Safety consistency control method for multi-agent system
A technology of multi-agent system and control method, applied in the direction of adaptive control, general control system, control/regulation system, etc., can solve the problems of increasing control cost, high connectivity, increasing deviation, etc. The effect of strong robustness and anti-interference
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0034] A security consistency control method for a multi-agent system in this embodiment may refer to the following steps:
[0035] Step 1: For any normal agent in the system that is performing state convergence, sort the sequences containing neighbor delay information and self information in ascending order at time t, and use the security domain of the system to preprocess it, that is, remove the sequences that are not in the sequence The state value of malicious nodes in the security domain is obtained after preprocessing.
[0036] Among them, the security domain refers to the range [m(0), M(0)] formed by the maximum value M(0) and the minimum value m(0) of the initial state of each normal agent in the multi-agent system; V o Represents a normal set of nodes.
[0037] Step 2: Calculate the mean of the new sequence and standard deviation Taking one standard deviation from the mean as the constraint condition, that is, using Judgment and elimination of malicious val...
Embodiment 2
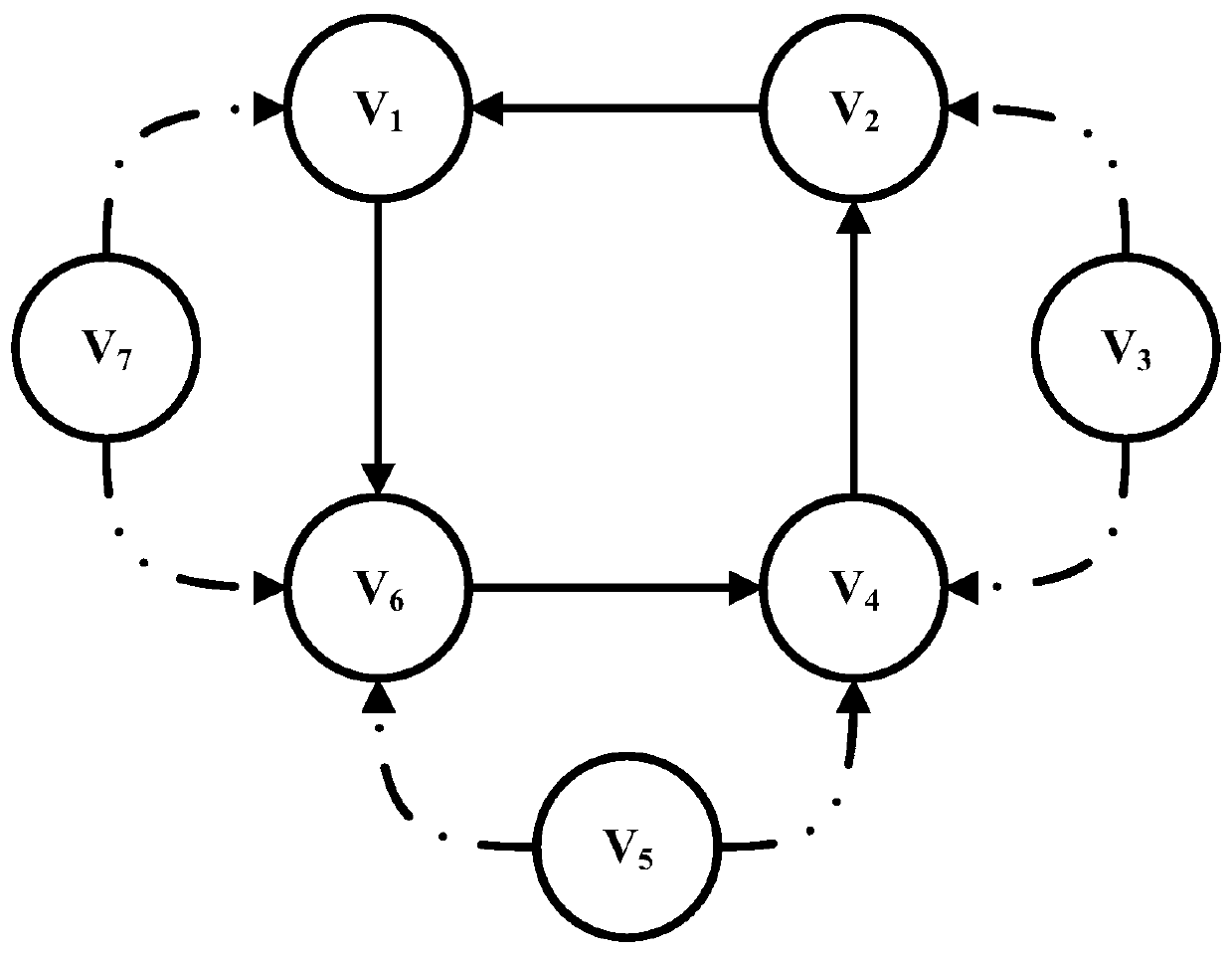
[0072] This embodiment takes figure 1 is the experimental topological graph, in which node V 1 , node V 2 , node V 4 and node V 6 is a normal node, node V 3 , node V 5 and node V 7 is a malicious node; the dotted line connecting a single point in the figure is the input edge between nodes at an odd moment, that is, V 7 to V 1 , V 3 to V 4 , V 5 to V 6 is the input edge between nodes at odd time; the dotted line connecting two points is the input edge between nodes at even time, that is, V 7 to V 6 , V 3 to V 2 , V 5 to V 4 is the input edge between nodes at even time; the solid line is the constant input edge, that is, V 6 to V 4 , V 4 to V 2 , V 2 to V 1 and V 1 to V 6 is a constant input edge. The communication step is set to 0.1s, and the delay upper bound T is set to 0.5s. The adjacency matrix A of the system is:
[0073]
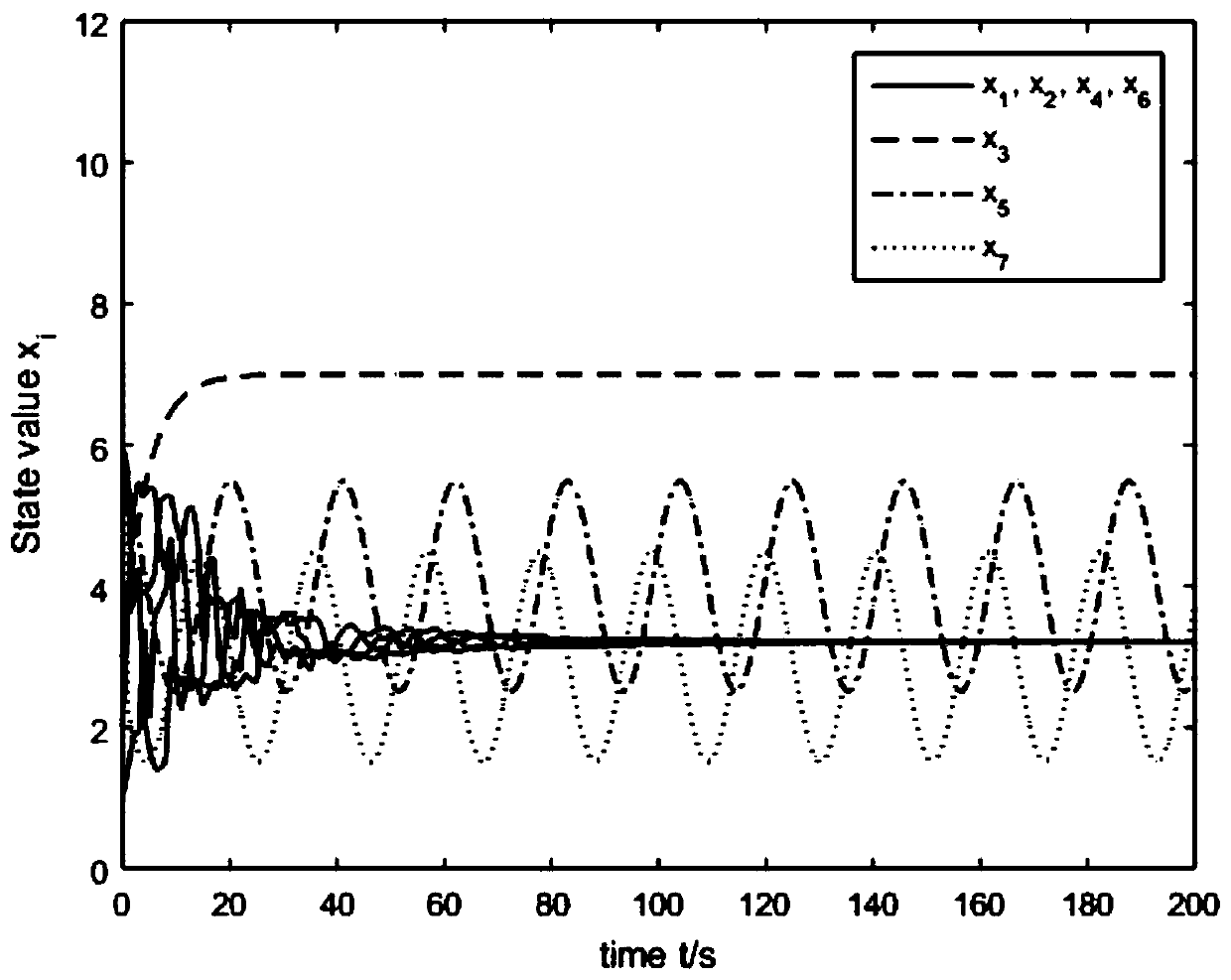
[0074] normal node V 1 V 2 V 4 and V 6 initial value of x 1 (0)=1,x 2 (0)=2,x 4 (0)=4,x 6 (0)=6; malicious node V ...
