System for synthetical analyzing and monitoring safety of information on network
A comprehensive analysis and information security technology, which is applied in the field of online information security comprehensive analysis and monitoring system, can solve the problems of single filtering algorithm, affecting the filtering speed, and unsatisfactory effect, so as to improve system processing efficiency, reduce workload, and run good effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
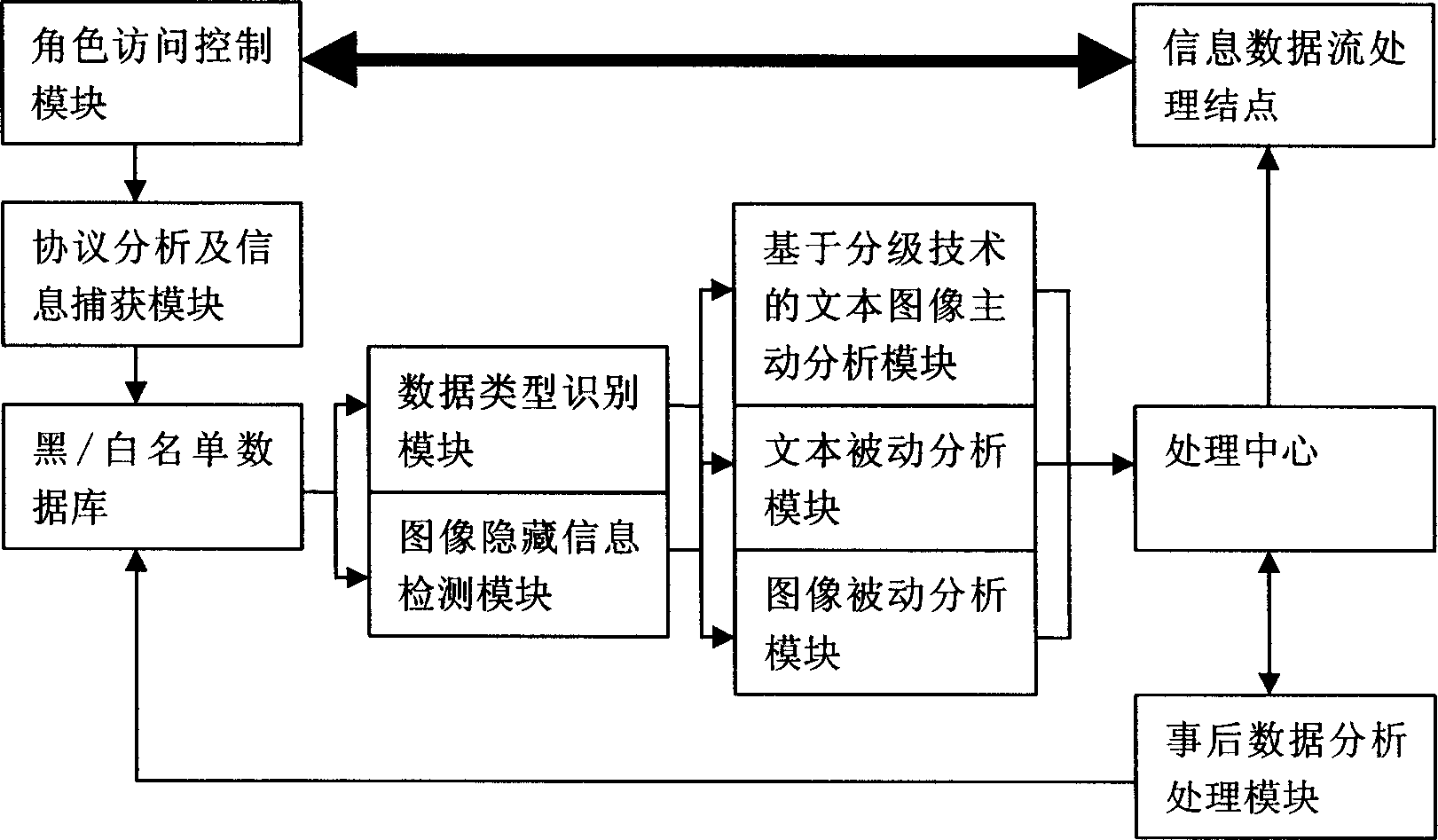
[0020] like figure 1As shown, the present invention includes: information data flow processing node, role access control module, protocol analysis and information capture module, black / white list database, data type identification module, text passive analysis module, image passive analysis module, processing center, Image hidden information detection module, text image active analysis module based on classification technology, post-event data analysis and processing module, the information to be processed first passes through the information data flow processing node, and the information data flow processing node forwards it to the role access control module, The role access control module checks whether the identification information comes from a controlled information source and sends it to the protocol analysis and information capture module. The protocol analysis and information capture module extracts the content of the information subject from the information and forward...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com