Safety control system and method for terminal equipment
A technology of terminal equipment and control system, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve problems such as malicious manipulation of terminal equipment and damage to the normal operation of IoT terminal equipment, so as to avoid losses, ensure safe operation, Effect of preventing hacker's attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0025] This embodiment proposes a security control system for terminal equipment. The system includes a background management terminal, a main control single-chip microcomputer, a security chip, and a peripheral execution mechanism; The safety chip communicates with the peripheral actuators.
[0026] The background management terminal is used to send the configuration parameters and control commands of the terminal actuator to the security chip through the main control microcontroller in the form of cipher text;
[0027] The security chip is used to decrypt and verify the received ciphertext, and output a control signal to the actuator according to the decryption result to control the actuator to perform corresponding actions.
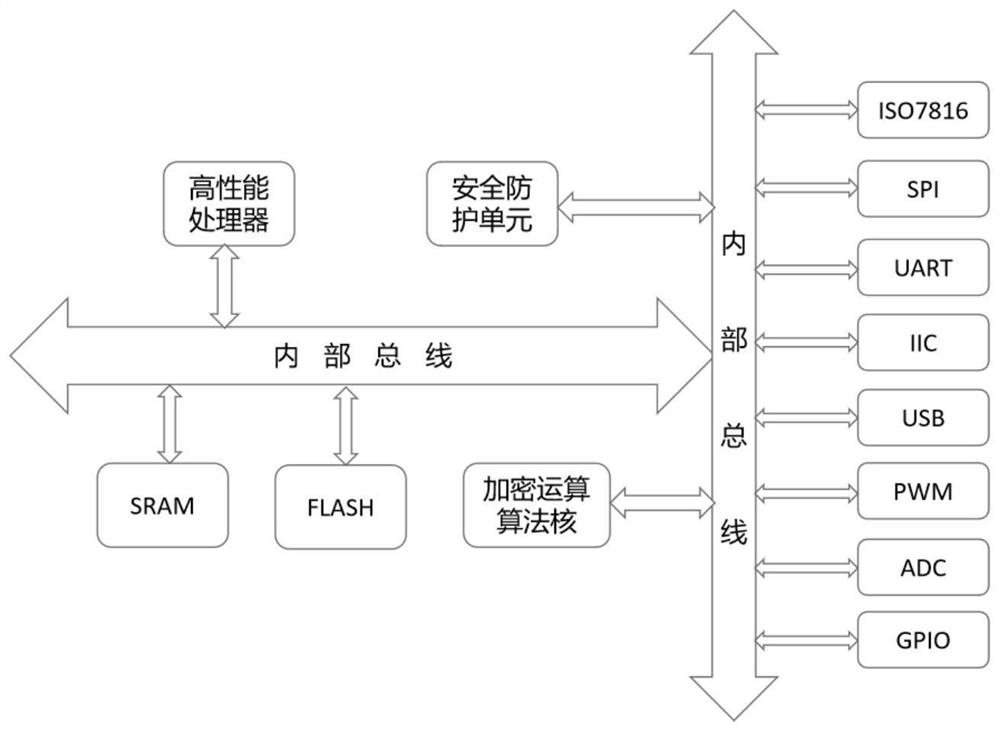
[0028] In this embodiment, the security chip has the characteristics of anti-cracking and anti-attack, and the professional security operating system it is equipped with uses the GPIO port of the security chip to control the peripheral actuator of the ...
example 1
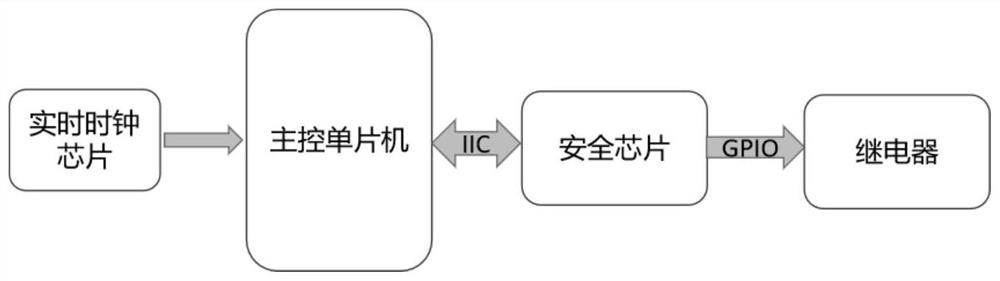
[0031] Control example 1, with a street light controller (such as figure 2 shown) as an example to illustrate the specific implementation process: the main control single-chip microcomputer and the security chip communicate through the IIC interface, and the security chip controls the switch of the relay through the GPIO port. The street light controller is based on the time rules for turning on and off the street lights set by the centralized management background of the system. When the real-time clock is 18:00, the main control single-chip microcomputer sends the command to turn on the street lights to the security chip. After the security chip receives the command, it parses the command and verifies that it is correct. Then, set the GPIO port to output the street light turn-on control signal and turn on the street light; when the real-time clock is 5 o'clock, the master microcontroller sends the command to turn off the street light to the security chip. After the security ...
example 2
[0032] Control example 2, with motor controller (such as image 3 shown) as an example to illustrate the specific implementation process: the communication chip and the system centrally manage the background networking communication to realize the communication between the background and the main control microcontroller; the main control microcontroller and the security chip communicate through the UART interface; the security chip controls the motor through the PWM interface Rotating speed. The centralized management backend of the system issues the ciphertext command of speed control to the motor controller through the Internet of Things according to the actual working conditions. After the motor controller receives the command, it forwards it to the security chip. The security chip decrypts the control command, and after judging that the command is complete, set the Output PWM control signal to control the speed of the motor.
[0033] In this embodiment, the GPIO port of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com