Method for multi-network guard end-to-end conversation cryptographic key negotiation of striding field
A session key and gatekeeper technology, applied to the public key and key distribution of secure communication, can solve the problem of no end-to-end key negotiation and exchange technology, no consideration of processing capacity, and difficulties in intercommunication communication security, etc. problems, to achieve the effect of increasing flexibility, preventing forgery, and simple layout
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
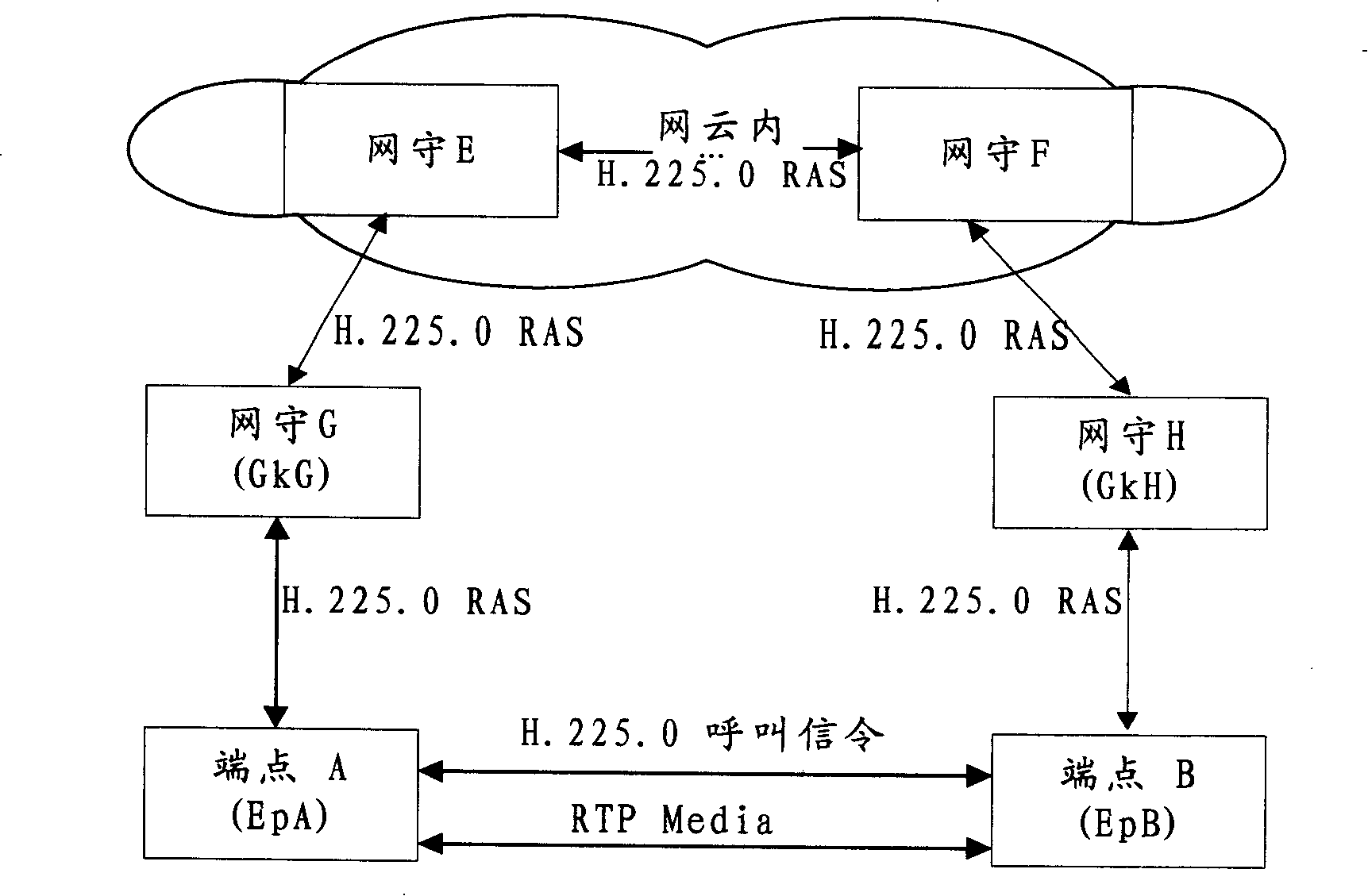
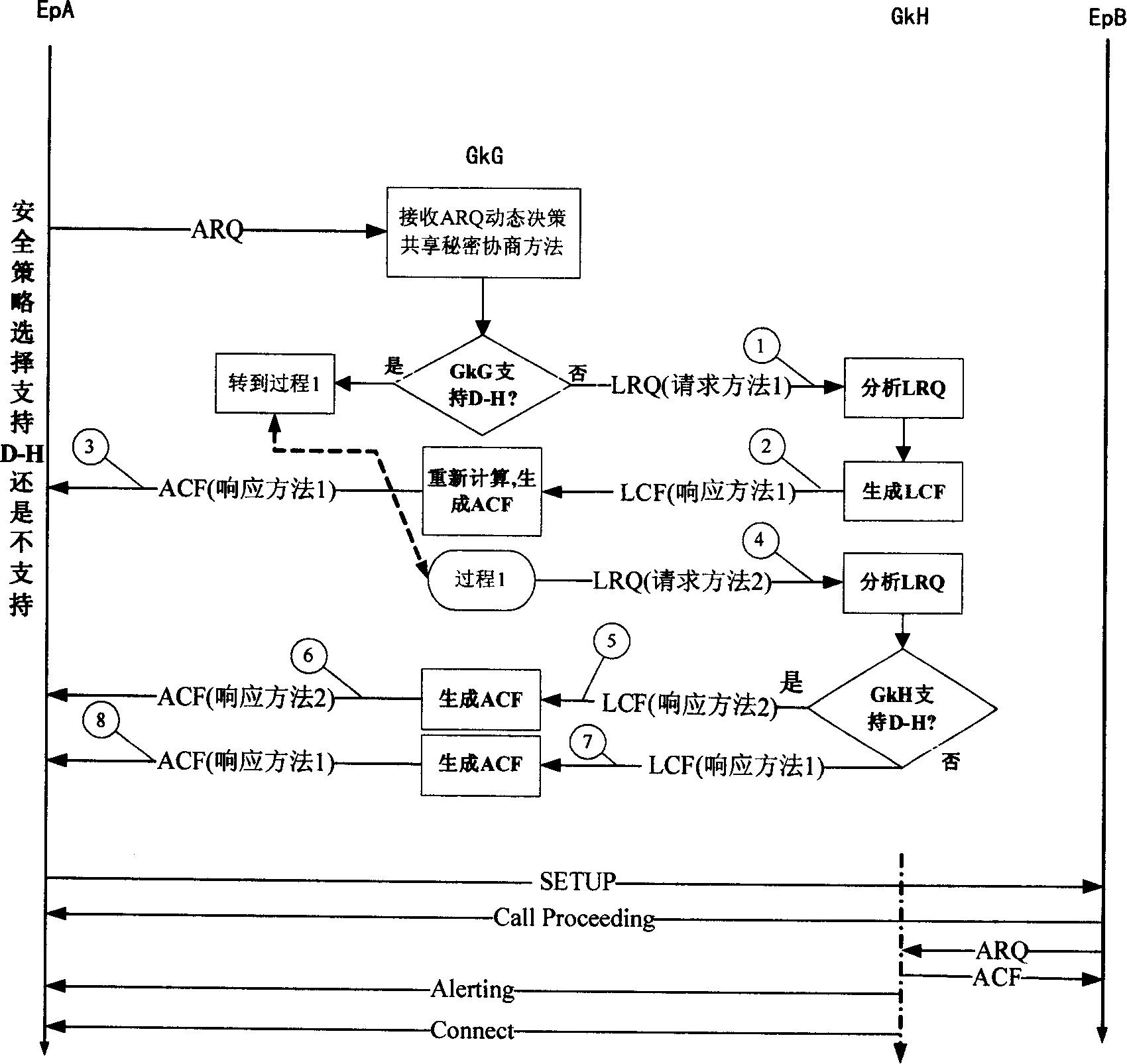
[0032] To illustrate the method of the present invention, the following symbols are referenced to represent endpoint and gatekeeper capabilities, or a combination of both, or to distinguish between calling / called endpoints maintaining a shared secret.
[0033] the symbol
Meaning
[0034] ″I0″
Indicates that the calling endpoint does not support D-H, and the calling or called gatekeeper does not support the D-H key exchange algorithm.
″I1″
Used in the independent ClearToken handed over to the calling endpoint, indicating that this ClearToken contains the shared secret.
″I2″
It is used in the independent ClearToken delivered to the called endpoint, indicating that this ClearToken contains the shared secret.
″I3″
Indicates that the calling endpoint does not support the D-H ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com