Dynamic password identity authentication system applicable to network based on software token
A software token and dynamic password technology, applied in the AAA field, can solve problems such as interception, counterfeiting, malicious borrowing, large amount of data, etc., and achieve improved security performance, strong practicability, and easy distribution Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The present invention will be described in further detail below in conjunction with the accompanying drawings and the inventor's specific implementation methods.
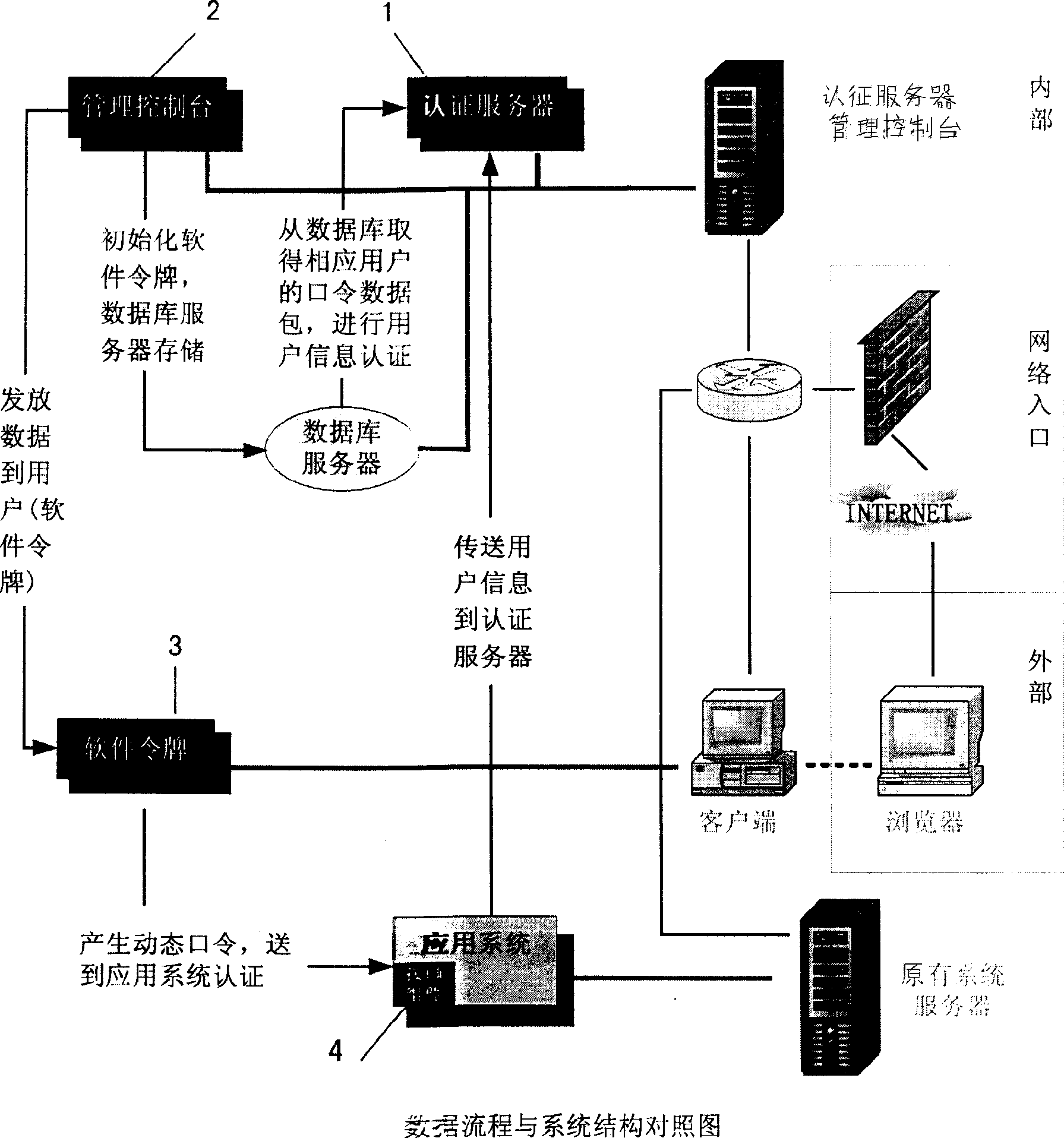
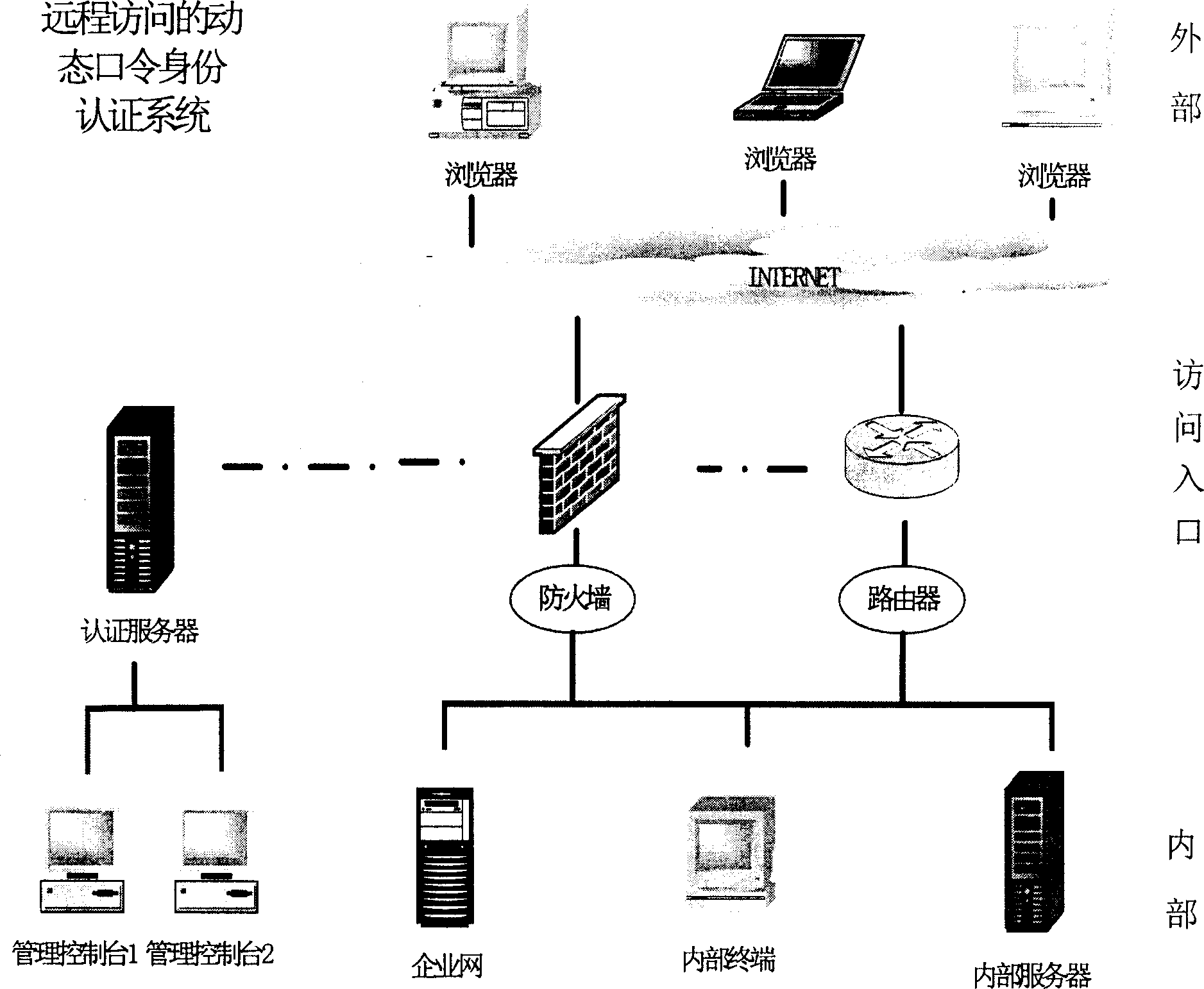
[0041] According to the technical scheme of the present invention, based on the dynamic password identity authentication system applicable to the network based on the software token, the system as a whole adopts a B / S modular structure, and the software token is iconized (see details). figure 1 ),include:
[0042] An authentication server 1;
[0043] a management console 2;
[0044] A software token 3, downloaded from the WEB site to the client's terminal equipment via the intranet or the Internet, and installed and run;
[0045] an interface component 4;
[0046] The authentication server 1 software follows the standard RADIUS protocol for international identity authentication services, and authenticates the dynamic password generated by the software token 3, so that the original application system adds mul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com