Embodiment 3
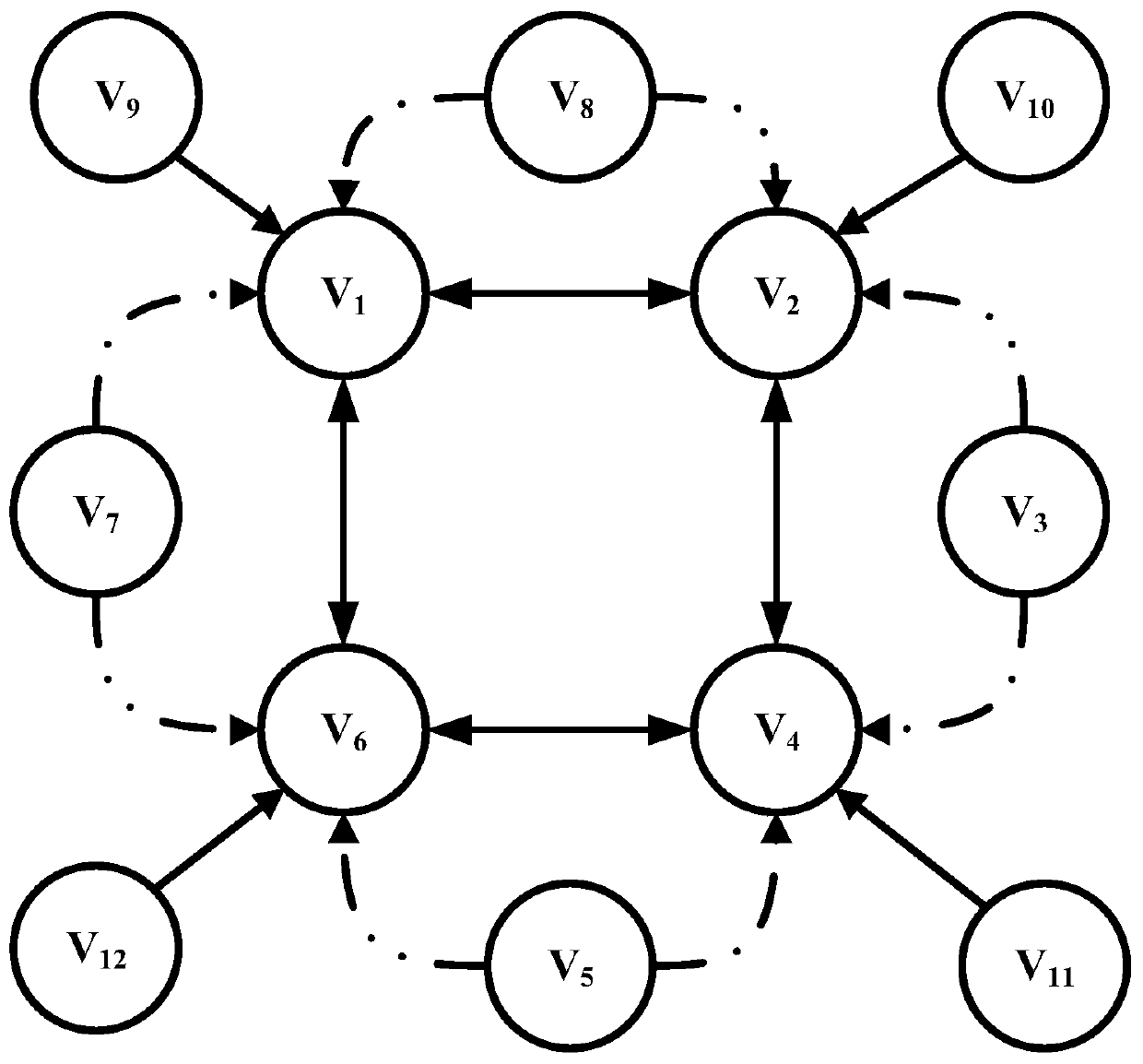
[0079] This embodiment takes figure 2 is the experimental topological graph, in which node V 1 , node V 2 , node V 4 and node V 6 is a normal node, node V 3 , V 5 , V 7 , V 8 , V 9 , V 10 , V 11 and V 12 is a malicious node; the dotted line connected by a single point in the figure is the input edge between nodes at odd times, the dotted line connected by double points is the input edge between nodes at even time, and the solid line is a constant input edge. The communication step length is set to 0.1s, and the upper bound T of the delay is set to 0.5s. The system adjacency matrix A is:
[0080]
[0081] normal node V 1 , V 2 , V 4 and V 6 initial state value x 1 ,x 2 ,x 4 ,x 6 They are as follows: x 1 (0)=1,x 2 (0)=2, x 4 (0)=4, x 6 (0)=6;
[0082] malicious node V 3 , V 5 , V 7 and V 8 The corresponding initial state value x 3 ,x 5 ,x 7 ,x 8 They are as follows: x 3 (0)=3, x 5 (0)=5, x 7 (0)=7,x 8 (0)=8;
[0083] malicious node V 9 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com