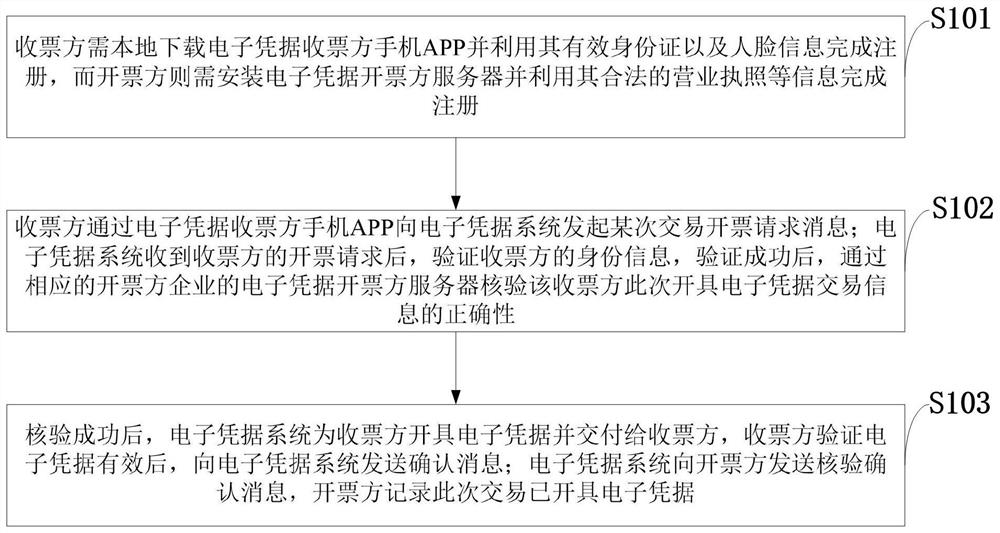
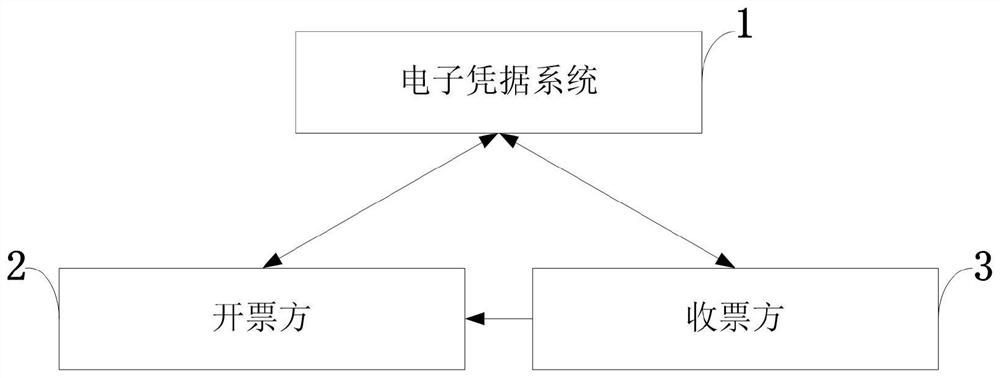
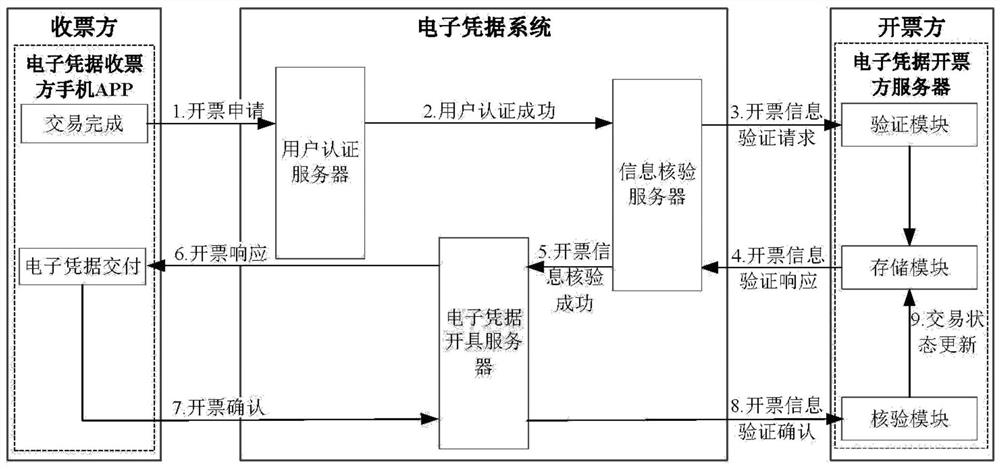
Privacy protection online invoicing service authentication method and system, storage medium and application
An authentication method and privacy protection technology, applied in the field of privacy protection online billing service authentication, can solve problems such as unlinkability, high computing and communication overhead, unlinkability, data confidentiality, etc., and achieve the effect of mutual authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0087] The embodiment of the present invention describes the system setup phase process. Electronic Credential System Selection Master Key K e , select a cyclic group G on the elliptic curve E, where the order of G is q, the generator is P, and the private key sk∈Z is selected q * , the public key pk=sk*P. Subsequently, the electronic credential system selects two secure hash functions h 1 ,h 2 , a keyed hash function f 1and a key derivation function KDF. Then, the electronic credential system selects a bind function according to the binding relationship between the ID card information and the face information required by the identity verification system of the Ministry of Public Security. The bind function is generally a hash function and does not leak input information. Finally, the electronic credential system selects the symmetric encryption algorithm ENC and decryption algorithm DEC, as well as the fuzzy extraction generation algorithm Gen and regeneration algorith...
Embodiment 2
[0089] The embodiment of the present invention describes the process of the online registration stage of the bill collector.
[0090] (1) The mobile APP of the electronic credential billing party first needs to locally verify the consistency of the ID card photo provided by the billing party user and the live face collection photo. If they are consistent, the mobile APP of the electronic voucher recipient will use the face information B provided by the user. i Calculate (α i ,β i )=Gen(B i ), and then export the ID card information eID i with face information α i The binding relationship A i =bind(eID i ,α i ). Then, the mobile APP of the electronic voucher recipient calculates H i =h 1 (eID i ,α i ,h i ), choose a random number Calculate R i =r i *P, Z i =r i *pk and MLK i =h 2 (Z i ,t i0 )=MK i ||LK i , using the encryption key MK i encrypted c i =ENC MKi (eID i ||A i ||H i ), using the integrity key LK i Calculate s i =f 1 (LK i ,C i ||R ...
Embodiment 3
[0094] The embodiment of the present invention describes the process of the online registration stage of the invoicing party.
[0095] (1) The corporate legal person will use the identification information sID of the company that issues the invoice j As well as business license, legal person ID card and other information M j Enter the electronic credential billing party server. The electronic credential issuer server selects a random number Calculate R j =r j *P, Z j =r j *pk, and MLK j =h 2 (Z j ,t j0 )=MK j ||LK j . Subsequently, the electronic credential issuer server adopts the encryption key MK j Put private information M j encrypted to get c j =ENC MKj (sID j ||M j ), using the integrity key LK j Calculate s j =f 1 (LK j ,C j ||t j0 ), where t j0 is the current timestamp. Finally, the electronic credential issuer server will register the request message (c j ,s j ,R i ,t j0 ) to the electronic credential system.
[0096] (2) After the elec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com