Method and device suitable for security protection and security audit of various DCS production control systems
A technology of production control and security protection, applied in the field of computer software, digital signature, hardware and network communication, and information security, it can solve problems such as disallowed installation, centralized information security functions, lack of security audit and complete event traceability methods, etc. To achieve the effect of complete functions, convenient operation and friendly interface
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
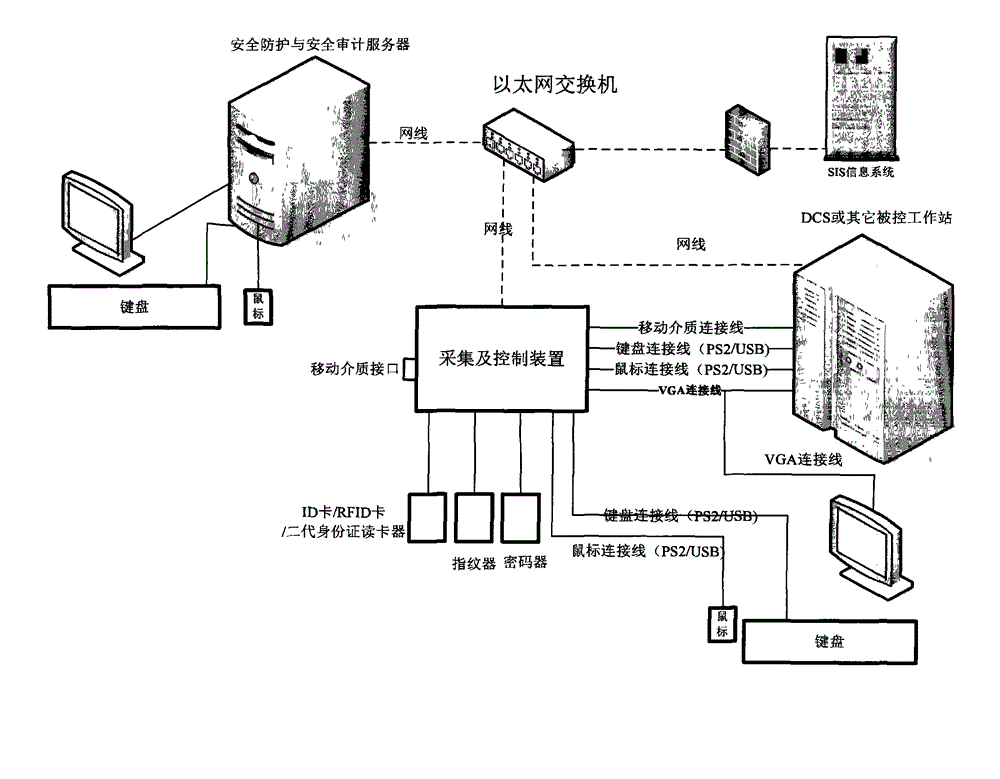
[0042] The specific implementation manners of the embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0043] Such as figure 1 Shown is a schematic diagram of the implementation of the system (including software and hardware) in the present invention.
[0044] System connection:
[0045] Connect the DCS keyboard and mouse to the device of the invention, and then connect the keyboard and mouse input of the DCS to the keyboard and mouse output of the device of the invention through the keyboard and mouse cable;
[0046] The VGA output of the DCS is divided into two by a VGA splitter, one is connected to the DCS display, and the other is connected to the device of the invention;
[0047] The USB of the DCS is connected to the device in the invention through a USB cable, or the Ethernet port of the DCS is connected to an Ethernet port in the invention;
[0048] ID cards, RFID cards, and ID card readers can be connect...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com