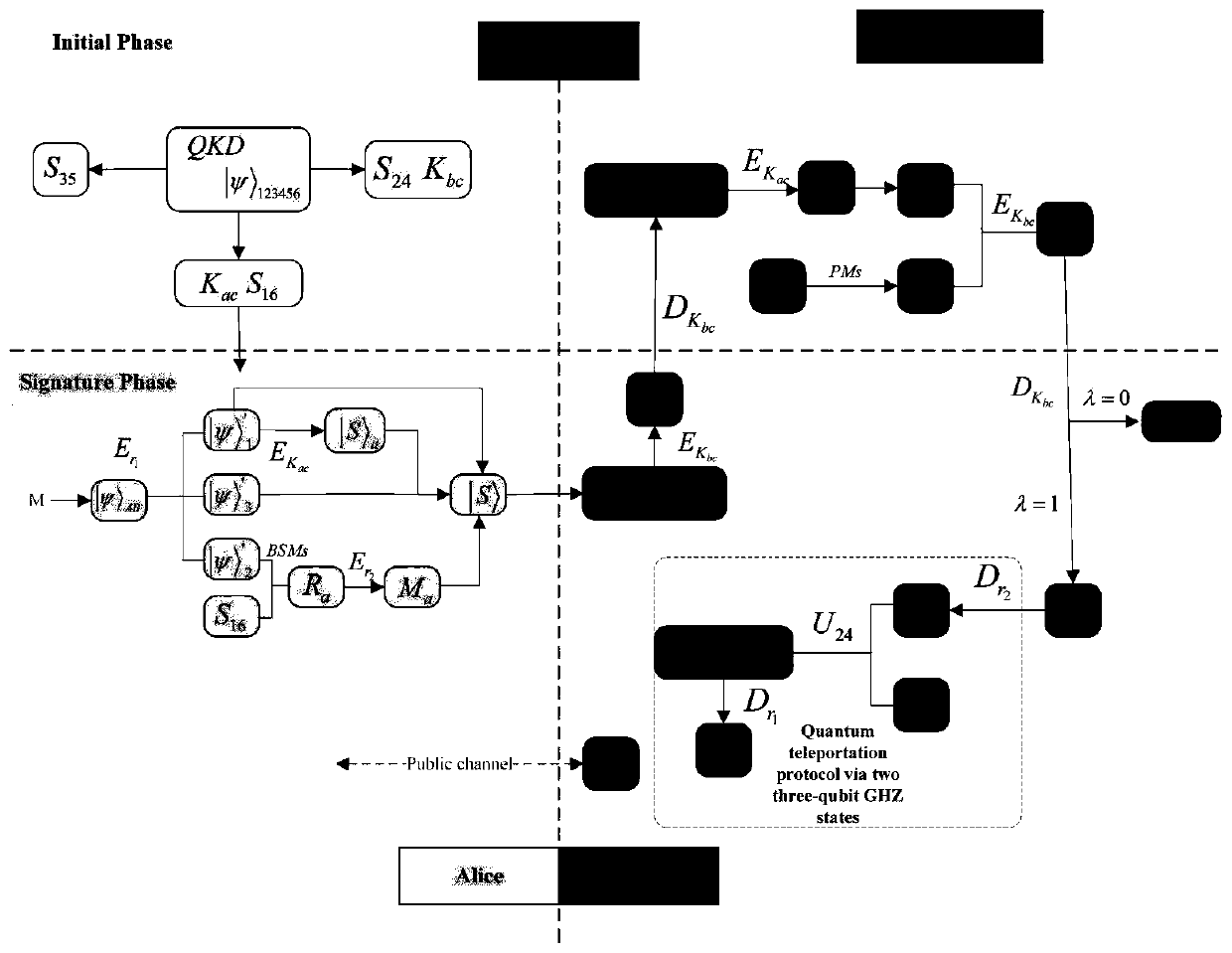
A quantum arbitration signature method and system based on six-particle teleportation
A teleportation and quantum technology, applied in transmission systems, digital transmission systems, user identity/authority verification, etc., can solve problems such as low particle usage efficiency, no consideration of random numbers, and AQS scheme denial of attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0086] 1. Program theory knowledge
[0087] 1.1 The present invention uses two GHZ states as quantum channels to complete the teleportation of quantum information:
[0088] First, a quantum teleportation protocol based on two three-qubit GHZ states and six-qubit entangled states is established. In the present invention, the difference lies in the prior art, the present invention uses 6 qubits as a quantum channel, Alice performs BSMs on its qubit pairs, and Charlie also performs BSMs operations on its qubits. Suppose Alice, Bob, and Charlie share a six-particle cluster state composed of two 3-particle GHZ states. Alice has qubits 1 and 6, Bob has qubits 2 and 4, and Charlie has qubits 3 and 5 respectively. The six qubit cluster states are described as follows: Alice keeps the two-particle state as: |ψ> AB =(α|00>+β|10>+γ|01>+η|11>) AB . The system state at this time is:
[0089]
[0090] Alice performs Belki measurements on her (A,1) and (B,6) particle pairs, and sh...
