Access control system, method and device and intelligent loudspeaker box
An access control, smart speaker technology, applied in instruments, single input/output register, time register, etc., can solve problems such as inability to unlock access control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
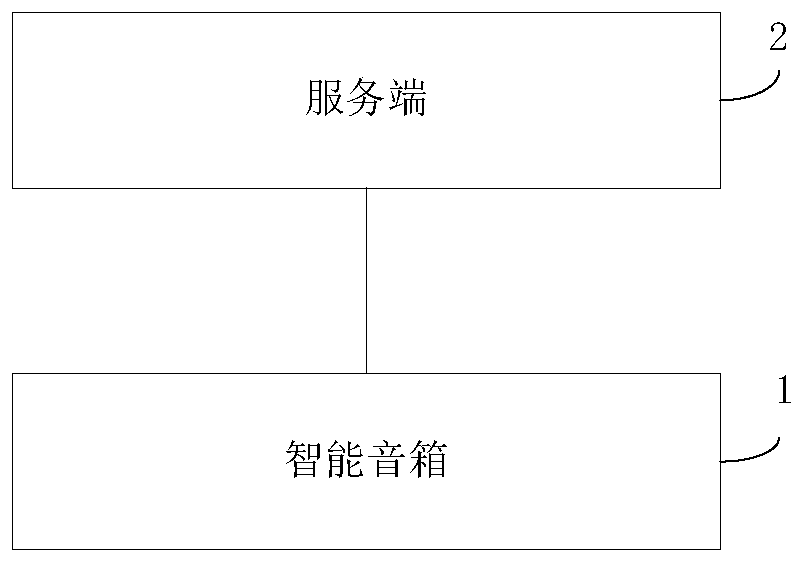
[0200] Please refer to figure 1 , which is a structural diagram of the access control system of the present application. The system includes: a smart speaker 1 and a server 2. In addition, an access control device 3 may also be included.
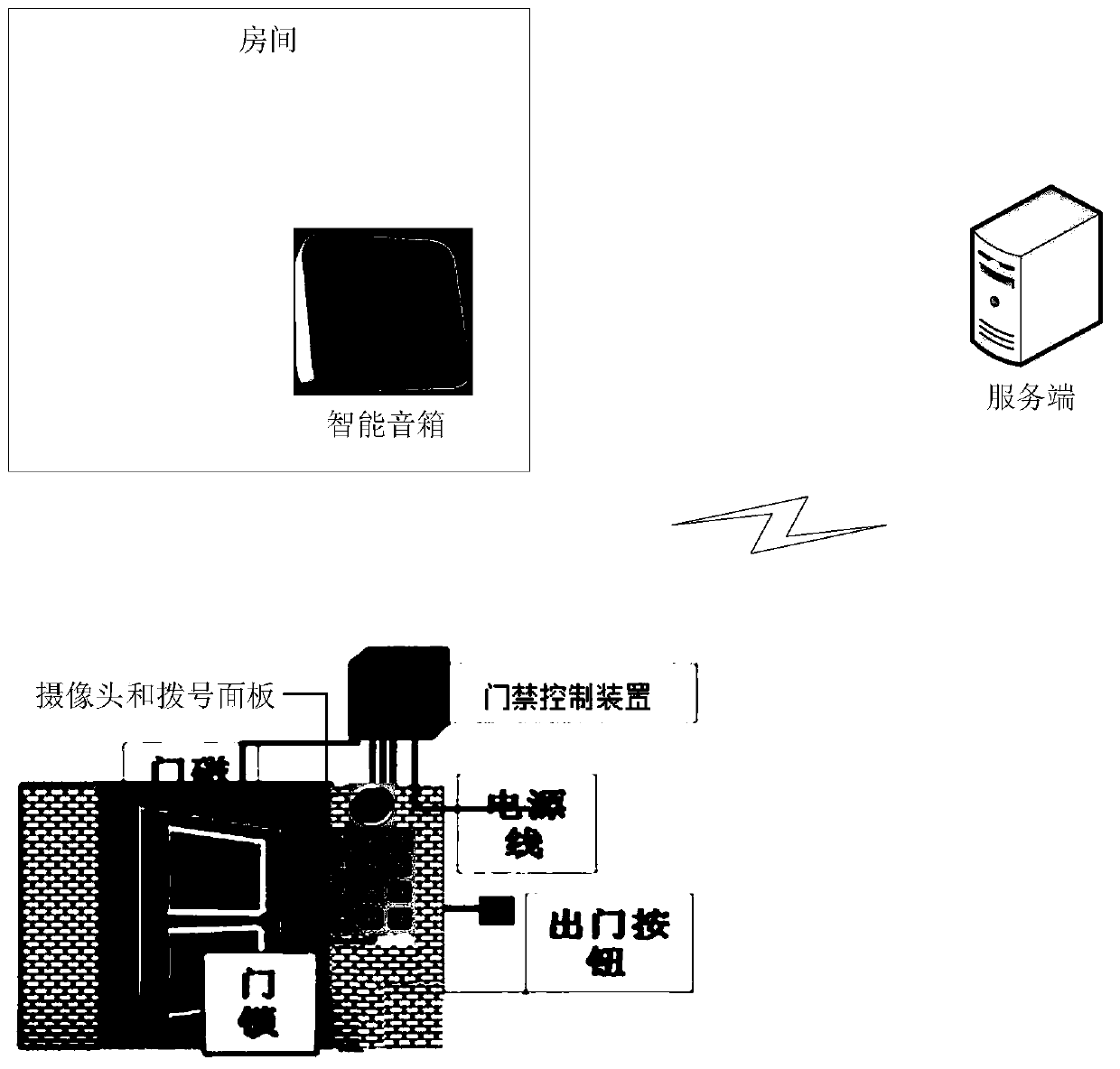
[0201] Smart speaker 1 can be a tool for home consumers to use voice to surf the Internet, such as ordering songs, shopping online, or understanding the weather forecast. It can also control smart home devices, such as opening curtains, setting the refrigerator The water heater heats up, etc.
[0202]The smart speaker 1 can be deployed in the room of the interviewed user, and can also be carried by the interviewed user when the interviewed user goes out. The smart speaker 1 may be a smart speaker with a display screen, or a smart speaker without a display screen.
