Method for checking and killing new computer virus using independent operation system
An operating system and virus technology, applied in the field of network communication technology, can solve problems such as the inability to upgrade the virus signature database, endanger the normal use of the user's computer, and hinder the normal connection of the network, etc., to achieve the effect of simplifying the process and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
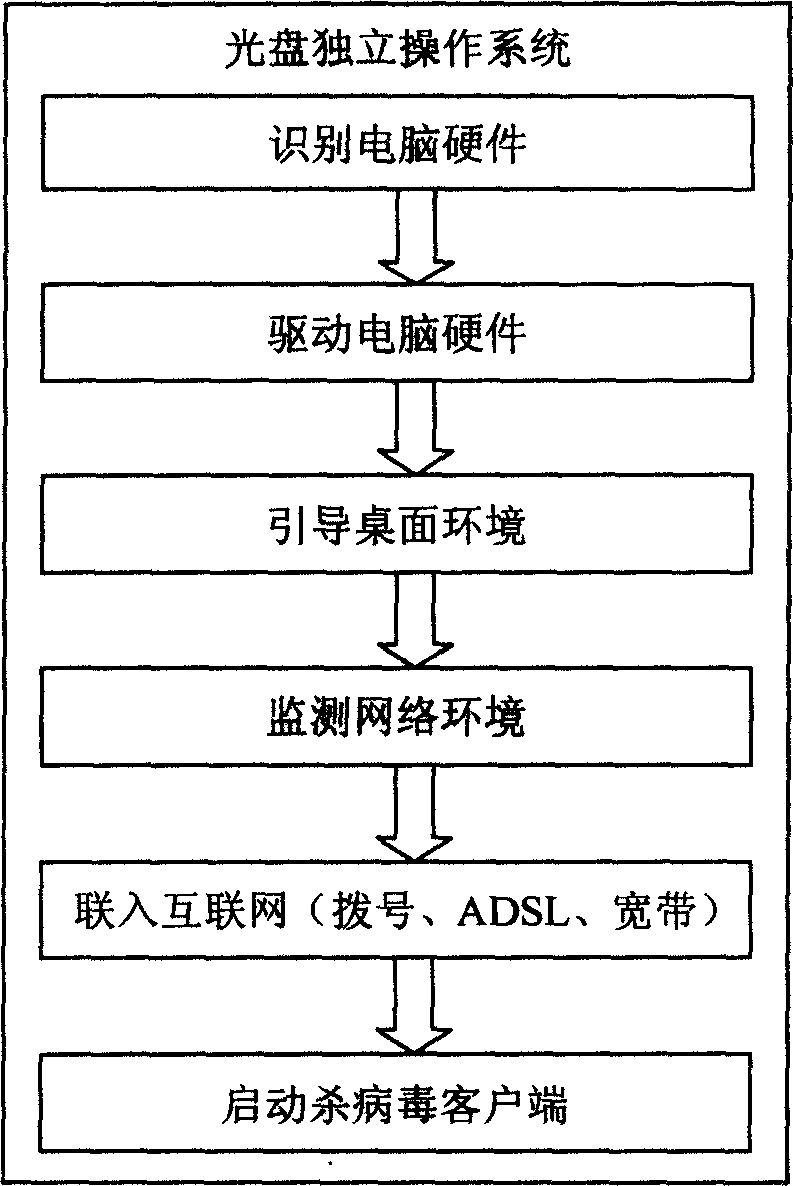
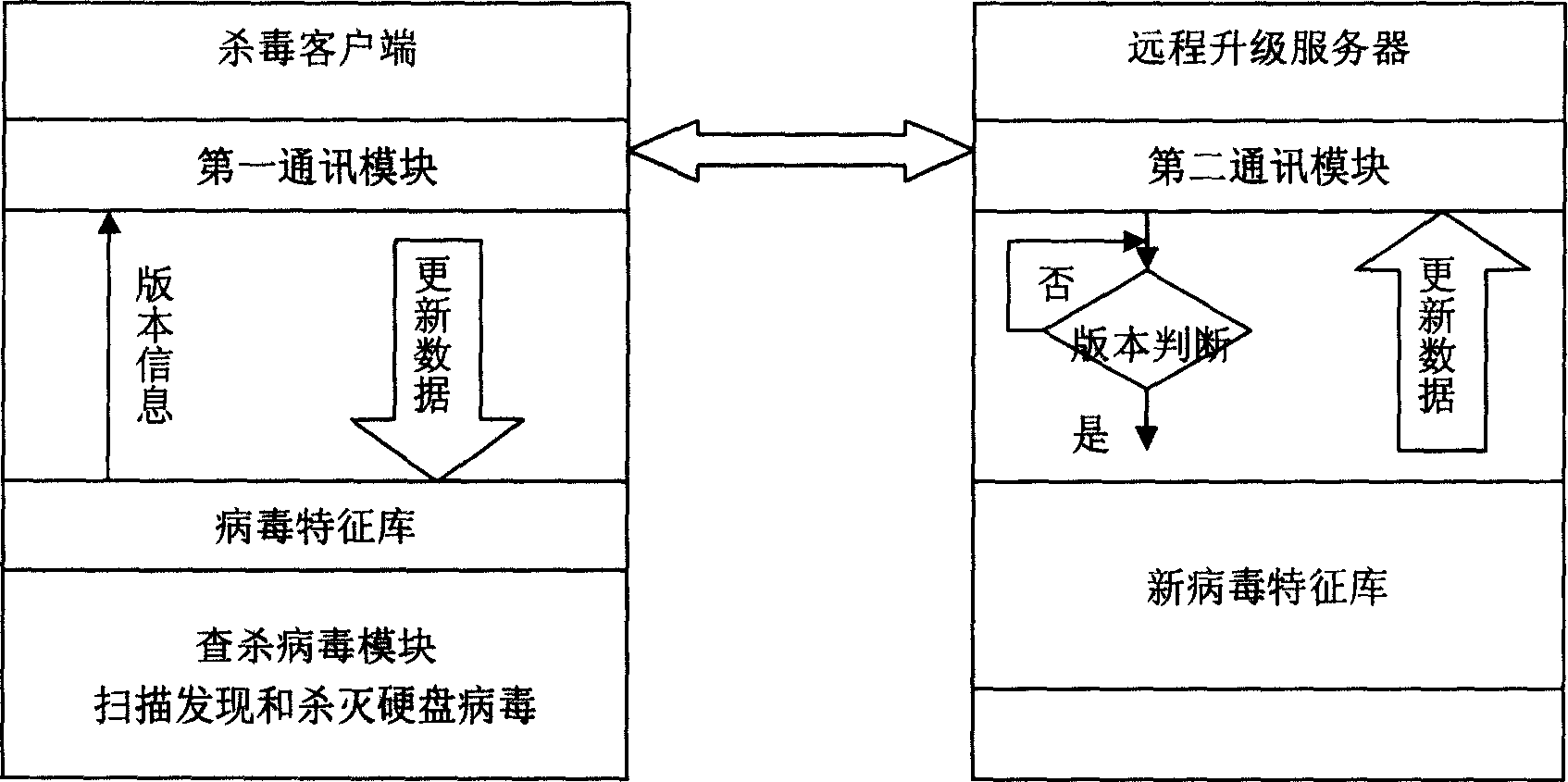
[0010] In the present, a new worm virus bypasses the traditional virus firewall (because the update of traditional antivirus software and the virus signature database always lags behind the development of the virus) and infects the user's computer with the attachment of the email, and is activated in the memory , frequently sending out a large amount of data, causing the user's computer system resources to be exhausted, and blocking the external network connection, making the user unable to visit the anti-virus software upgrade website after the virus is discovered, and unable to obtain the latest virus signature database or Designed to kill tools to stop the destruction and spread of viruses. Or because of the shock wave virus, exploiting Windows system vulnerabilities to attack and destroy the RPC service process, causing the user's computer to be forcibly shut down after 60 seconds after it is turned on, making the computer unusable. Or the five-drug insect virus, when infe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com