Embodiment 2
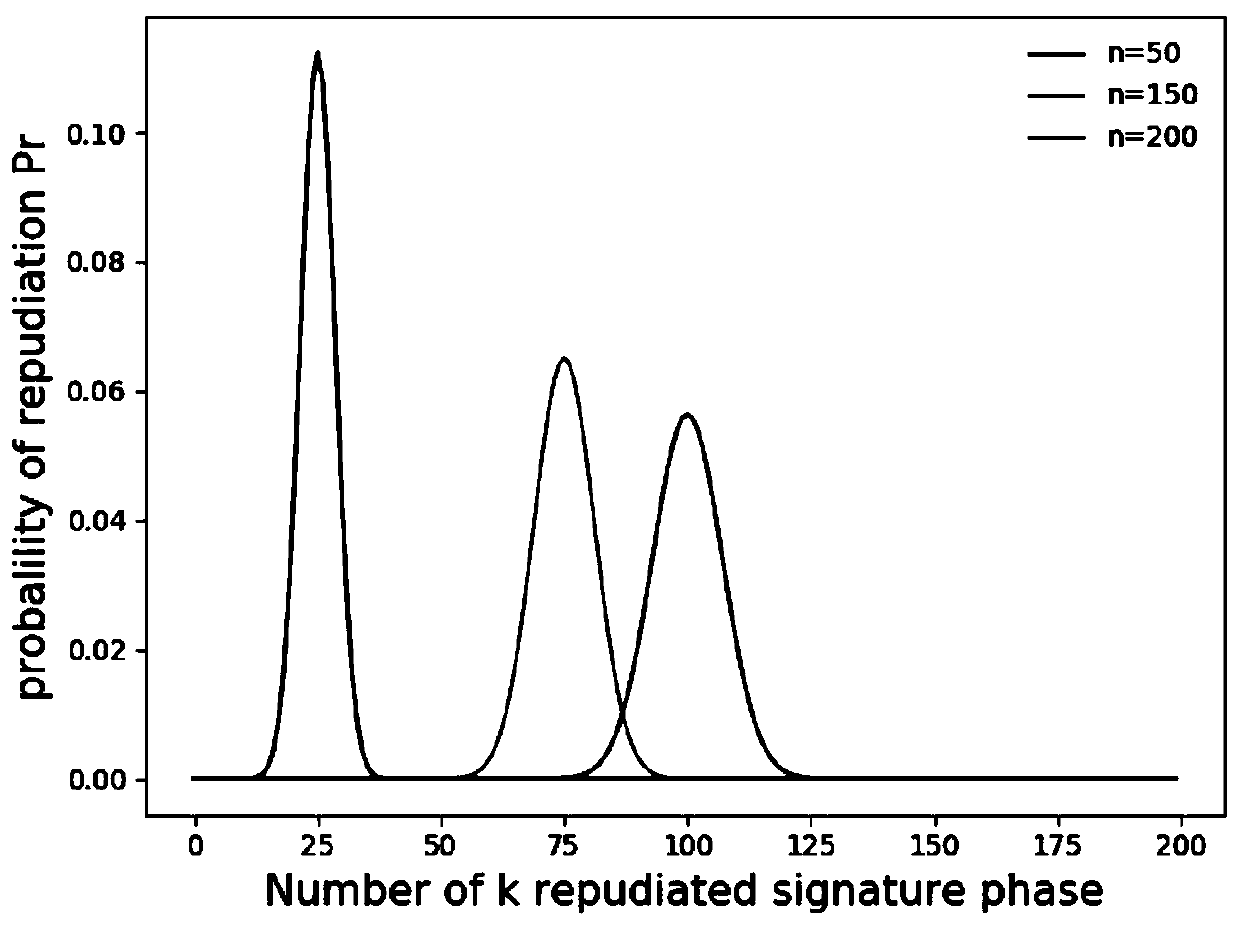
[0132] Example 2: Protocol Analysis
[0133] 1), the non-repudiation of the signer:
[0134] Assuming that the signer Alice denies her signature, the arbitrator Charlie must be able to discover her dishonesty: Alice’s signature state|S> a contains her key in Only Alice and Charlie can use K ac Perform other operations such as encryption and decryption. Therefore Alice cannot deny her signature.
[0135] 2), the non-repudiation of the confirmer:
[0136] If Bob receives the signature sent by Alice, he cannot deny his acceptance if the agreement is completed normally. In the confirmation phase, Bob needs to use the key K bc For messages (|S> a ,|ψ>′ 1 ) for encryption operations: Bob then sends it to Charlie, who uses the key K bc Decrypt it and restore it. Therefore, the arbitrator Charlie must be able to judge the state of the message |ψ> B Does the key K exist in bc . When Bob receives the message sent back by Charlie, if he wants to get the random number r 2...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com