Security authentication method and system based on open interface communication
A security authentication, open interface technology, applied in the computer field, can solve the problems of high memory cost, interface replay attack, key leakage and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
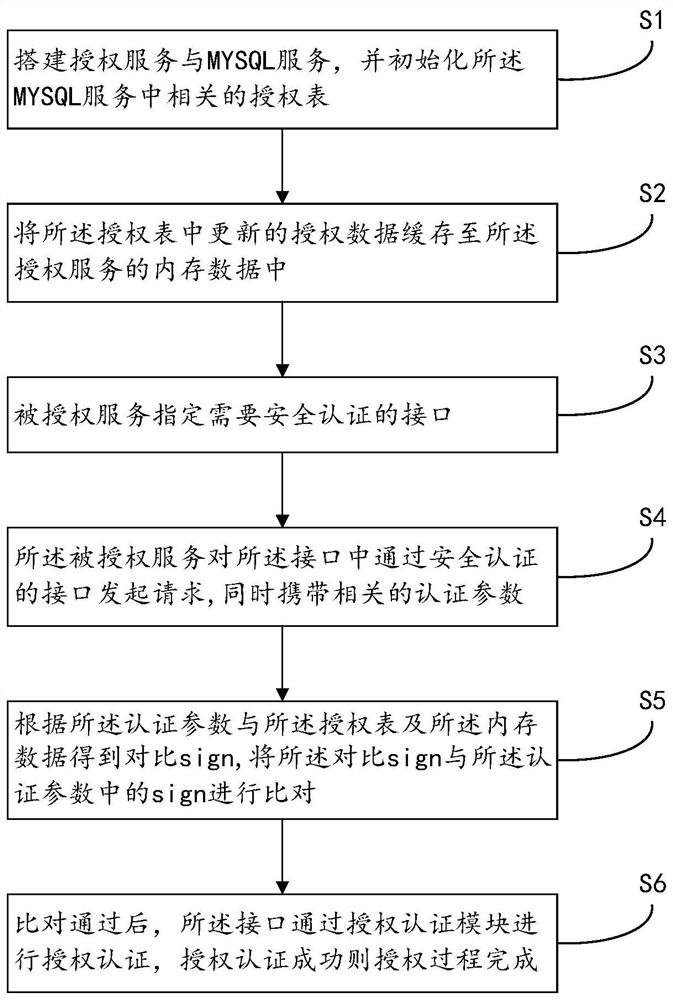
[0052] figure 1 It is a schematic diagram of steps of a security authentication method based on open interface communication provided by the present invention. Such as figure 1 As shown, this embodiment discloses a specific implementation of a security authentication method based on open interface communication (hereinafter referred to as "method").
[0053] Specifically, the method disclosed in this embodiment mainly includes the following steps:
[0054] Step S1: Build the authorization service and MYSQL service, and initialize the related authorization table in the MYSQL service;
[0055] Specifically, build the MYSQL service and initialize the relevant authorization table (OpenAuth) in the MYSQL service. The information specified in the authorization table field includes but is not limited to: App source name, AppId, AppSecret, status validity, and creation date.
[0056] Step S2: cache the updated authorization data in the authorization table into the memory data of th...
Embodiment 2
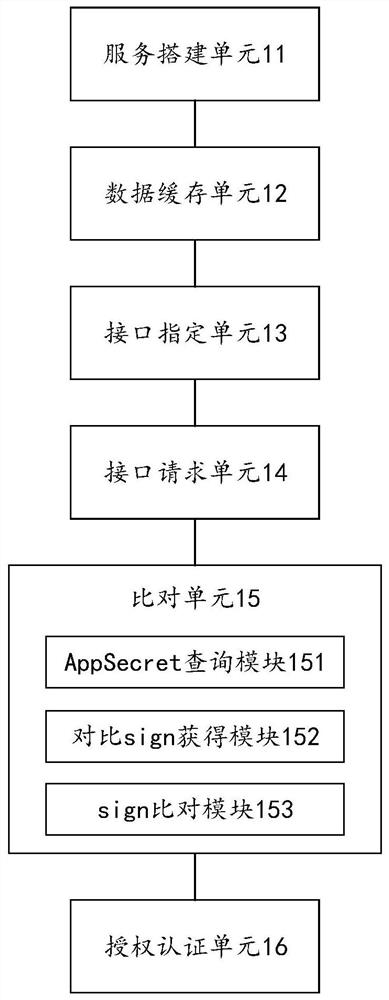
[0080] In combination with the security authentication method based on open interface communication disclosed in Embodiment 1, this embodiment discloses a specific implementation example of a security authentication system based on open interface communication (hereinafter referred to as "system").
