Dynamic hash table operation method based on hybrid DRAM-NVM memory
A DRAM-NVM, dynamic hash table technology, applied in the field of computer data storage, can solve the problem of high access delay, reduce access delay, optimize read and write performance, and reduce overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
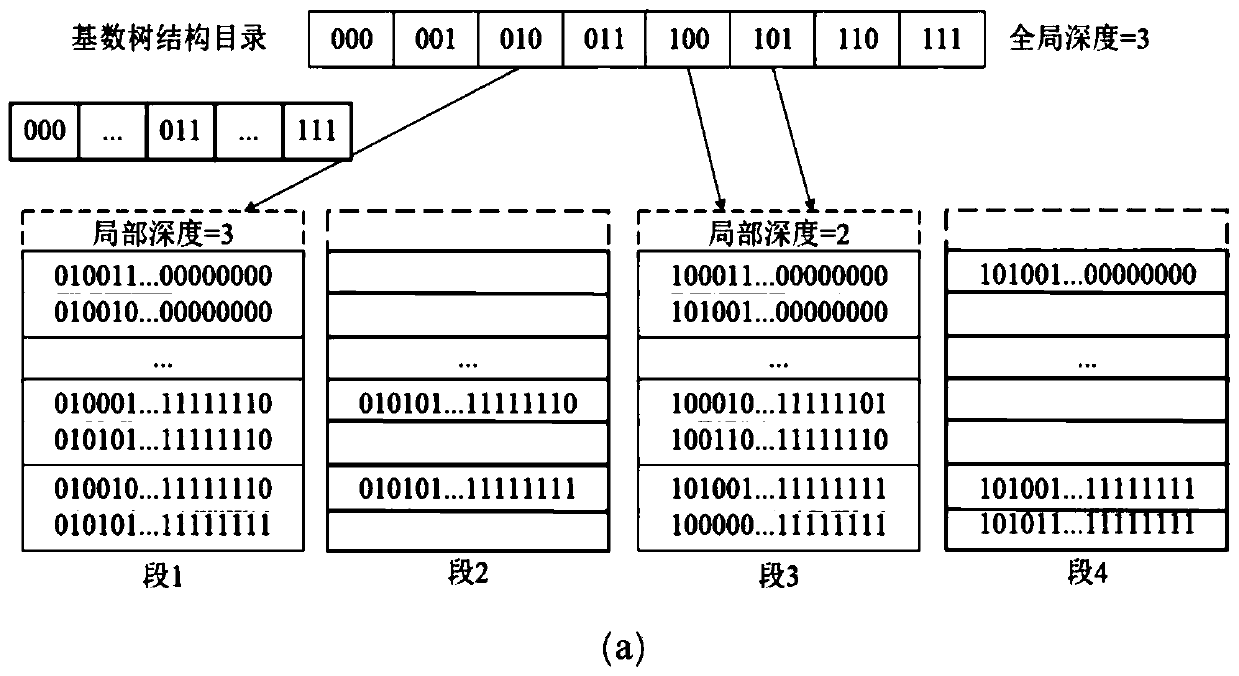
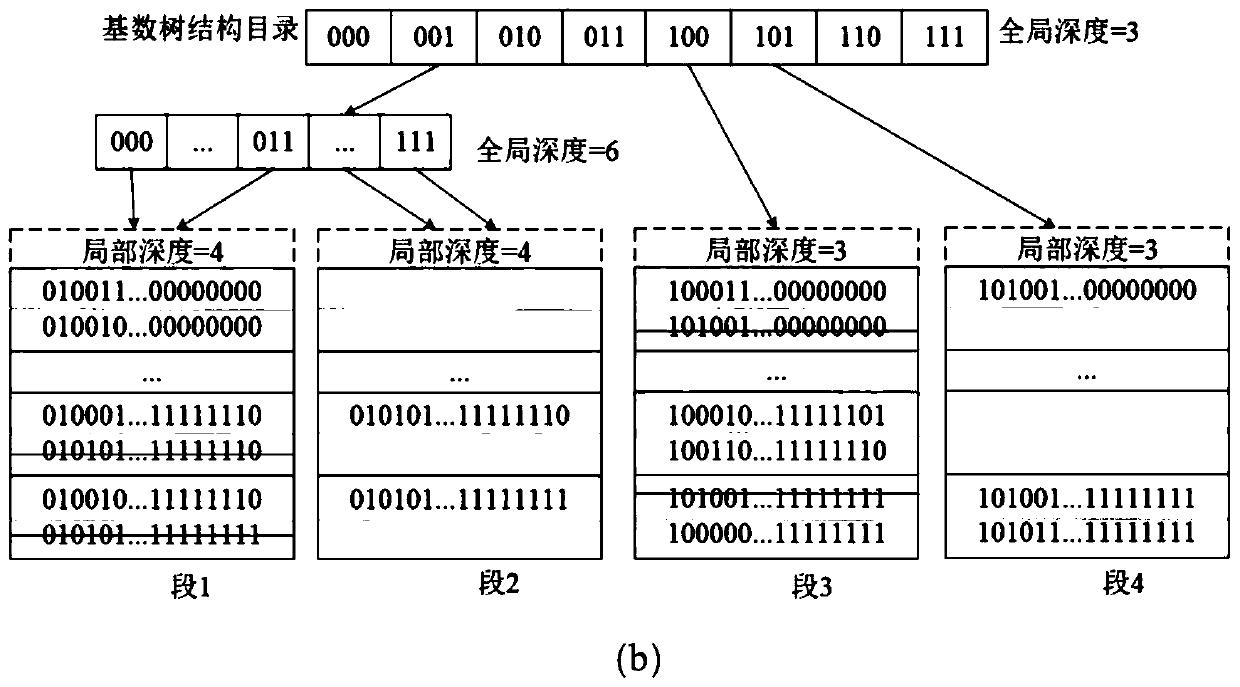
[0047] A segment split operation method based on the dynamic hash table of hybrid DRAM-NVM memory, such as figure 2 As shown, in this embodiment, n=256, and m can be any positive integer, and m is set to 0 for convenience of explanation; wherein, n represents the last n bits of the hash value, and m represents that the backup area occupies m buckets. Specifically, when the hash collision cannot be resolved, the capacity of the hash table needs to be expanded. There are two cases of segment splitting, among them, the first case, such as figure 2 As shown in section 3 in (a), if it is found that the local depth 2 of section 3 is less than the global depth 3 of the directory, it indicates that there is excess directory space. At this time, it is directly necessary to split the section and create a new section 4. Recalculate the hash values of all hash elements in segment 3, migrate the hash elements with hash value prefix 101 in segment 3 to segment 4, modify the segment add...
