System and method for globally and securely accessing unified information in a computer network
a global and secure access technology, applied in the field of computer networks, can solve the problems of affecting the integrity and confidentiality of downloaded data, affecting the quality of downloaded data, and consuming a lot of time to download large files and programs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
first embodiment
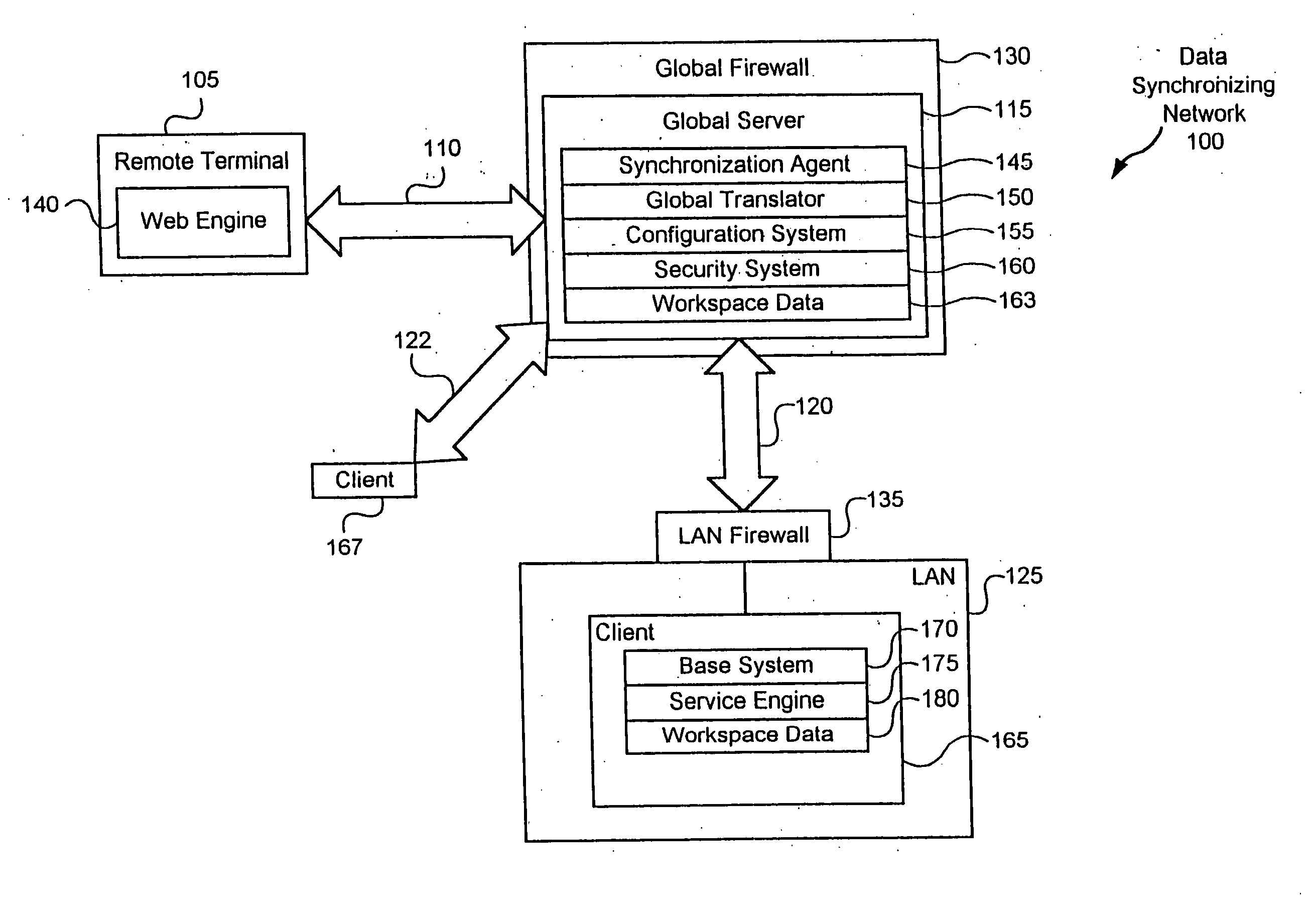
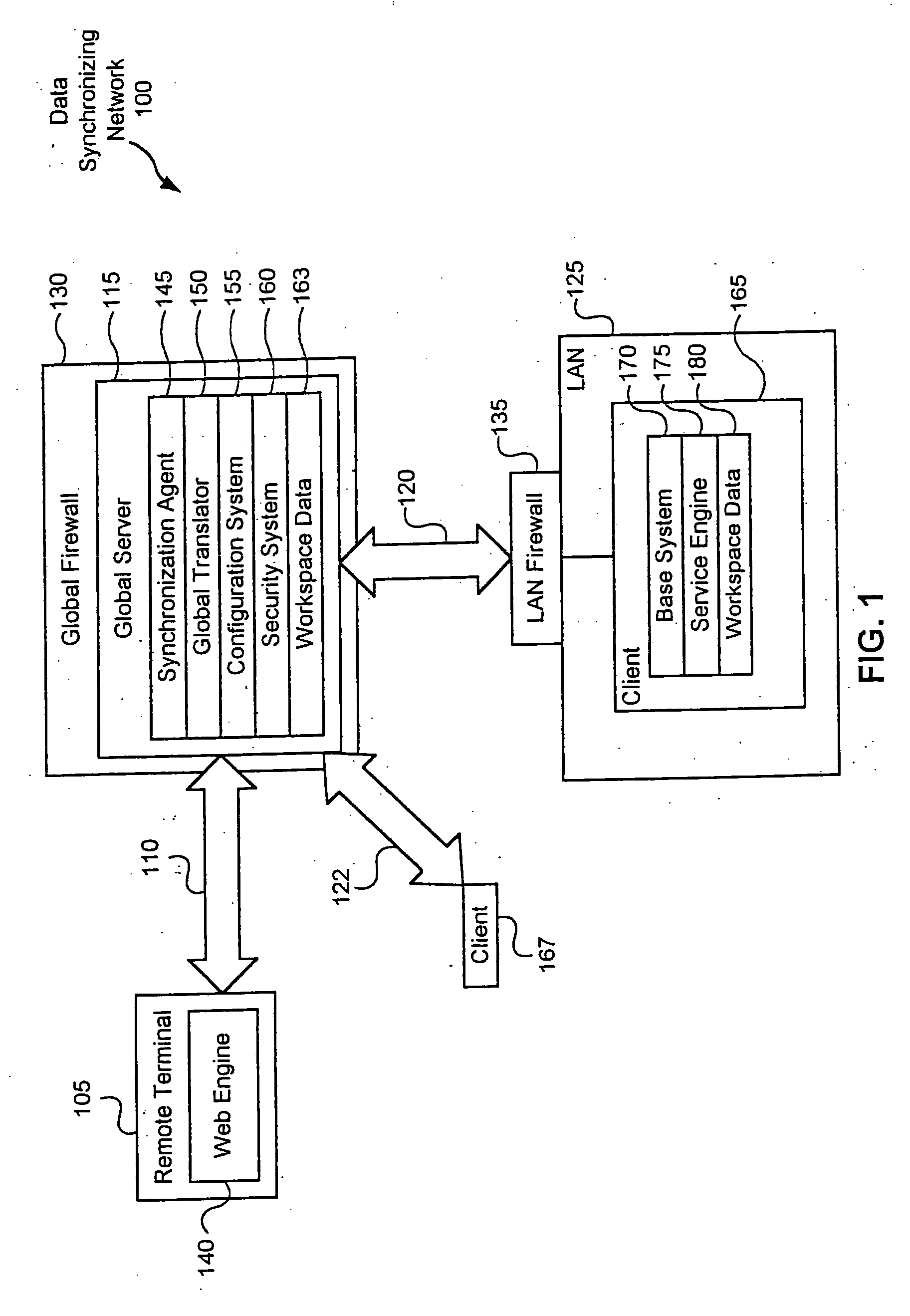
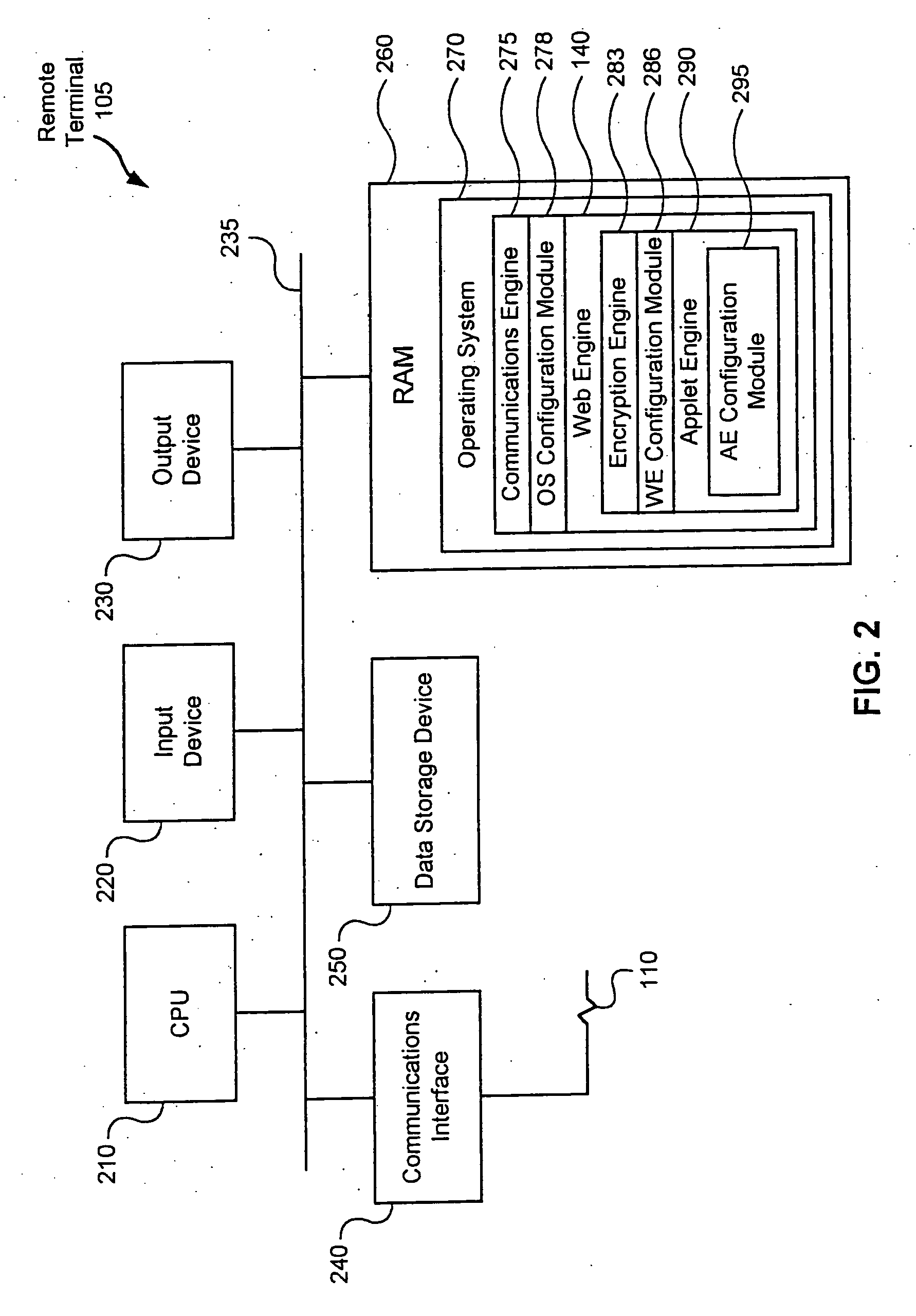
[0076]FIG. 12 is a flowchart illustrating details of step 1050 in a first embodiment, referred to as step 1050a, wherein the global server 115 provides the remote terminal 105 with a direct connection to a service 615. Step 1050a begins by the applet engine 290 in step 1205 running a configuration applet 359 for the selected service 615 that retrieves the service address 620 from data storage device 380 and the authentication information from the keysafe 365. The communications interface 340 in step 1210 creates a direct and secure connection with the communications interface 340 