[0081] refer to image 3 As shown, the system includes:
[0082] Service building unit 11: build authorization service and MYSQL service, and initialize related authorization tables in MYSQL service;
[0083] Data cache unit 12: cache the updated authorization data in the authorization table into the memory data of the authorization service;
[0084] Interface specifying unit 13: the authorized service specifies an interface requiring security authentication;
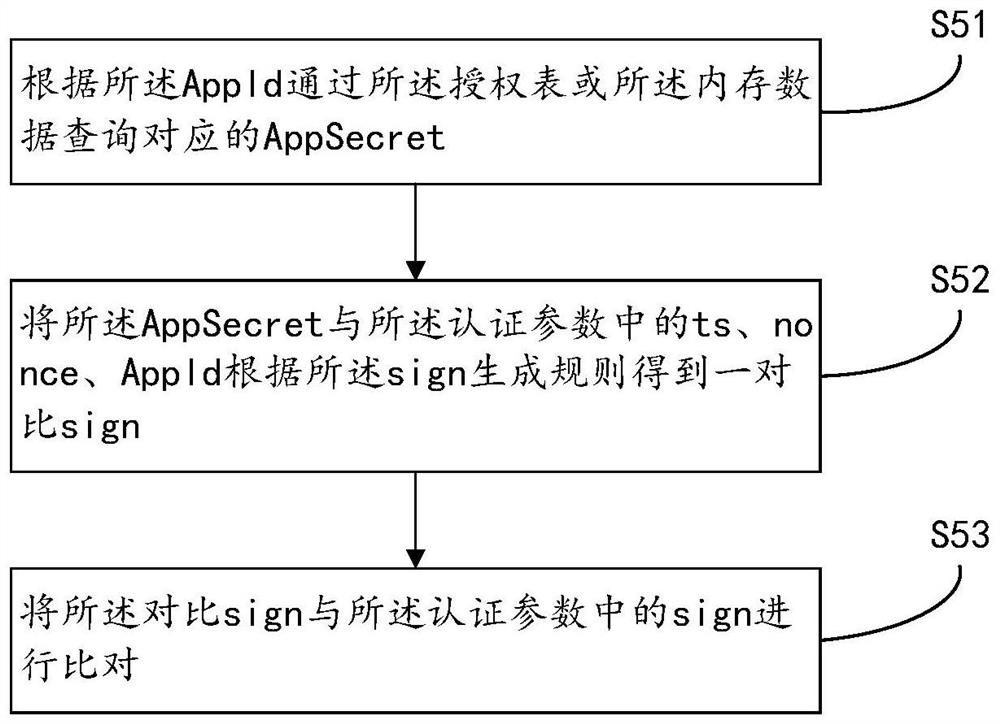
[0085] Interface request unit 14: the authorized service initiates a request to the interface that has passed security authentication among the interfaces, and carries relevant authentication parameters at the same time; ...
Embodiment 3
[0094] combine Figure 4 As shown, this embodiment discloses a specific implementation manner of a computer device. The computer device may comprise a processor 81 and a memory 82 storing computer program instructions.
[0095] Specifically, the processor 81 may include a central processing unit (CPU), or an Application Specific Integrated Circuit (ASIC for short), or may be configured to implement one or more integrated circuits in the embodiments of the present application.
[0096] Among them, the memory 82 may include mass storage for data or instructions. For example without limitation, the memory 82 may include a hard disk drive (Hard Disk Drive, referred to as HDD), a floppy disk drive, a solid state drive (SolidState Drive, referred to as SSD), flash memory, optical disk, magneto-optical disk, magnetic tape or universal serial bus (Universal Serial Bus, referred to as USB) drive or a combination of two or more of the above. Storage 82 may comprise removable or non-r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com