Network work communication security and secrecy system on basis of PKI (public key infrastructure) technology and method for implementing network work communication security and secrecy system
A safe, confidential and technical technology, applied in transmission systems, electrical components, etc., can solve problems such as easy to be modified, difficult to completely replace, lack of legal protection, etc., to achieve the effect of ensuring no loss, improving efficiency, and maintaining safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
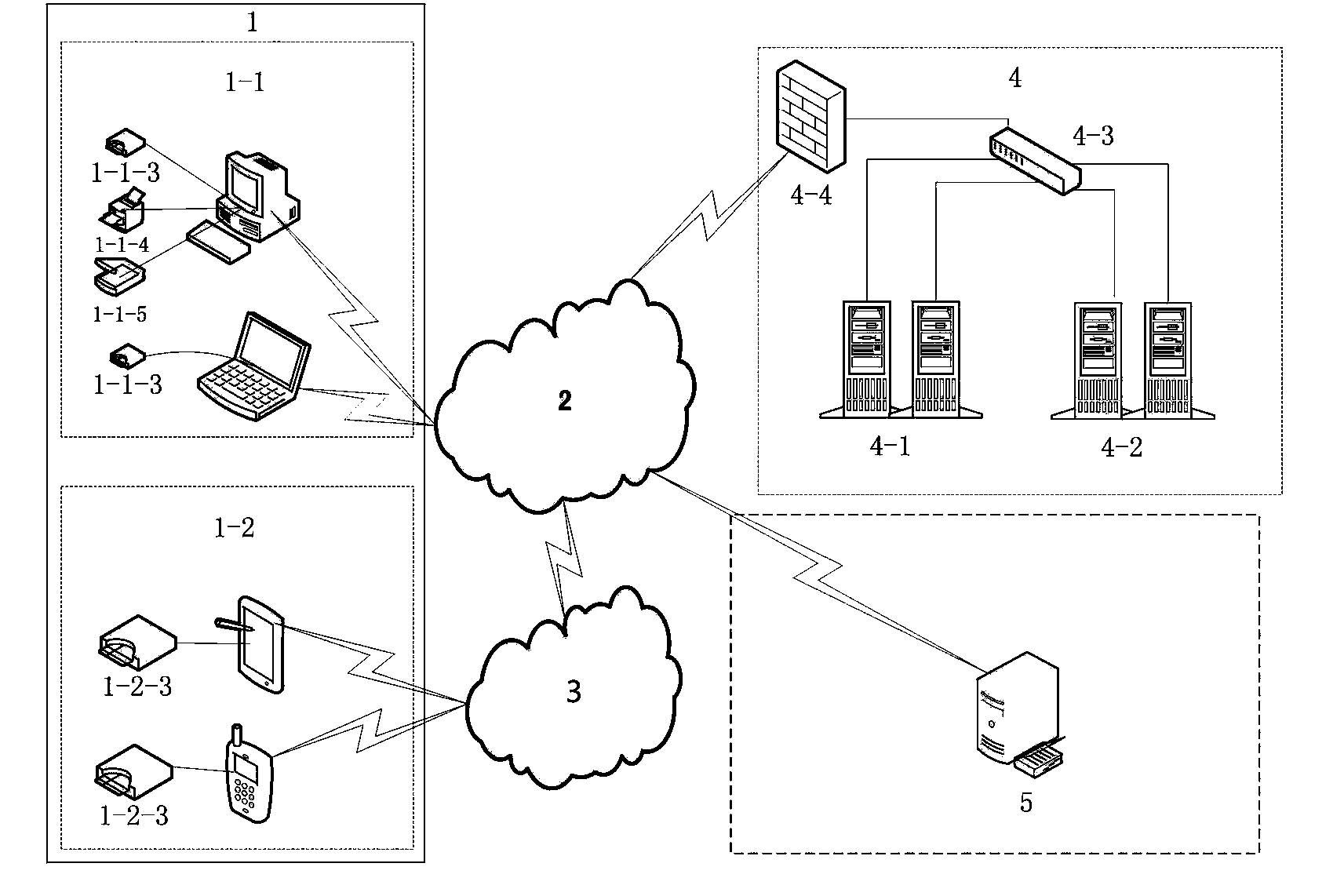
[0050] Embodiment 1 (the embodiment of the system of the present invention, see figure 1 ):
[0051] This embodiment includes a client, a server and a third-party CA organization directory server; the server end is connected to the client and the third-party CA organization directory server through the Internet respectively;
[0052] Described client is made up of PC client 1-1 and mobile client 1-2; Described PC client 1-1 is by the PC machine 1-1 that client smart card 1-1-3 and client software system are installed -1 and notebook computer 1-1-2, printer 1-1-4 and scanner 1-1-5;
[0053] Described mobile client 1-2 is made up of smart mobile phone 1-2-2 and panel computer 1-2-1 that mobile client smart card 1-2-3 and client software system are installed, and described smart mobile phone 1-2 -2 and the tablet computer 1-2-1 are connected to the Internet through a wireless communication network;
[0054] The client password module is respectively installed in the PC cli...