[0203] The server 2 can be a server deployed on a cloud server, or a server dedicated to implementing an access control system, and can be deployed in a data center.
[0204]...
no. 2 example
[0243] Corresponding to the above-mentioned access control system, the present application also provides an access control method, where the method is executed by an access control device.
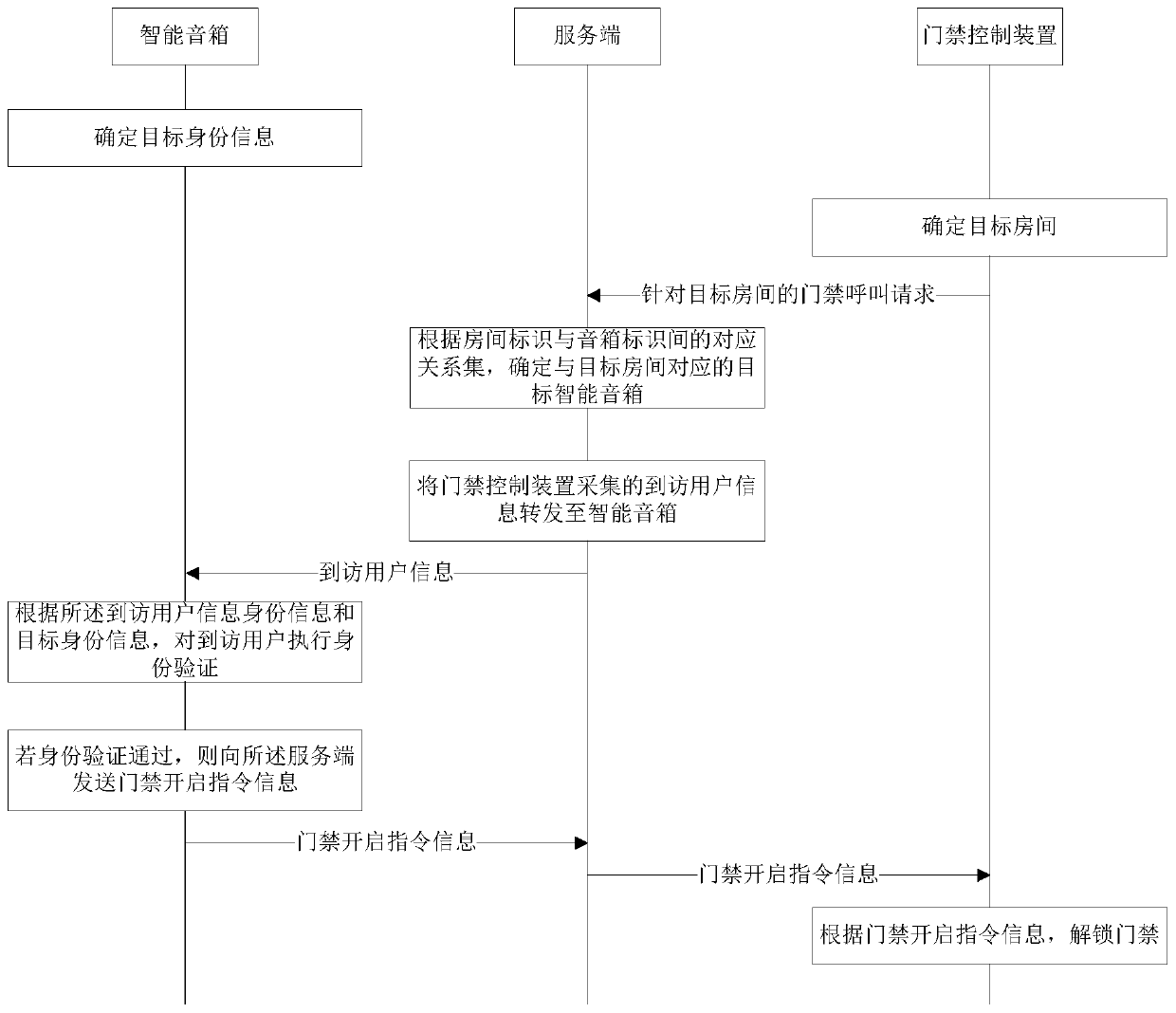
[0244] Please refer to Figure 5 , which is a flow chart of an embodiment of an access control method provided by the present application. The parts in this embodiment that are the same as those in the first embodiment will not be described again. Please refer to the corresponding parts in Embodiment 1. An access control method provided by the application includes:
[0245] Step S501: Send an access control call request for the target room to the server;
[0246] Step S502: Send the visitor information to the server, so that the server can send the visitor information to the smart speaker, and the smart speaker authenticates the visitor according to the visitor information.
[0247] In an example, the access control device receives user identity information collection instruction informa...
no. 3 example
[0256] Please see Figure 6 , which is a schematic diagram of an embodiment of the access control device of the present application. Since the device embodiment is basically similar to the method embodiment, the description is relatively simple, and for relevant parts, refer to the part of the description of the method embodiment. The device embodiments described below are illustrative only.
[0257] The present application additionally provides an access control device, including: an input panel 601, a memory 602, a processor 603, and a communication module 604; the memory is used to store a program for implementing the access control method, and the device is powered on and runs through the processor. After the program of the method, perform the following steps: send the access control call request for the target room to the server; send the visiting user information to the server, so that the server can send the visiting user information to the smart speaker, The identity...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com