Multi-gateway authentication method and system, storage medium, computer equipment and terminal
An authentication method and multi-gateway technology, applied in the fields of systems, multi-gateway authentication methods, terminals, storage media, and computer equipment, can solve problems such as high cost of receiving and sending messages, leakage of communication content, security threats to entities to be authenticated, etc. , to achieve good forward security, protect user privacy, good user privacy and forward security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
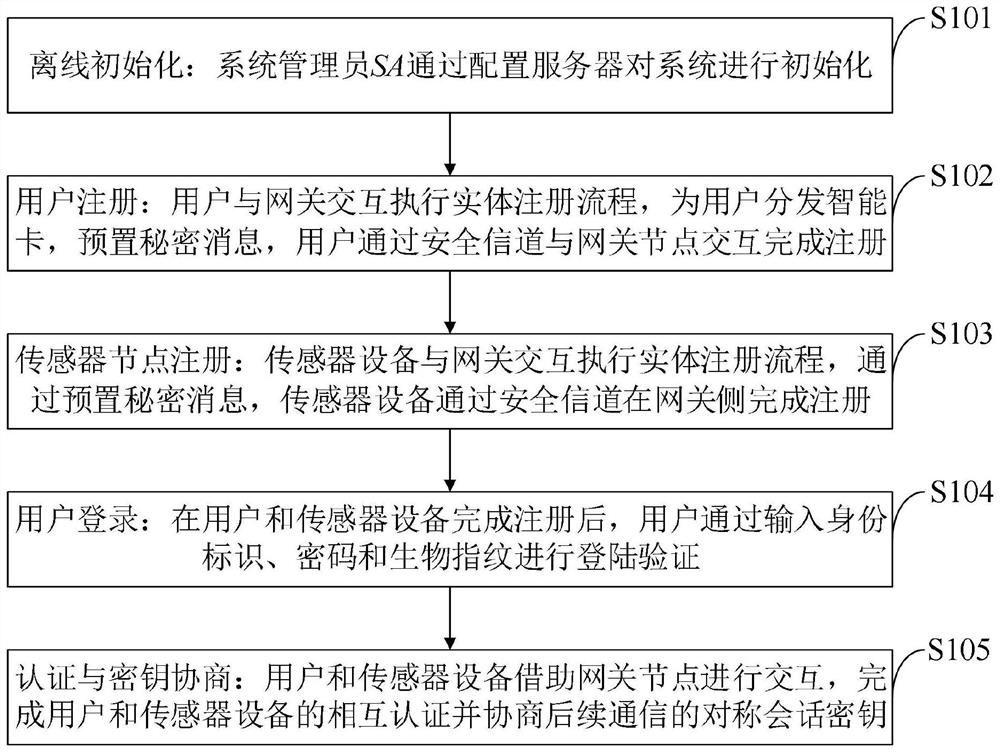
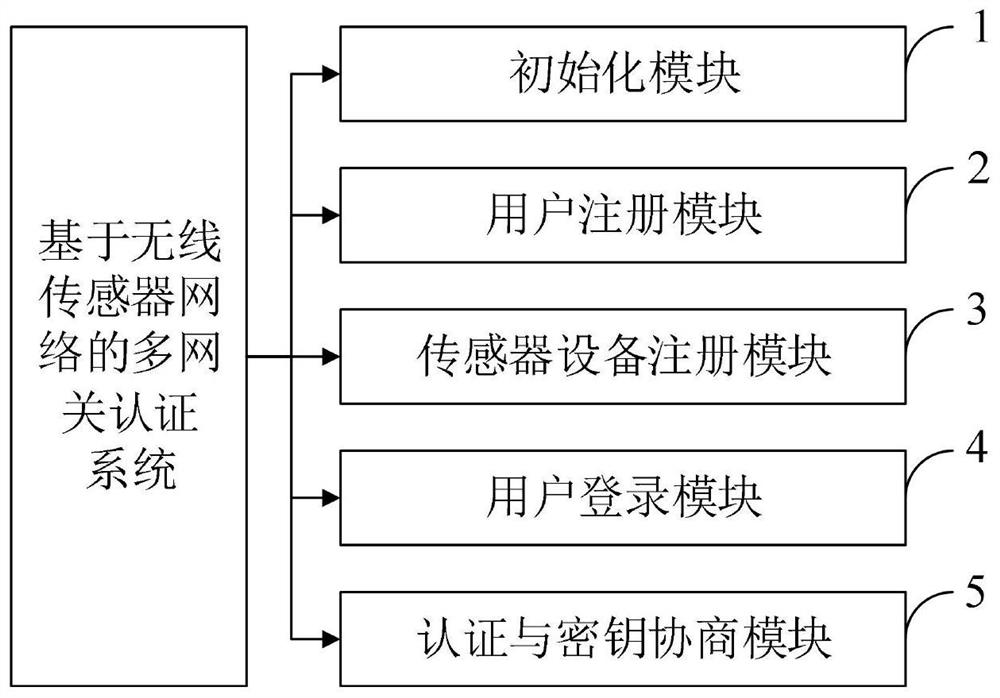
[0080] In order to make the object, technical solution and advantages of the present invention more clear, the present invention will be further described in detail below in conjunction with the examples. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
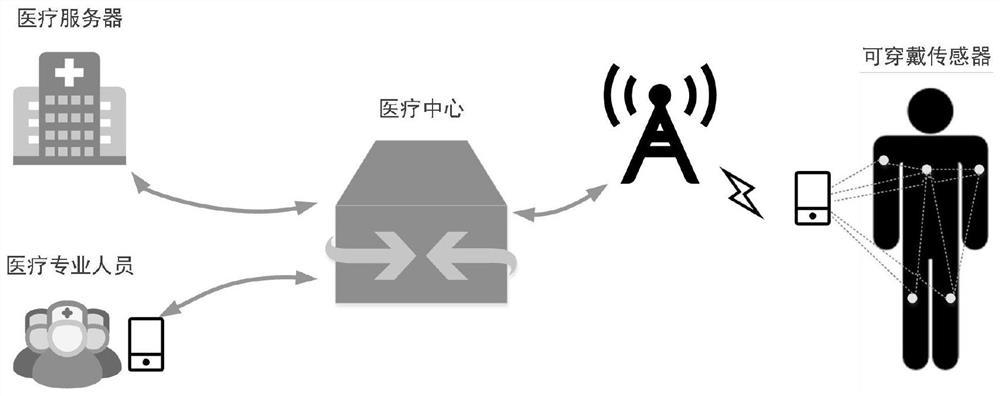
[0081] Aiming at the problems existing in the prior art, the present invention provides a multi-gateway authentication method, system, device and application. Specifically, in smart medical scenarios, in some scenarios that require emergency rescue, in order not to delay the final Doctors need to collect data in real time through the medical sensors deployed on the patient's body in order to obtain the patient's health status in a timely manner and formulate an appropriate treatment plan. At the same time, there are cross-domain access requirements in some special cases, such as a medical professional in a certain domain Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com