Embodiment 2
[0049] A kind of insertion operation method based on the dynamic hash table of mixed DRAM-NVM memory, comprises the following steps:
[0050] For the element to be inserted , where key represents the key value of the storage element, and value represents the value of the storage element;
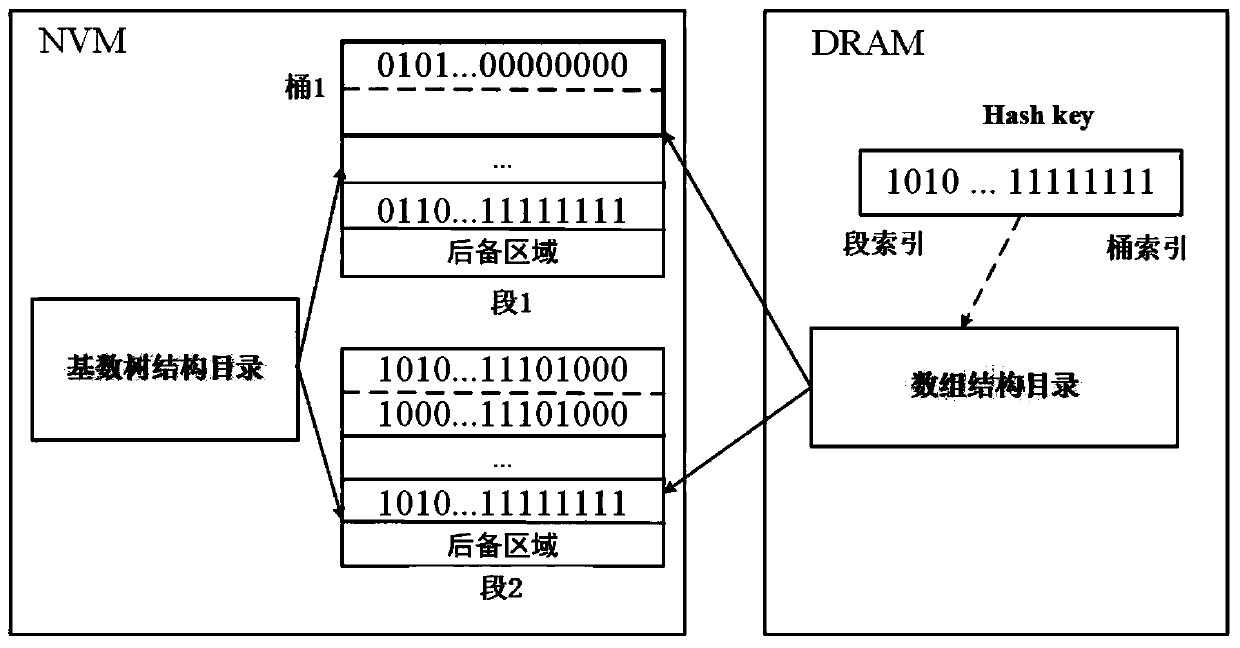
[0051] 2.1) For the element to be inserted, where key represents the key value of the storage element, and value represents the value of the storage element; the hash value of the key is calculated by the hash function, and the first k bits of the hash value correspond to Take out the segment address p1 from the array structure directory, and then obtain the corresponding bucket address p2 through the index of the last n digits of the hash value; where k and n are positive integers;
[0052] 2.2) Determine whether the hash unit in p1 is empty or whether the hash value of the key does not match the current index, if so, go to step 2.3), otherwise, go to step 2.4);
[0053] 2.3) Split the ke...
Embodiment 3
[0063] A kind of query operation method based on the dynamic hash table of mixed DRAM-NVM memory, comprises the following steps:
[0064] For the target element to be queried , where key represents the key value of the storage element, and value represents the value of the storage element; the segment address p1 and the bucket address p2 corresponding to the key of the target element to be queried are calculated through a hash function, Determine whether the current position is the target element, if so, return the value of the target element; otherwise, traverse the 4 consecutive buckets after p2 and the backup area p3 until the target element is found, and return its value, if there is still no value after traversing all the shared areas If the target element is found, the queried target element is not in the hash table.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com