of the global server 115 at the retrieved service address 620, and uses the authentication information to authenticate itself. The applet in step 1215 acts as the I / O interface with the service 615. Step 1050a then ends.
second embodiment
[0077]FIG. 13 is a flowchart illustrating details of step 1050 in a second embodiment, referred to as step 1050b, wherein the global server 115 acts for the remote terminal 105 as a proxy to the service 615. Step 1050b begins with a configuration applet 359 in step 1305 requesting the service address 620 for the selected service 615, which results in retrieving the service address 620 directing the applet 359 to the global server 115. The applet 359 in step 1310 creates a connection with communications interface 340 of the global server 115. The global server 115 in step 1315 retrieves the service address 620 of the selected service 615 and the authentication information for the selected service 615 from the keysafe 365. The communications interface 340 of the global server 115 in step 1320 negotiates secure channel parameters for creating a secure channel with the service server 1014. The communications interface 340 in step 1320 also authenticates itself as the user.
[0078] Thereaf...
third embodiment
[0079]FIG. 14 is a flowchart illustrating details of step 1050 in a third embodiment, referred to as step 1050c, wherein the service 615 being requested is located on the global server 115. Step 1050 begins with an applet in step 1405 retrieving the service address 620 for the selected service 615, which results in providing the configuration applet 359 with the service address 620 of the service 615 on the global server 115. Thus, the applet in step 1410 creates a secure connection with the global server 115. No additional step of identification and authentication is needed since the remote terminal 105 has already identified and authenticated itself to the global server 115 as described with reference to step 1010 of FIG. 10.
[0080] In step 1415, a determination is made whether the service 615 is currently running. If so, then in step 1425 a determination is made whether the service 615 can handle multiple users. If so, then the global server 115 in step 1430 creates an instance fo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com