Physical layer secure transmission method capable of resisting any number of eavesdropping antennas
A physical layer security and transmission method technology, applied in the field of physical layer security transmission, can solve problems such as eavesdropping and attack, deterioration, and inability to resist, and achieve the effect of low complexity, low power consumption, and low interference
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] In order to have a clearer understanding of the technical features, objectives and effects of the present invention, specific embodiments of the present invention will now be described with reference to the accompanying drawings.
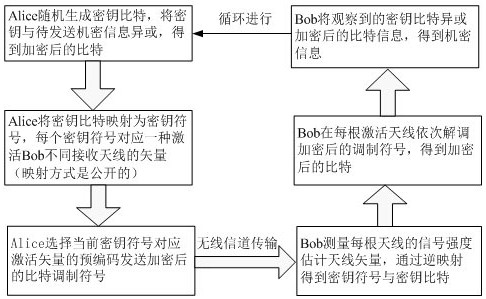
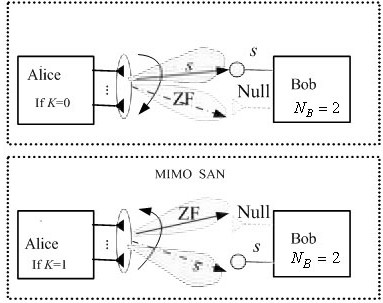
[0041] In order to have a deeper understanding of the present invention, the physical aspects realized by the method are now described, and those skilled in the art should understand that it does not limit the scope of protection of the present invention.
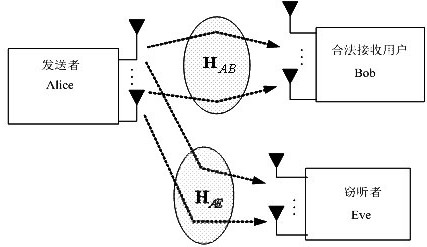
[0042] The legal communication parties Alice and Bob each use a protected area to surround themselves with a radius of R. The radius of the protected area R must be greater than the irrelevant distance of the channel, so that the eavesdropper Eve cannot enter the protected area for eavesdropping, which means that Eve and The distance between Alice and Bob is greater than R, which ensures that Eve's channel is independent of Alice and Bob. The length of R is determined by the channel propagation...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com