Embodiment 2
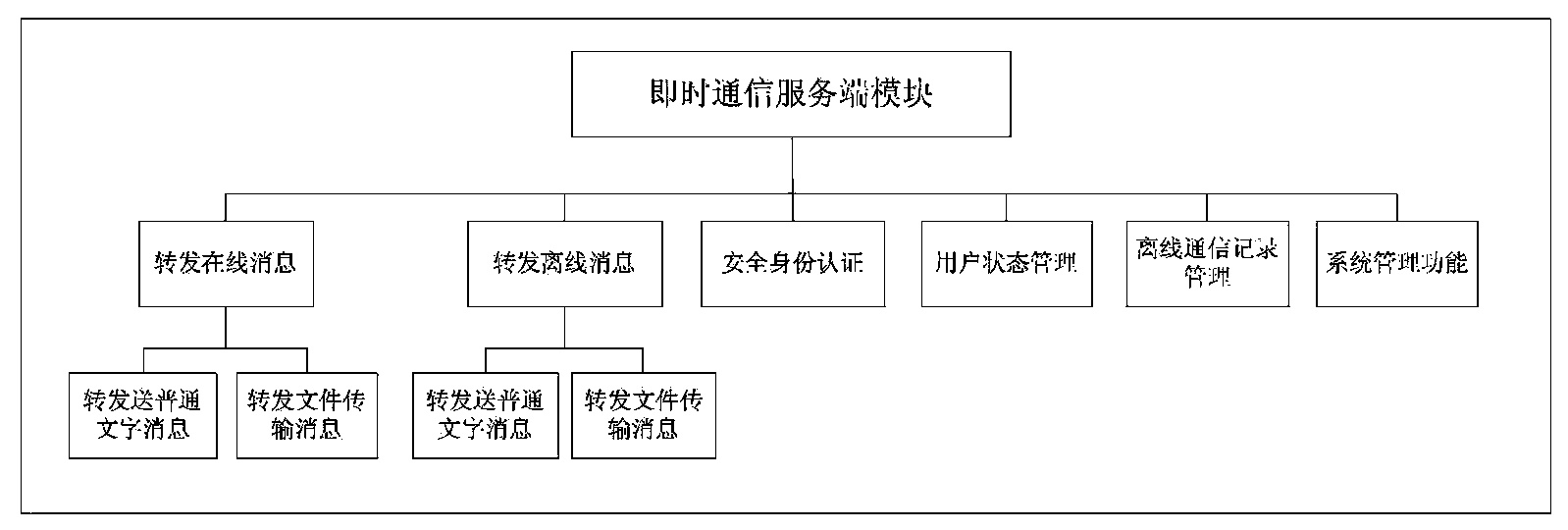
[0057] Embodiment 2 (the embodiment of method of the present invention, see Figure 1-10 ):
[0058] This embodiment is a method for realizing a PKI technology-based network work exchange security system, which is characterized in that the method is based on PKI technology and browser client / server communication technology, through the client software system and server software Realized by the interaction of the system;
[0059] The client software system includes a WEB client software module, a secure network disk client module, a client password module and an instant messaging client module;
[0060] Described WEB client software module comprises the version for IE, Firefox, Crome browser; This module calls client password module, provides identity authentication, data encryption and decryption, electronic signature, signature verification; This module operates scanner, supports single page Scanning and multi-page continuous scanning, adjust the angle of the scanned image;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com