Internetwork data security sharing and management method and system
A data security and management system technology, applied in the field of data security sharing and management between networks, can solve the problems of not introducing the perspective of data life cycle, scattered data cross-domain sharing process, and non-safe use environment, so as to achieve small security risks, The effect of low management cost and low misjudgment rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
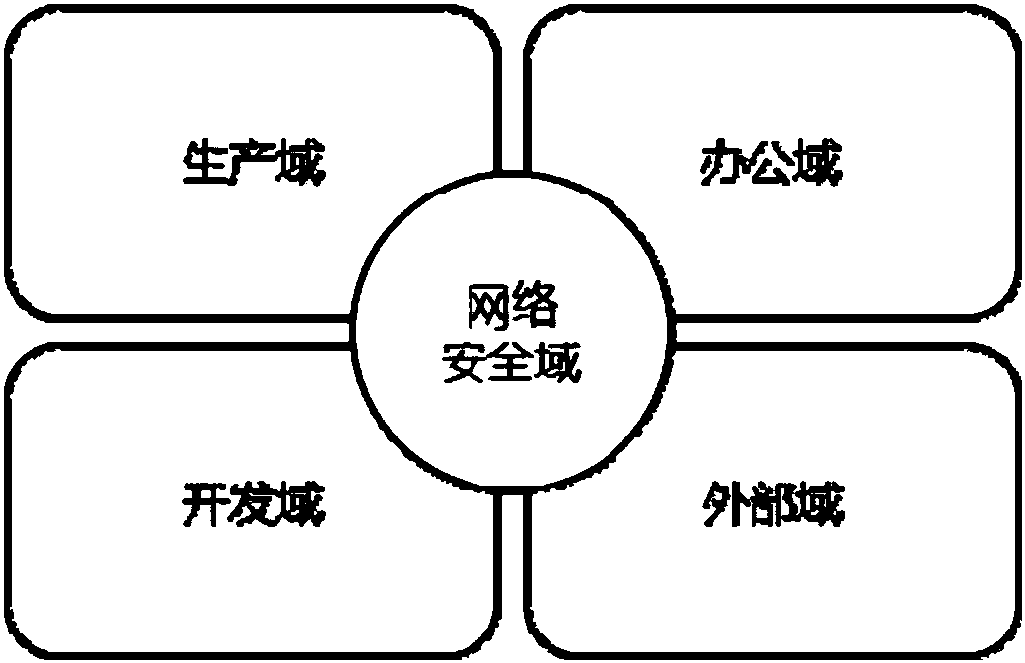
[0103] refer to Figure 4 , showing a schematic diagram of a method for data security sharing and management between networks, the method is applied to a data security sharing and management system between networks, wherein the core system belonging to the data management party can be deployed on the network where the data management party is located The core domain in the security domain. Other systems belonging to the data demander can be deployed in other domains in the network security domain where the data demander is located. Other domains are usually non-core domains in the network security domain where the data demander is located. For example, the data demander The office domain in the network security domain, etc., the data security sharing and management system between the networks can be deployed in the DMZ area between the core domain and other domains (demilitarized zone, also called demilitarized zone, different network security The buffer zone between domains. ...
Embodiment 2
[0150] refer to Figure 5 , shows a schematic diagram of a data security sharing and management method between financial institutions networks, the method is applied to the data security sharing and management system between financial institutions networks, wherein the production system belonging to a bank can be deployed in the bank The production domain in the network security domain where the bank is located. The production system can store head office data and branch data, etc. The office system belonging to the banking business department can be deployed in the office domain in the network security domain where the bank is located. The data security sharing and management system can be deployed in the DMZ area between the production domain and the office domain. The method specifically may include the following steps:
[0151] Step 501: In the management portal module, initialize system operating parameters and environment, and perform cross-domain approval rules, cross-do...
Embodiment 3
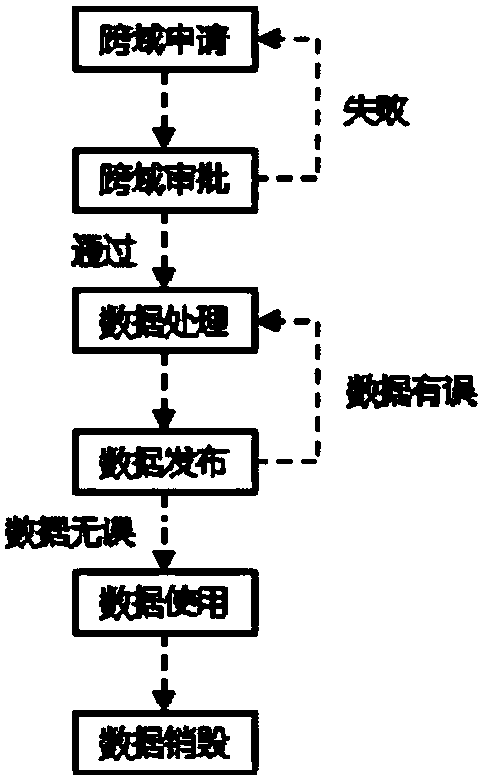
[0203] refer to Image 6 , shows a block diagram of an inter-network data security sharing and management system 600, the system includes a security process module 601, a security cross-domain sharing module 602, a security data storage module 603, a security data processing module 604 and a management portal module 605 ;
[0204] The security process module 601 is used for:
[0205] For cross-domain application, the data demander fills in the cross-domain sharing application form for the target data in the core domain according to its own business needs, and initiates a cross-domain sharing application request;
[0206] Cross-domain approval, the data management party approves the cross-domain sharing application work order submitted by the data requester according to specific cross-domain approval rules;
[0207] Cross-domain audit, record cross-domain application process information, cross-domain approval process information, and audit data across domains according to spe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com